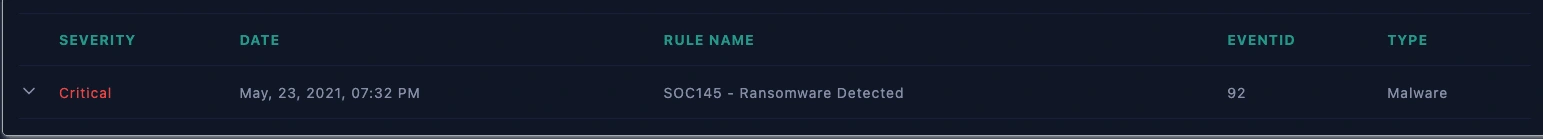
EventID: 92 - [SOC145 - Ransomware Detected]
SOC - LetsDefend.io
This is a report on what I have done training at the SOC Analyst Fundamentals course on letsdefend.io. Letsdefend.io is a good platform for blue team training.
Ransomware Detection Walkthrough.
SOC ANALYST REPORT
Incident Details:
Incident ID: EventID: 92 - [SOC145 - Ransomware Detected]
Date and Time of Detection: May, 23, 2021, 07:32 PM
Incident Severity: Critical
Incident Category: Malware
SIEM Alert
Summary:
The SIEM simulation detected a security event (EventID: 92 - [SOC145 - Ransomware Detected]) indicating the presence of a Ransomware Attack on host markPRD (172.16.17.88). The malware has successfully encrypted all files on the machine. The effected host has been contained and this case was escalated to tier 2. This report outlines the analysis, investigation, and mitigation steps taken.
Incident Description:
The alert which is EventID: 92 - [SOC145 - Ransomware Detected] triggered due to the detection USA attacker's IP (192.64.119.190 ) has attempted an Avaddon Ransomware attack on host markPRD (172.16.17.88 ). It was flagged as potentially malicious as the severity is Critical, warranting further investigation. Here's the full details on Avaddon Ransomware for reference.
Ransomware is basically a malware that encrypts all the victim's files and data on the effected machine making the victim limit the access to files and data on the machine. The attacker demands a ransom to restore the encrypted files. Note that there are ways to decrypt the affected files without paying ransom which is using a ransomware decryption tool and many more.
Investigation Steps:
Initial Triage:
Reviewed the SIEM alert dashboard for relevant details.
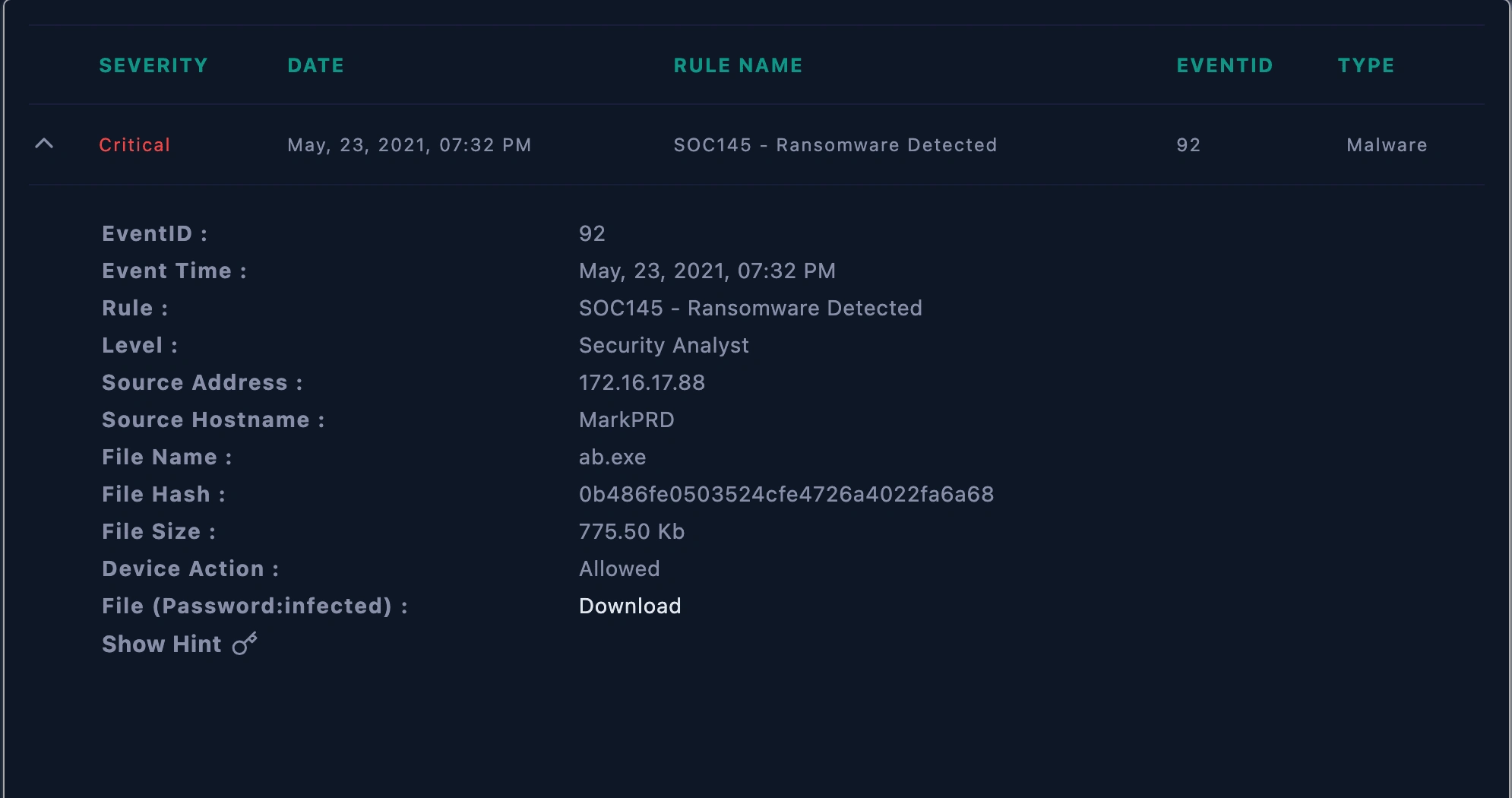
Alert details
Traffic Analysis:
Examined network traffic logs to identify the source and destination of the suspicious requested URL.
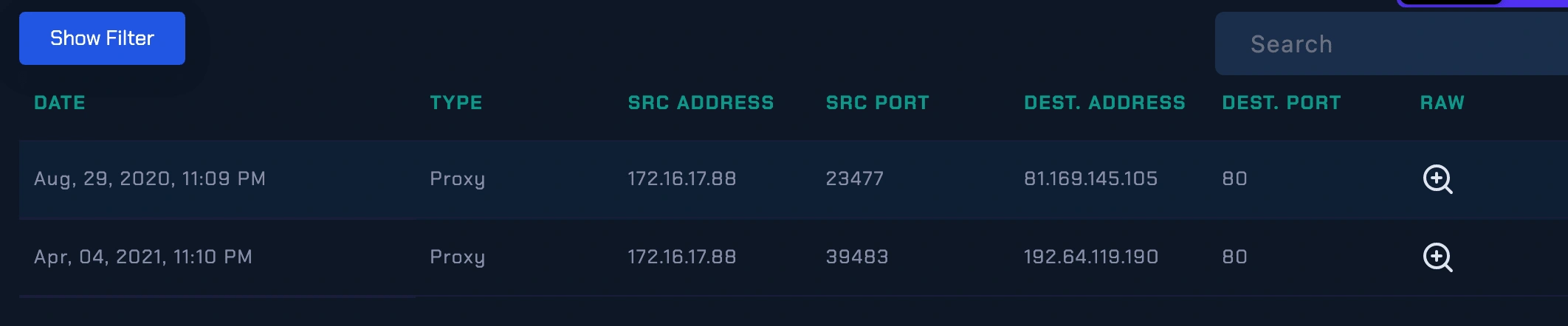
Log management
Those malicious IP addresses has communicate with markPRD (172.16.17.88) with through the following URL addresses;
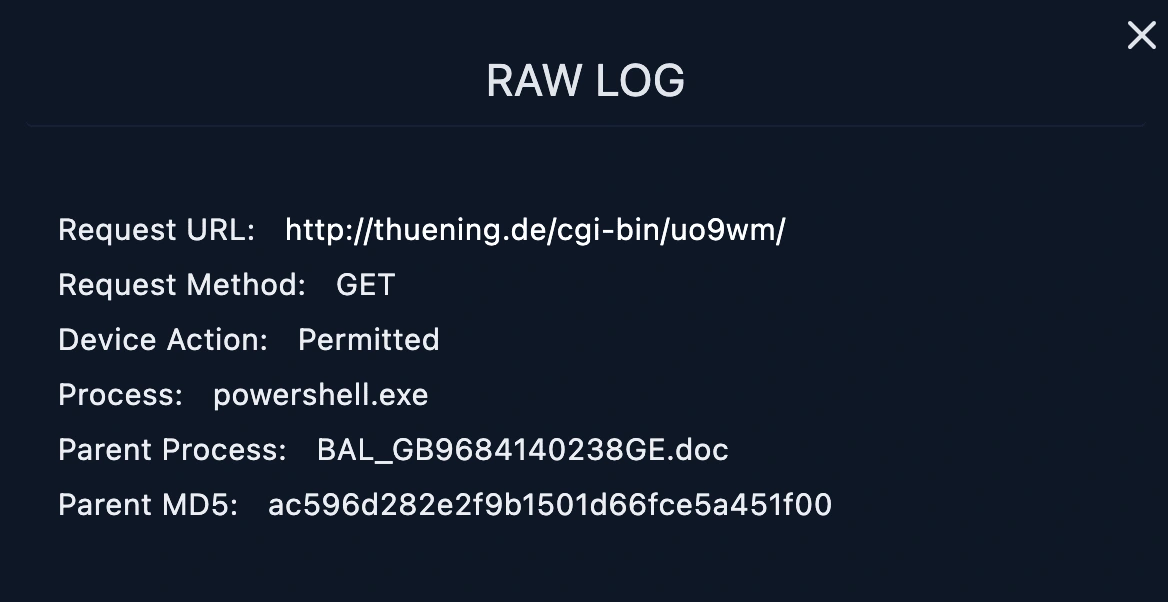
81.169.145.105 accessed
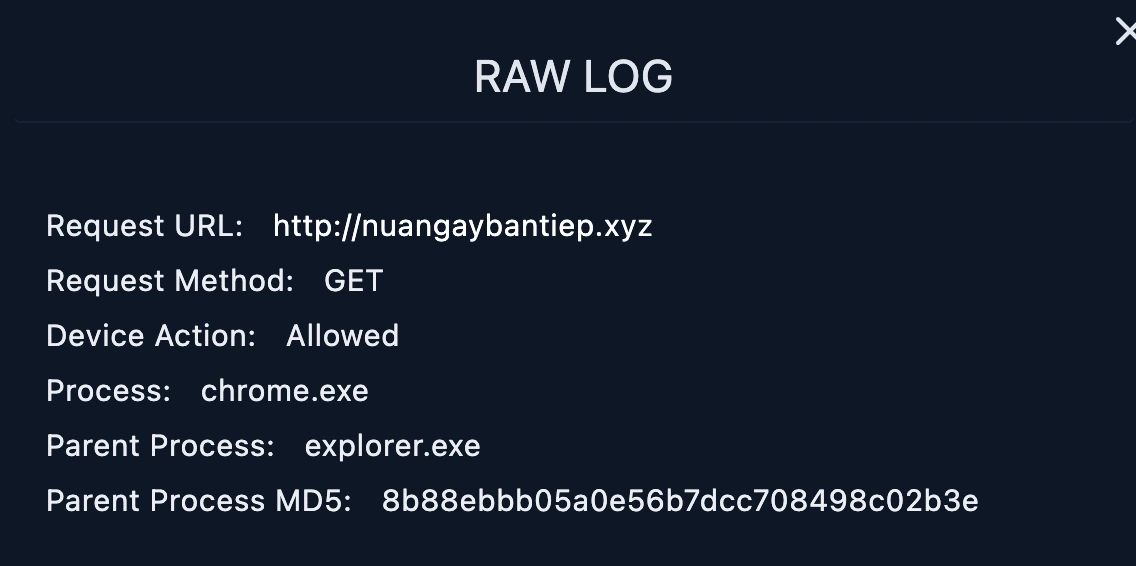
192.64.119.190 accessed
The use of “Log Management” to check if there is communication with a certain address and to see the details of this communication.
Logs are records of individual events or activities that occur within a system, and they often contain valuable information for troubleshooting, monitoring, and security purposes.
Malware Analysis:
Static Analysis
The header of file.
MD5 Hash : 0b486fe0503524cfe4726a4022fa6a68
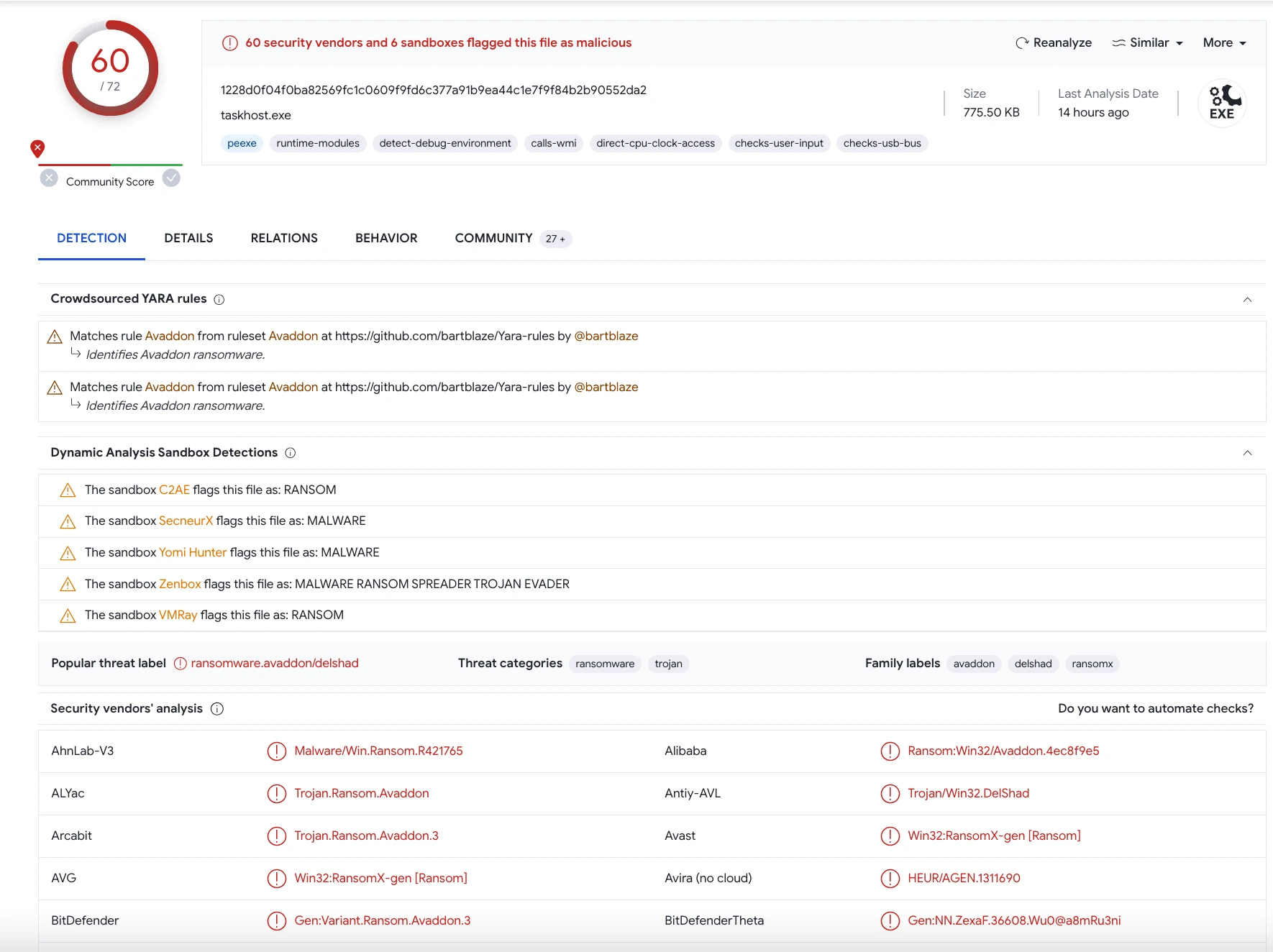
Hash file details on Virustotal
The 60 antivirus/security vendors and 6 sandboxes detected the hash file is malicious.
As we can see here it labels as ransomware.avaddon/delshad. It is a avaddon type ransomware as the many detections data above such as Crowdsourced YARA Rules and Dynamic Analysis Sandbox Detections conforms it.
On the community tab, many reports being shared by the community that says (MD5 Hash : 0b486fe0503524cfe4726a4022fa6a68) is a genuine malware turns out to be Avaddon Ransomware.
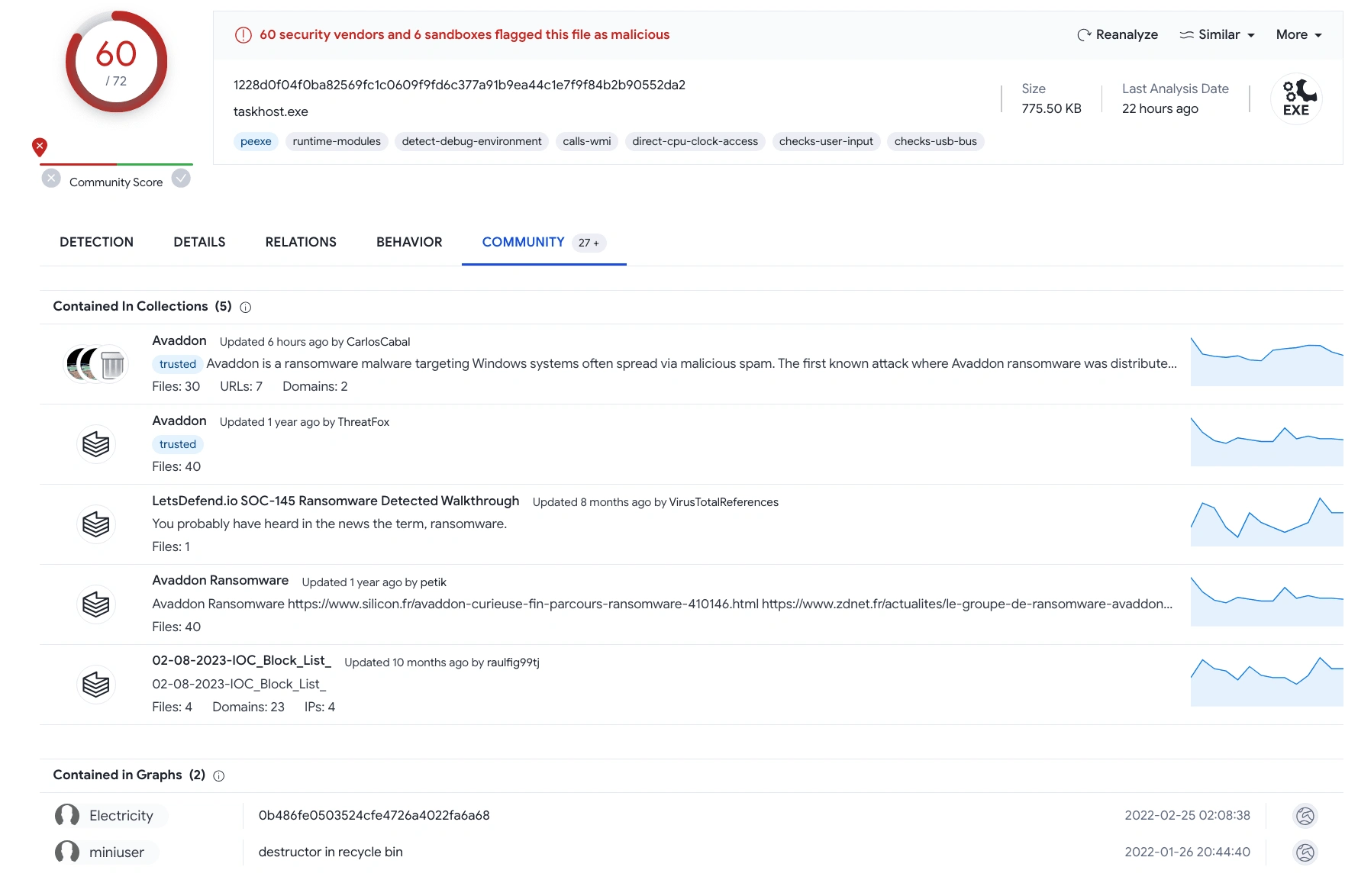
Community section on Virustotal
On the behavior section on VirusTotal it shows the type of process being executed as while the malware is running.
All of these processes were deleting shadow copies and and backup from victim's system. Note that Microsoft Windows machine can create backup and copies or snapshots of computer files when they are in use. It is implemented as a Windows service called the Volume Shadow Copy service.
This clearly shows positive for ransomware activity.
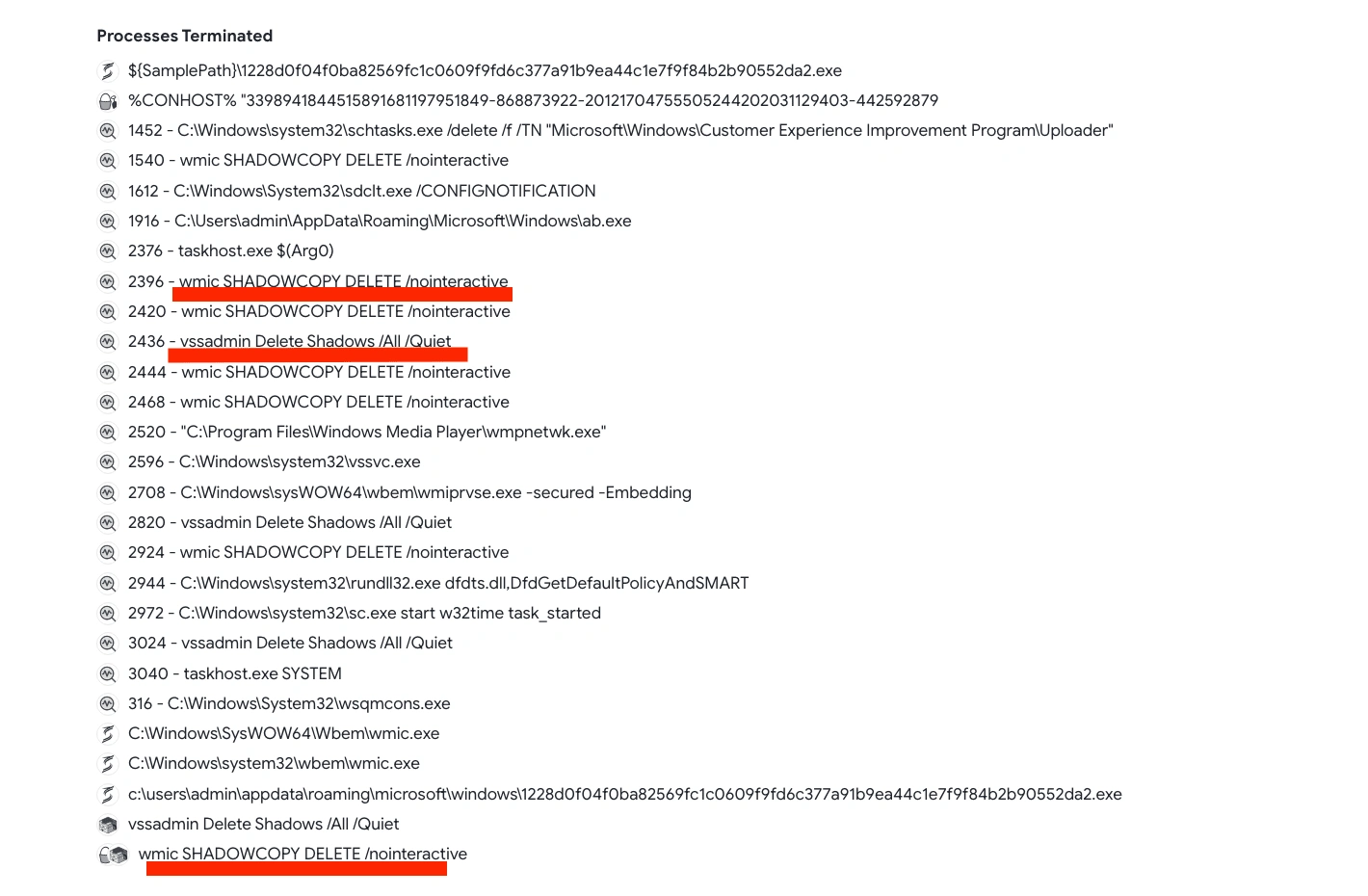
Behaviour tab on Virustotal
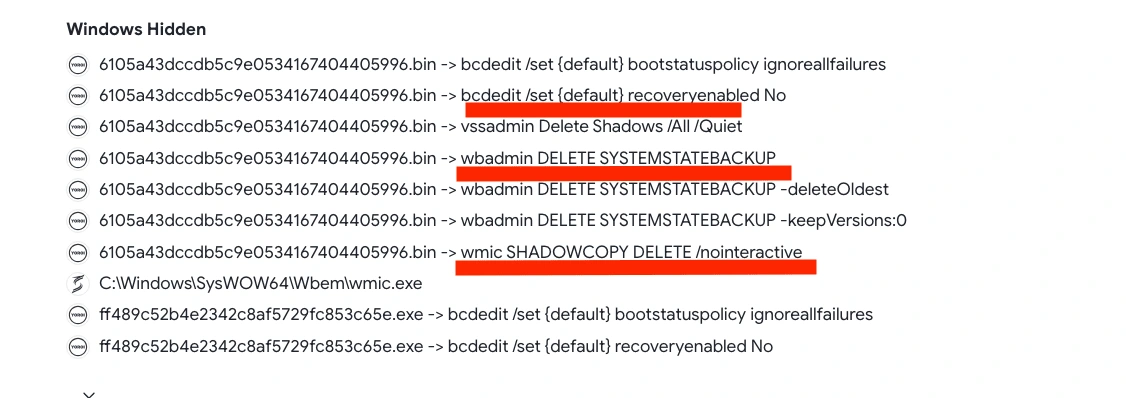
Behavior tab on Virustotal
All the following processes being executed on the markPRD's machine on the Endpoint Management.
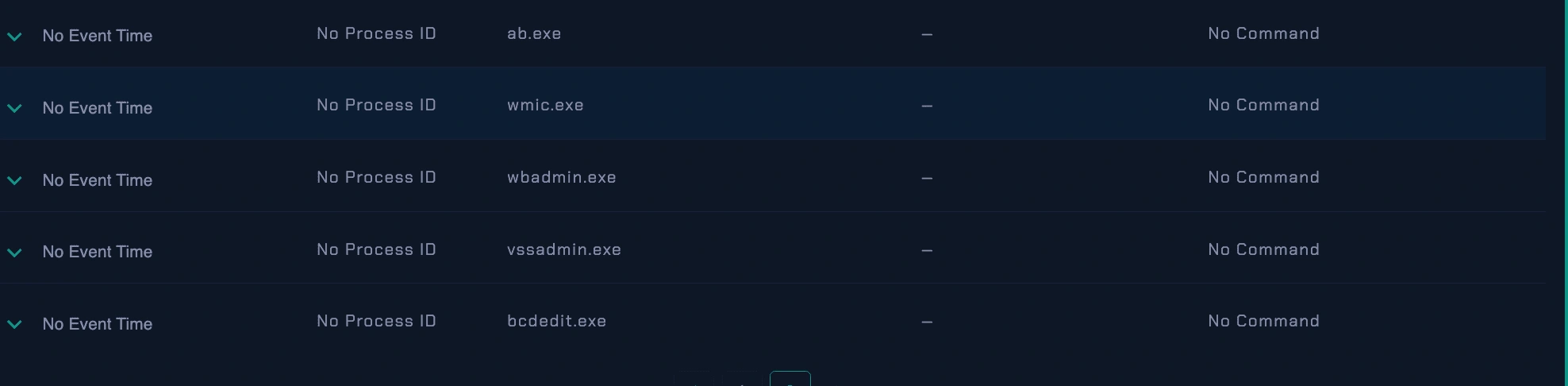
Process History
Dynamic Analysis
This was the first interface that shows files are starting to locked by itself.
Files are starting to locked by itself
All the related commands were starting to execute fast as we can see the command prompt below.
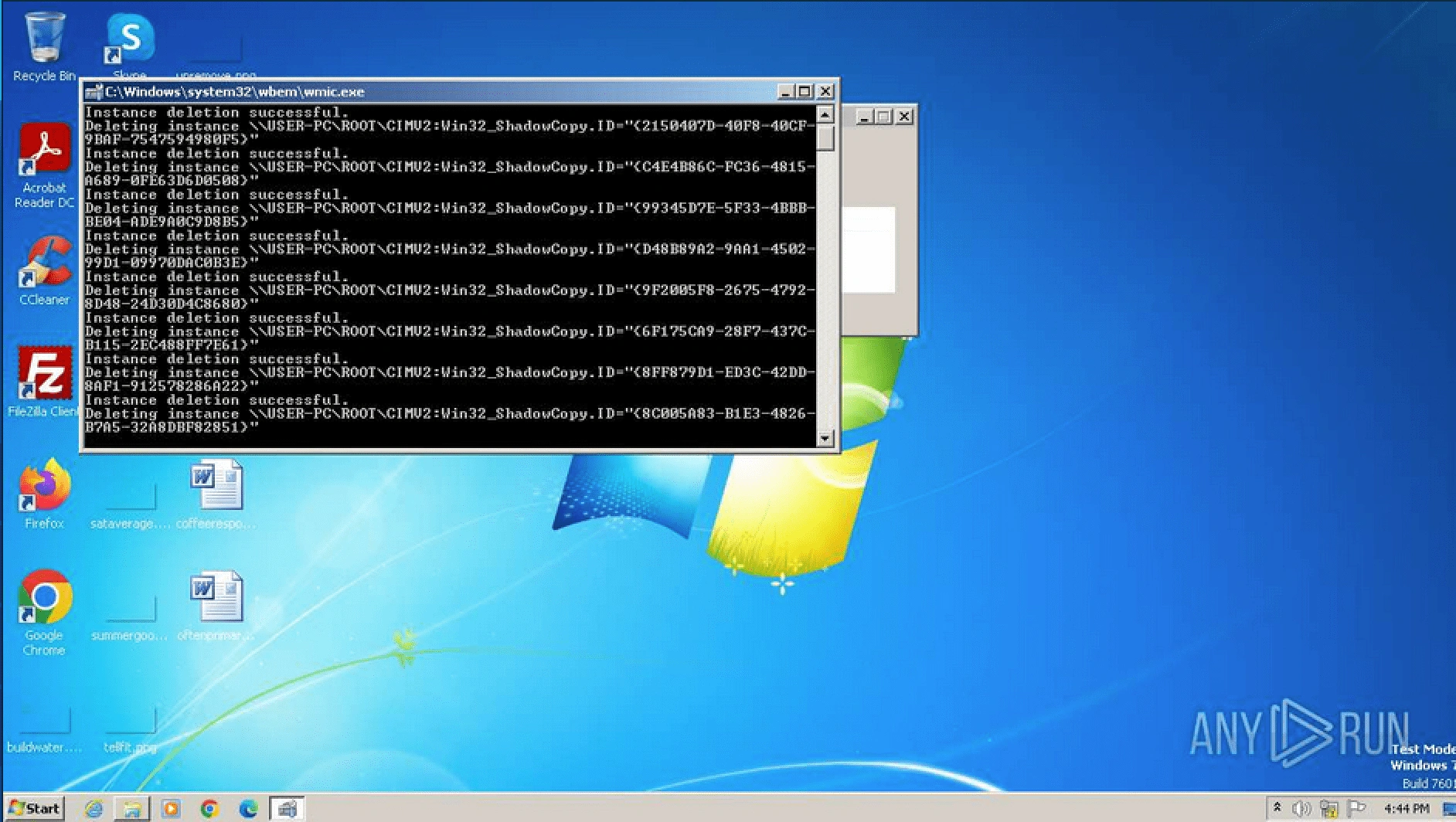
Commands executed
The malware has encrypted all the data and files.
All files are encrypted
Checking the file modification tab on ANYRUN.
The ab.bin.exe is executed then all the files are encrypted with unknown extension such as binary, etl.
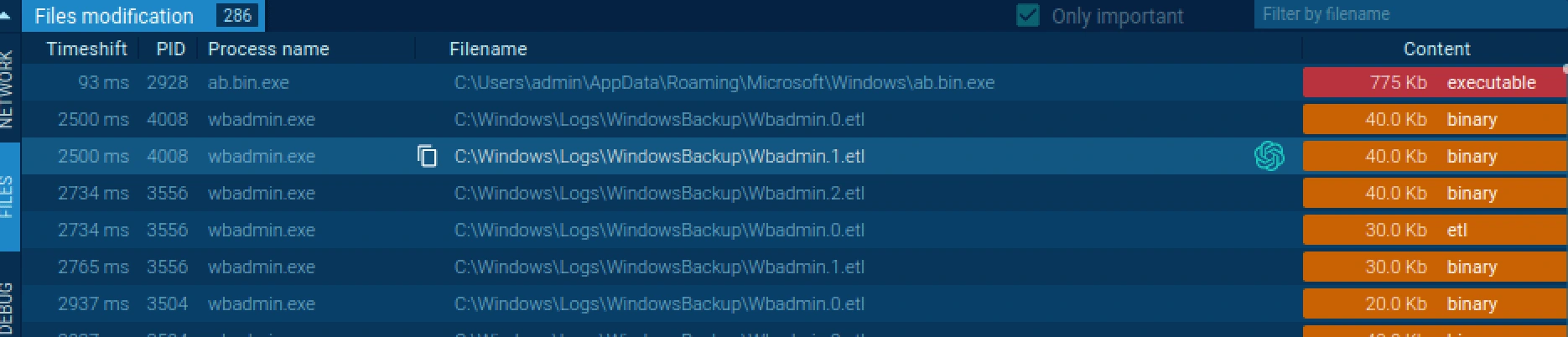
files modification tab
We found out that the attacker sends a ransom note as below;
-----=== Your network has been infected! ===-------
***************** DO NOT DELETE THIS FILE UNTIL ALL YOUR DATA HAVE BEEN RECOVERED *****************
All your documents, photos, databases and other important files have been encrypted and have the extension: .bDdbaEcaad
You are not able to decrypt it by yourself. But don't worry, we can help you to restore all your files!
The only way to restore your files is to buy our special software. Only we can give you this software and only we can restore your files!
We have also downloaded a lot of private data from your network.
If you do not contact as in a 3 days we will post information about your breach on our public news website (avaddongun7rngel.onion) and after 7 days the whole downloaded info.
You can get more information on our page, which is located in a Tor hidden network.
How to get to our page
--------------------------------------------------------------------------------
|
| 1. Download Tor browser - https://www.torproject.org/
|
| 2. Install Tor browser
| 3. Open link in Tor browser - avaddonbotrxmuyl.onion
| 4. Follow the instructions on this page
|
--------------------------------------------------------------------------------
Your ID:
--------------------------------------------------------------------------------
DO NOT TRY TO RECOVER FILES YOURSELF!
* DO NOT MODIFY ENCRYPTED FILES!
* * * OTHERWISE, YOU MAY LOSE ALL YOUR FILES FOREVER! * * *
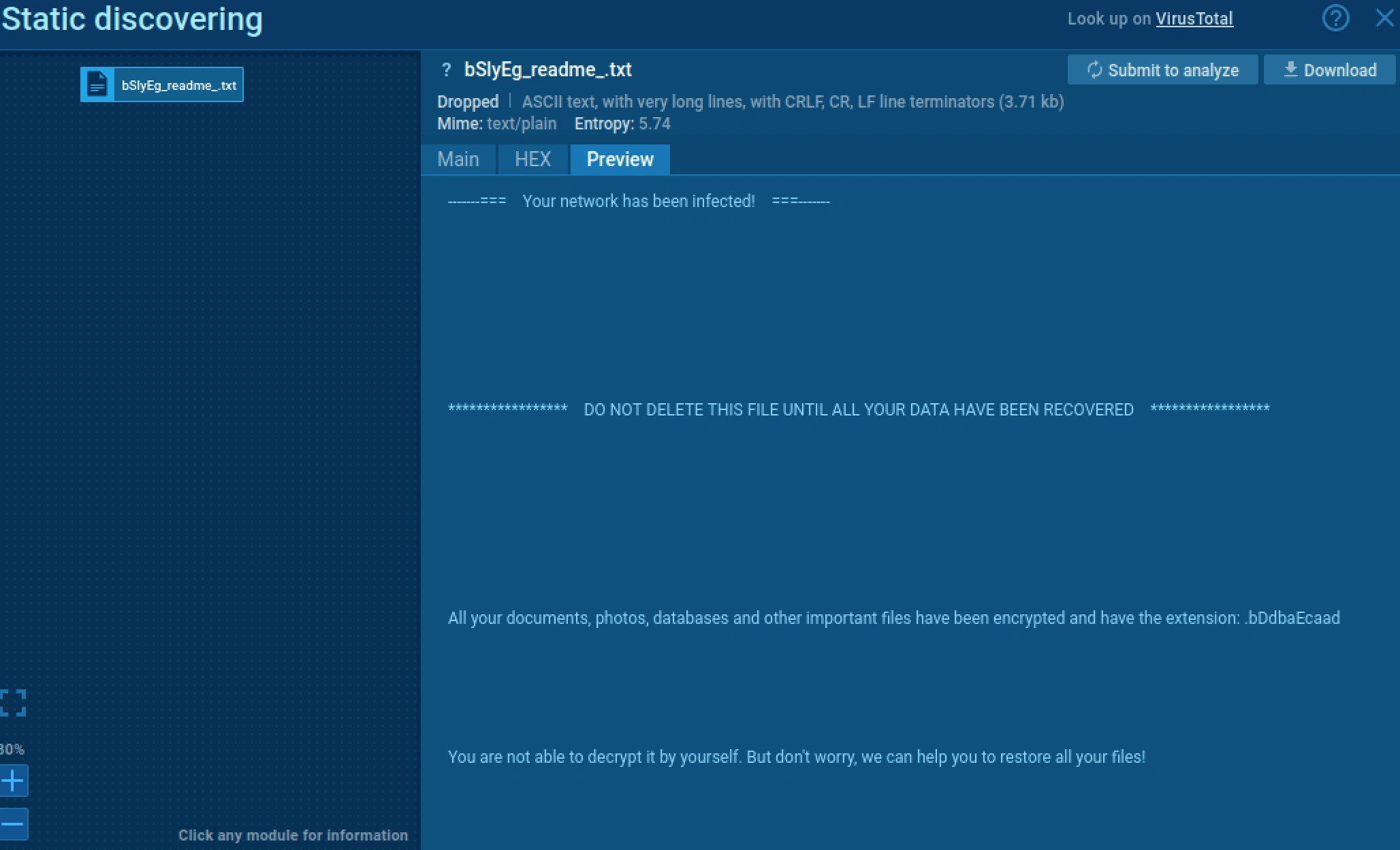
Note from attacker
This is a confirmation of ransomware attack, the threat actor provide an Onion URL.
Here are the full report for the dynamic analysis on any.run
Findings:
Ransomware Activity:
User Interaction:
Mitigation and Response:
Isolation:
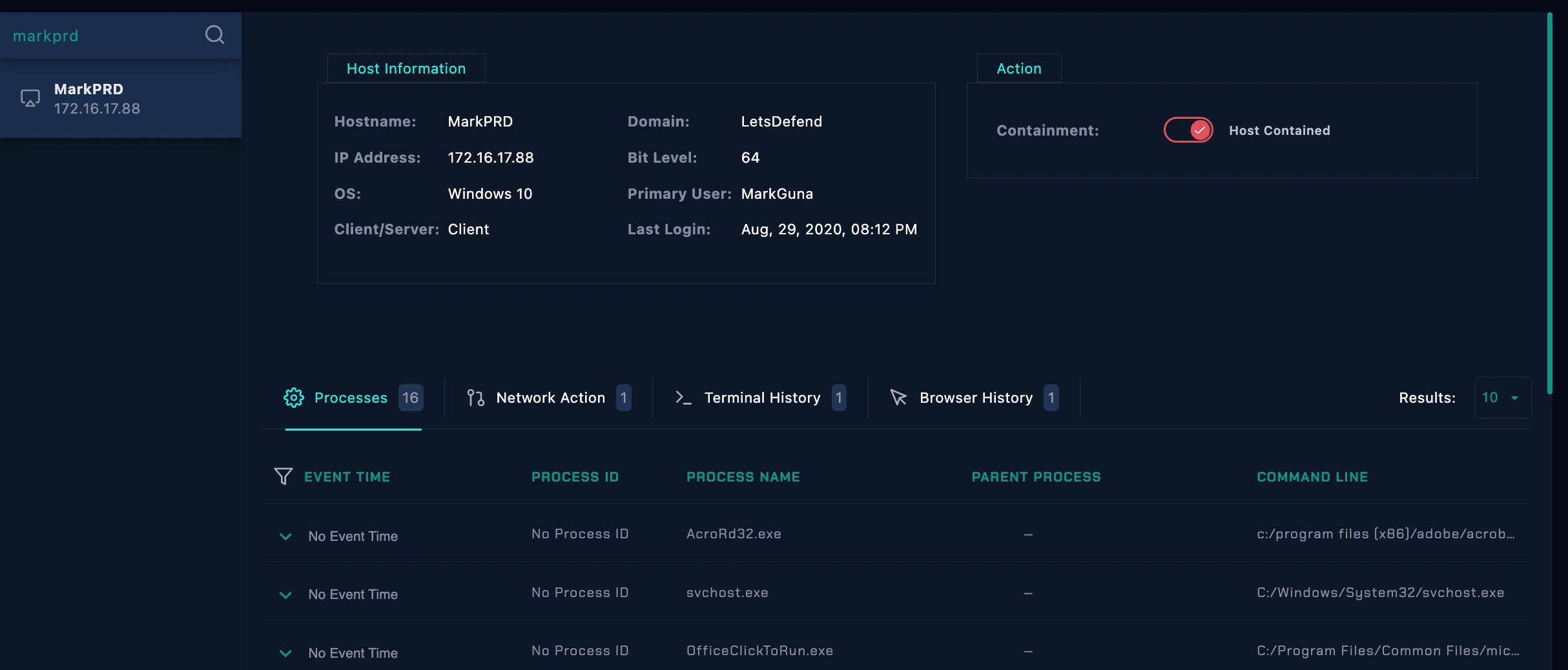
Host containment
2. Tier 2 escalation:
Escalated this issue to tier 2 analyst for further analysis.
Recommendations:
Incident Documentation:
User Awareness:
Conducted user awareness training on the dangers of clicking on suspicious links and engaging with untrusted content.
Lesson learned
It is True Positive alert, because ab.exe is ransomware and encrypted all files on the machine. Conducting dynamic analysis using a sandbox environment, we can see how it is acting.
Conclusion:
The incident was successfully reported to Tier 2 analyst. Continuous monitoring and user education are critical to prevent future ransomware incidents.
Like this project
Posted Dec 5, 2023
This report outline the detect, response and mitigations step taken on a security event indicating the presence of Avaddon Ransomware



