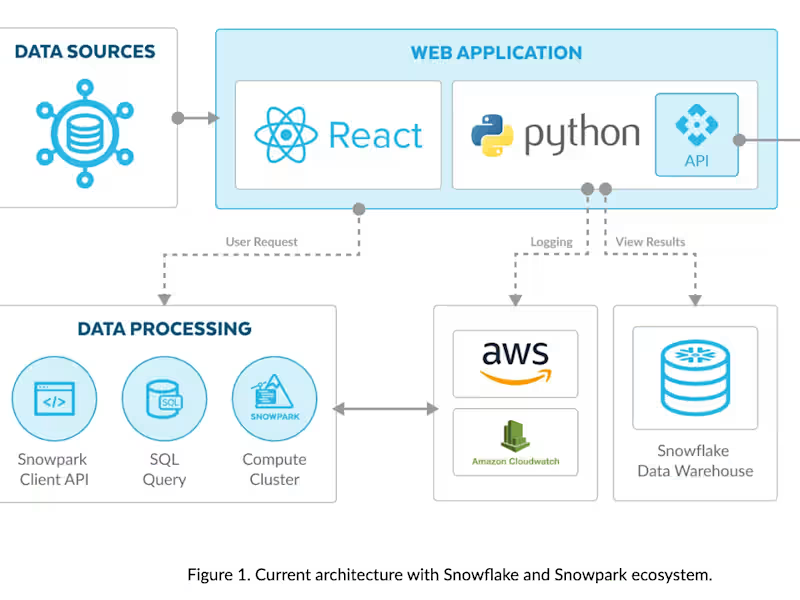
What skills should I look for when I hire a security engineer?
When you want to hire a security engineer, check if they know about network security, cryptography, and ethical hacking. They should understand firewalls, malware, and how to protect data. A good security engineer also knows how to test computer systems to find weaknesses.
How can I define clear project goals when hiring a freelance security engineer?
Explain what parts of your computer system or website need protection. Be clear about what you want the security engineer to test or build. Agree on a timeline for the project, so you know when each part will be done.
What important factors should I consider for a successful hire of a security engineer?
Look for a security engineer who understands your industry, like banking or healthcare. Think about their work method, if they provide regular updates, and their ability to solve problems. Make sure they fit well with your team and know your goals.
What is the best way to share my security needs with a freelance security engineer?
Write down a list of what needs to be secure, like your website or data. Use clear words and provide examples if you can. Discuss any specific security issues you've faced before, so they know what to expect.
How do I set clear expectations for the deliverables from a security engineer?
Create a checklist of all the things you need the security engineer to complete. Talk about the type of report you expect after their work. Make sure they know how you want problems fixed if they find any.
What should I include in our initial conversations before hiring?
Talk about the main goals of the security project and any deadlines. Discuss the tools they will use and if they need anything from you. Make sure you both agree on how to communicate, like by email or video call.
How do I assess if a security engineer is capable of handling my project's needs?
Look at their previous work to see if they’ve done similar projects. Ask them about how they’ve solved specific security issues in the past. Check if they are certified in security fields, as this shows they have special skills.
How do I ensure the project starts smoothly with a freelance security engineer?
Set up an initial meeting to go over the project's details and deadlines. Share any important documents or access they need to start work. Establish a routine for progress updates to keep the project on track.
What ways can I use to discuss sensitive information with a security engineer safely?
Use encrypted email or secure file-sharing tools when sending sensitive data. Explain any company rules about information security they should know. Always confirm the security engineer understands how to keep your data safe.
Why is it important to agree on a communication plan with my security engineer?
A clear communication plan helps avoid confusion and keeps the project on track. Decide how often you’ll have check-ins and how you’ll share updates. This makes it easier to address any issues quickly and keep everything running smoothly.
Who is Contra for?
Contra is designed for both freelancers (referred to as "independents") and clients. Freelancers can showcase their work, connect with clients, and manage projects commission-free. Clients can discover and hire top freelance talent for their projects.
What is the vision of Contra?
Contra aims to revolutionize the world of work by providing an all-in-one platform that empowers freelancers and clients to connect and collaborate seamlessly, eliminating traditional barriers and commission fees.