Event ID: 36 - [SOC104 - Malware Detected]
Table Of Content
SOC - LetsDefend.io
This is a report on what I have done training at the SOC Analyst Fundamentals course on letsdefend.io. Letsdefend.io is a good platform for blue team training.
Malware Detected Walkthrough.
SOC ANALYST REPORT
Incident Details:
Incident ID: Event ID: 36 - [SOC104 - Malware Detected]
Date and Time of Detection: Dec 01, 2020, 10:23 AM
Incident Severity: High
Incident Category: Malware
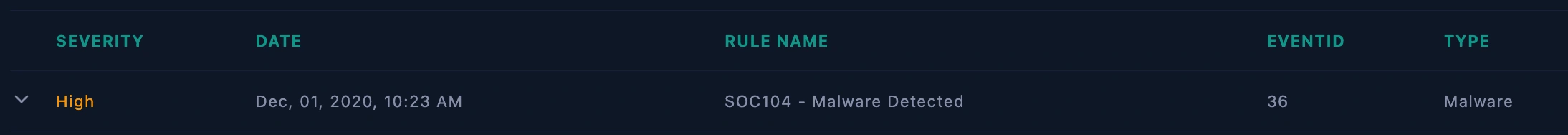
SIEM alert
Summary:
The SOC detected a security event Event ID: 36 - [SOC104 - Malware Detected] indicating the presence of malware. This report outlines the analysis, investigation, and mitigation steps taken.
Incident Description:
Upon analysis of the SIEM simulation, Event ID: 36 triggered an alert due to the detection of malware on host AdamPRD (10.15.15.18). Turns out to be a Maze Ransomware that successfully attacked the affected host. The alert raised concerns about a potential security incident, prompting further investigation. Reference for Maze Ransomware.
Maze ransomware was notorious for its strategy of not only encrypting files but also exfiltrating sensitive data from the victim's system. The attackers threatened to release this data publicly unless the ransom was paid. This dual-threat approach added an extra layer of pressure on the victims to meet the ransom demands.
Investigation Steps:
Initial Triage:
Reviewed the SIEM alert dashboard for relevant details.
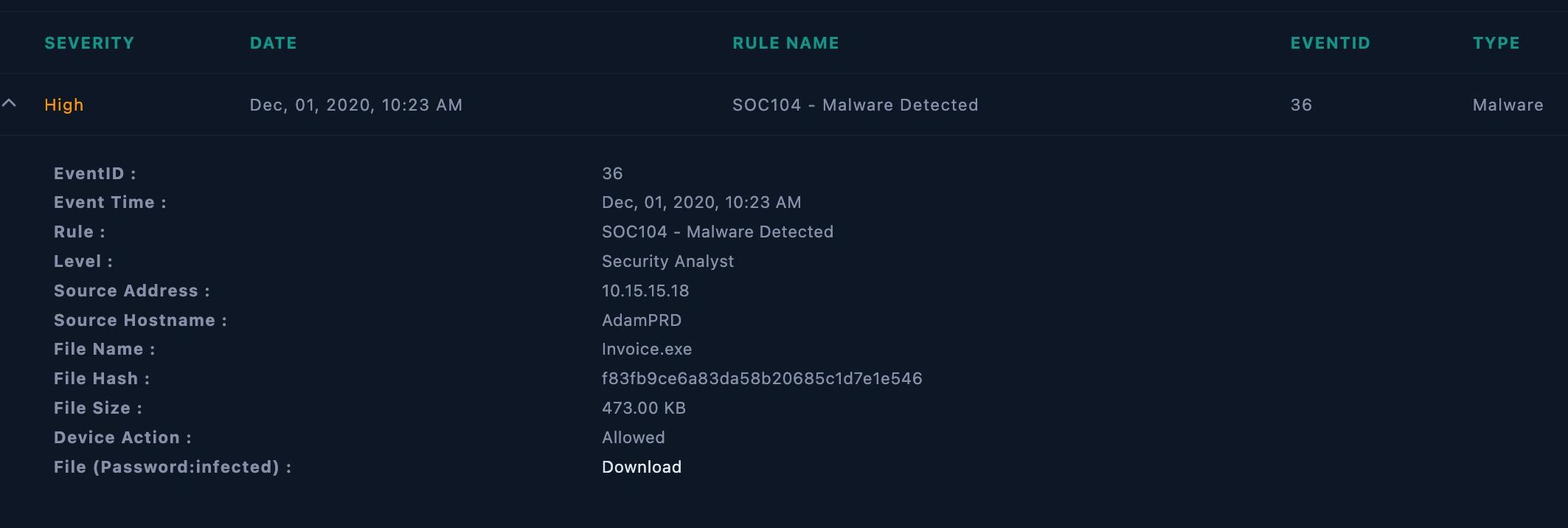
Alert details
Event Analysis:
Examined the details of Event ID: 36 to understand the characteristics of the detected malware.
Network Traffic Analysis:
Investigated network traffic logs to identify communication patterns related to the malware.
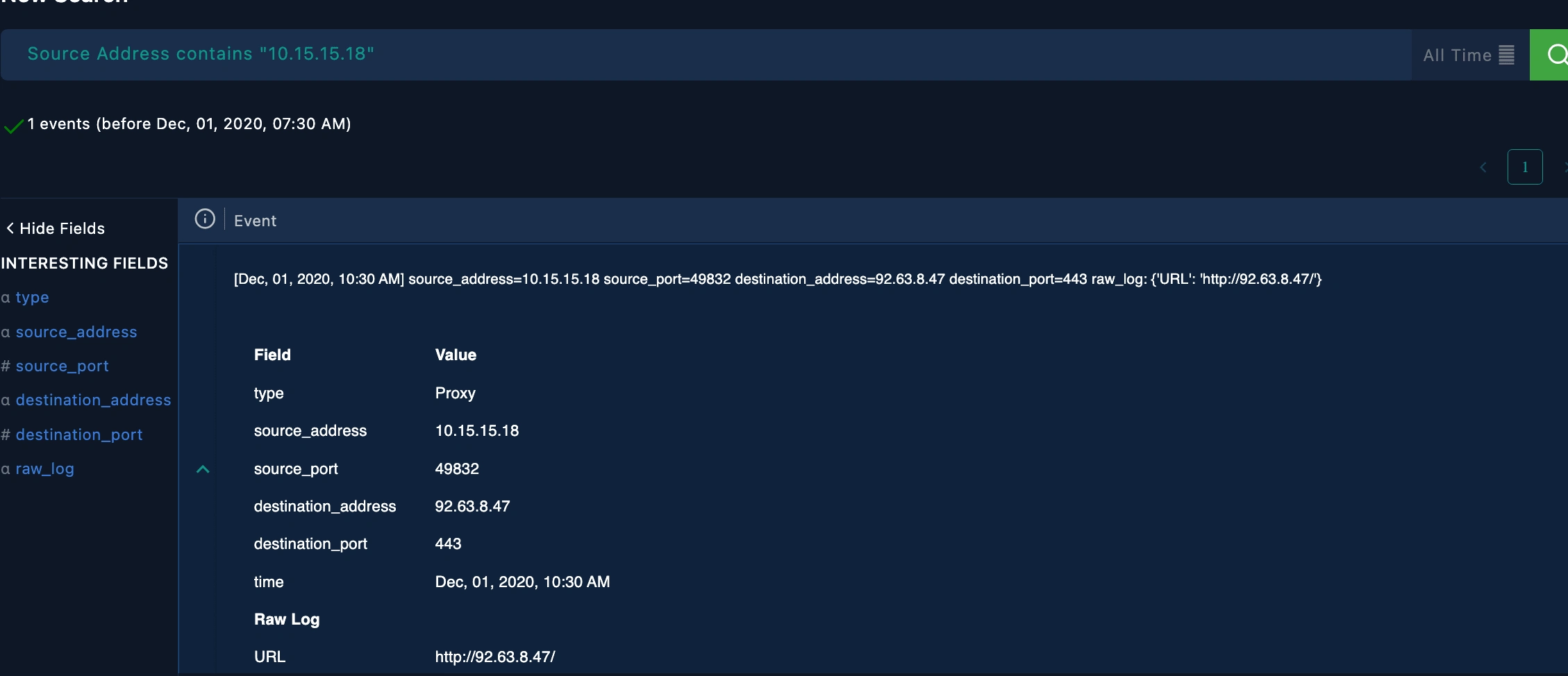
Containment host appropriate to avoid any further compromises.
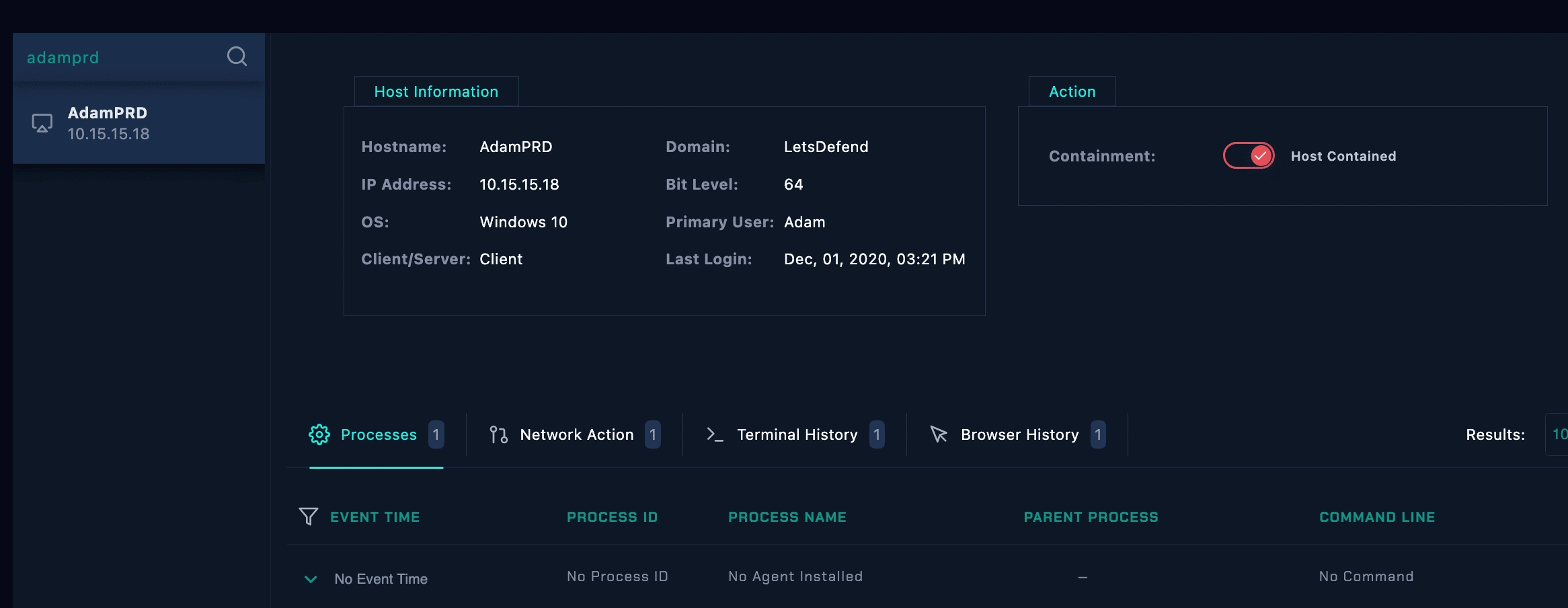
adamPRD contained
Findings:
Malware Identification:
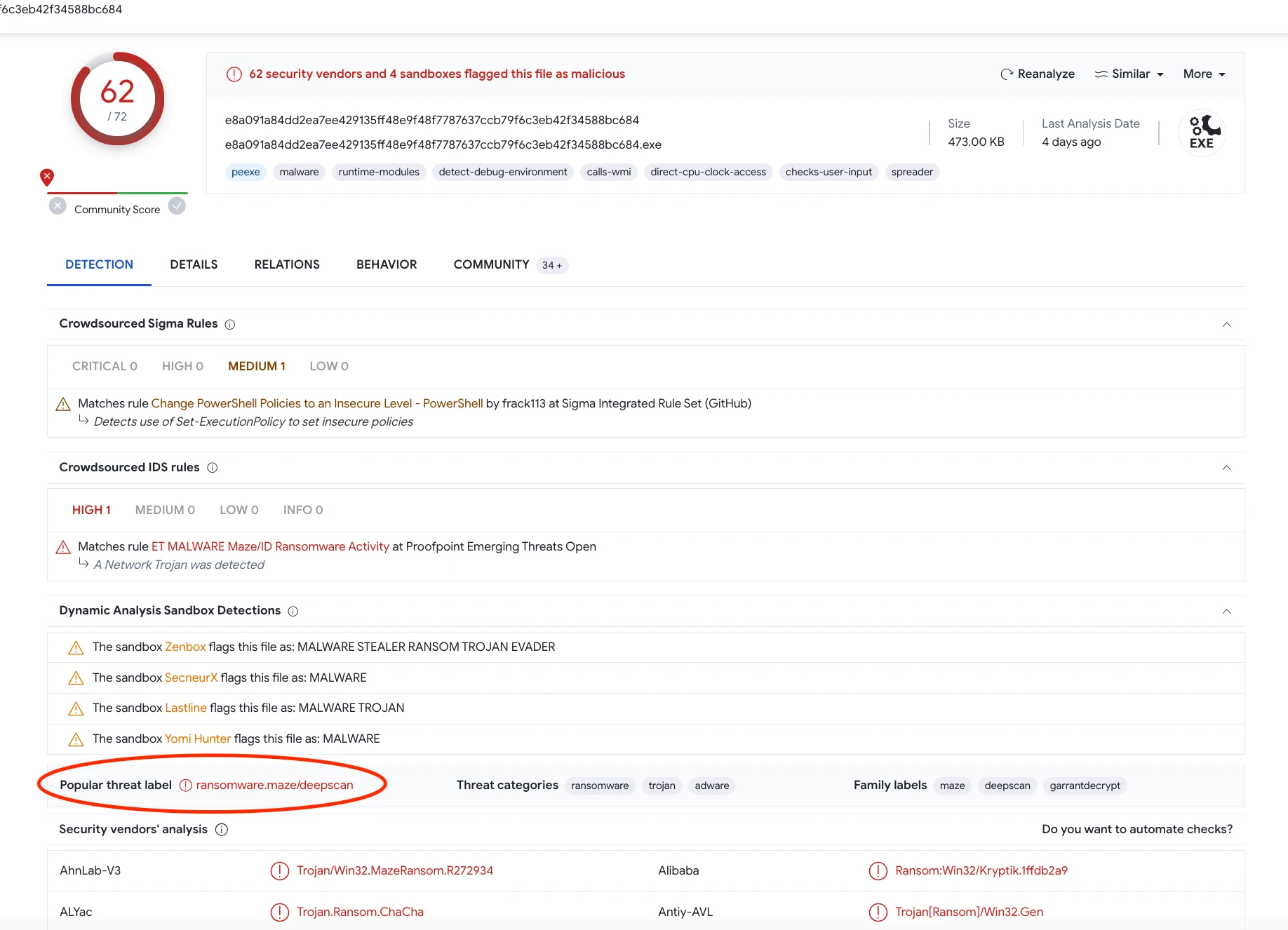
virustotal
Mitigation and Response:
Isolation:
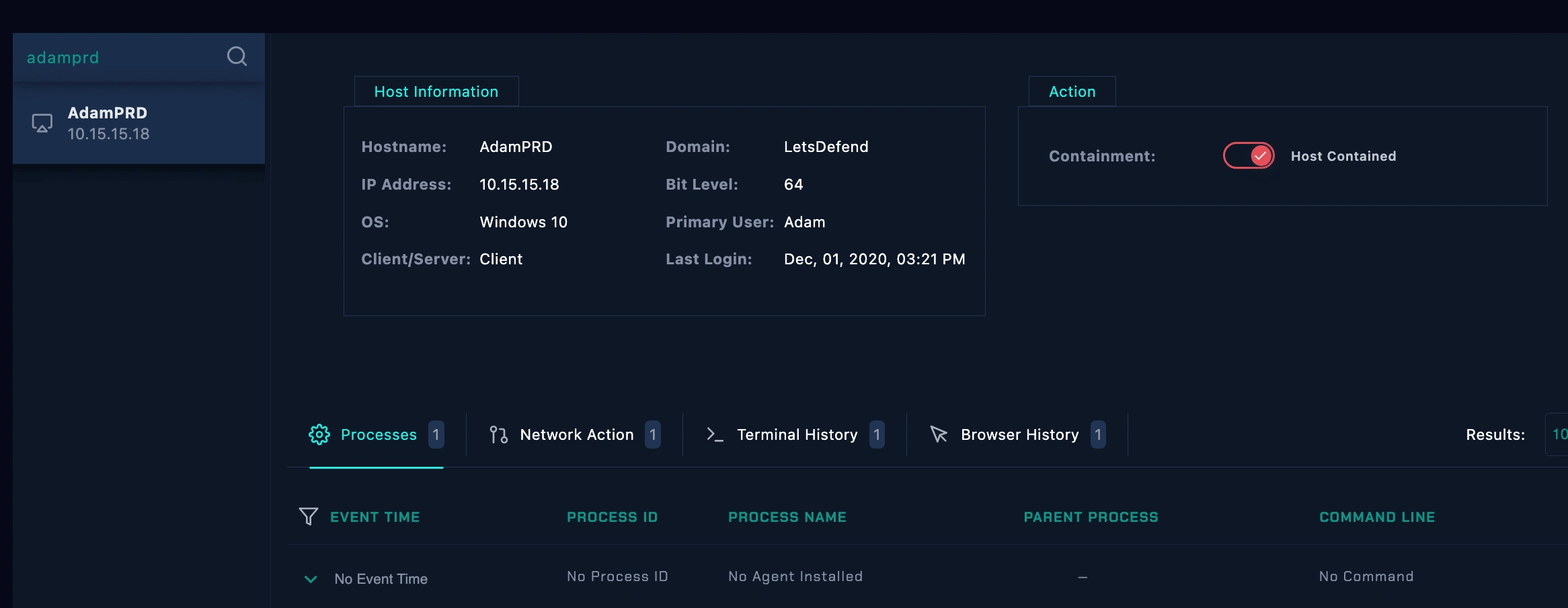
isolation on adamPRD
Malware Removal:
Recommend Tier 2 / Tier 3 to Initiate the removal of the detected malware from the affected system.
Recommendations:
Incident Documentation:
User Awareness:
SIEM Rule Enhancement:
Conclusion:
The incident was successfully mitigated through prompt detection, analysis, and response. Continuous monitoring and proactive security measures are crucial to preventing similar malware incidents in the future.
Like this project
Posted Dec 5, 2023
Event ID: 36 triggered an alert due to the detection of malware on host AdamPRD (10.15.15.18). Turns out to be a Maze Ransomware.




