SOC146 - Phishing Mail Detected - Excel 4.0 Macros
SOC - LetsDefend.io - Phishing Mail Walkthrough.
This is a documentation on what I have done training at the SOC Analyst Fundamentals course on letsdefend.io. Let'sdefend.io is a good platform for blue team training.
Alert triggered.
Shows an alert generated from SIEM (SOC146 - Phishing Mail Detected - Excel 4.0 Macros)
On this report, I will be triaging the Excel 4.0 Macros vulnerability - Phishing Mail Detected.
Here's the full details on this Excel 4.0 Macros vulnerability For your reference.
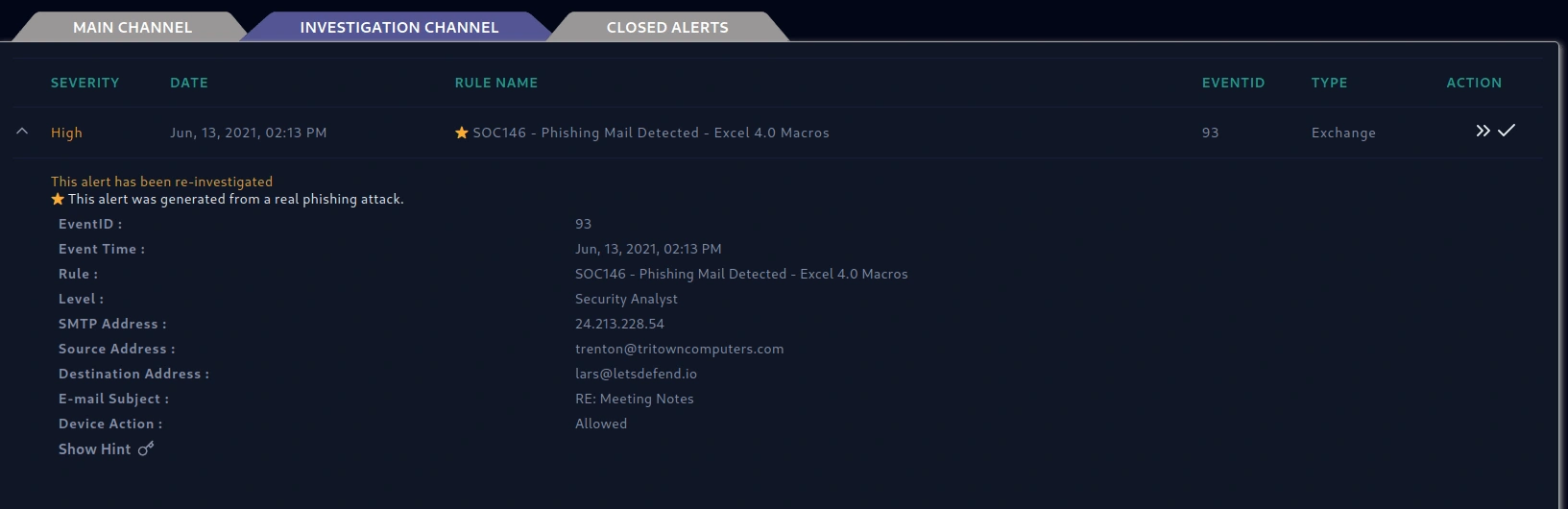
Overview of the Alert
The event has triggered an alert on SIEM:
I can see that a suspicious behaviour called the SOC146 - Phishing Email Detected -Excel 4.0 Macros. Figure above, able to view the SMTP address, Destination Address, Source address and E-mail Subject.
The investigation of the alert :
Case management :
Incident Details
A playbook is a document that describes how to verify a cybersecurity incident and how the incident should be responded. The purpose of the playbook is to document what the runbook should do.
Reference : wikipedia
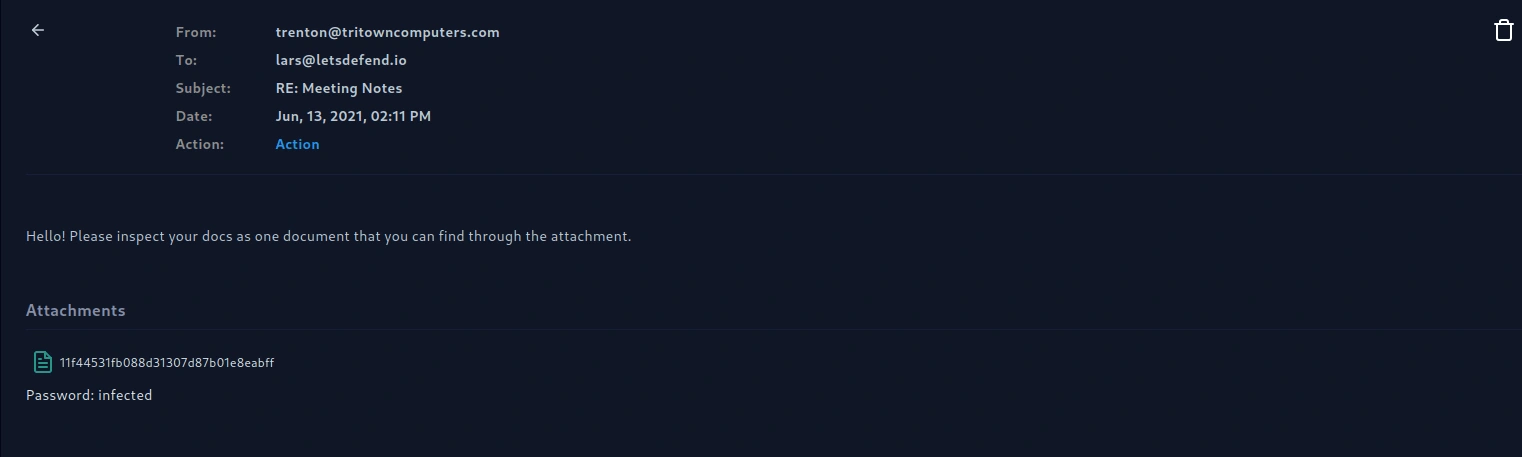
Let's take a look at the malicious email
Key information on the email.
From: trenton@tritowncomputers.com
To: lars@letsdefend.io
Subject: RE: Meeting Notes
Date: Jun, 13, 2021, 02:11 PM
Attachment in zip file : 11f44531fb088d31307d87b01e8eabff.zip
Trenton's Mailbox
Unzipped the file and found three files.
iroto.dll
iroto1.dll
research-1646684671.xls
Malicious files on zip
Virustotal for analysis
After unzipped the files then I scan these files into Virustotal.com to get an overview of the malicious files and do analysis from details provided.
iroto1.dll
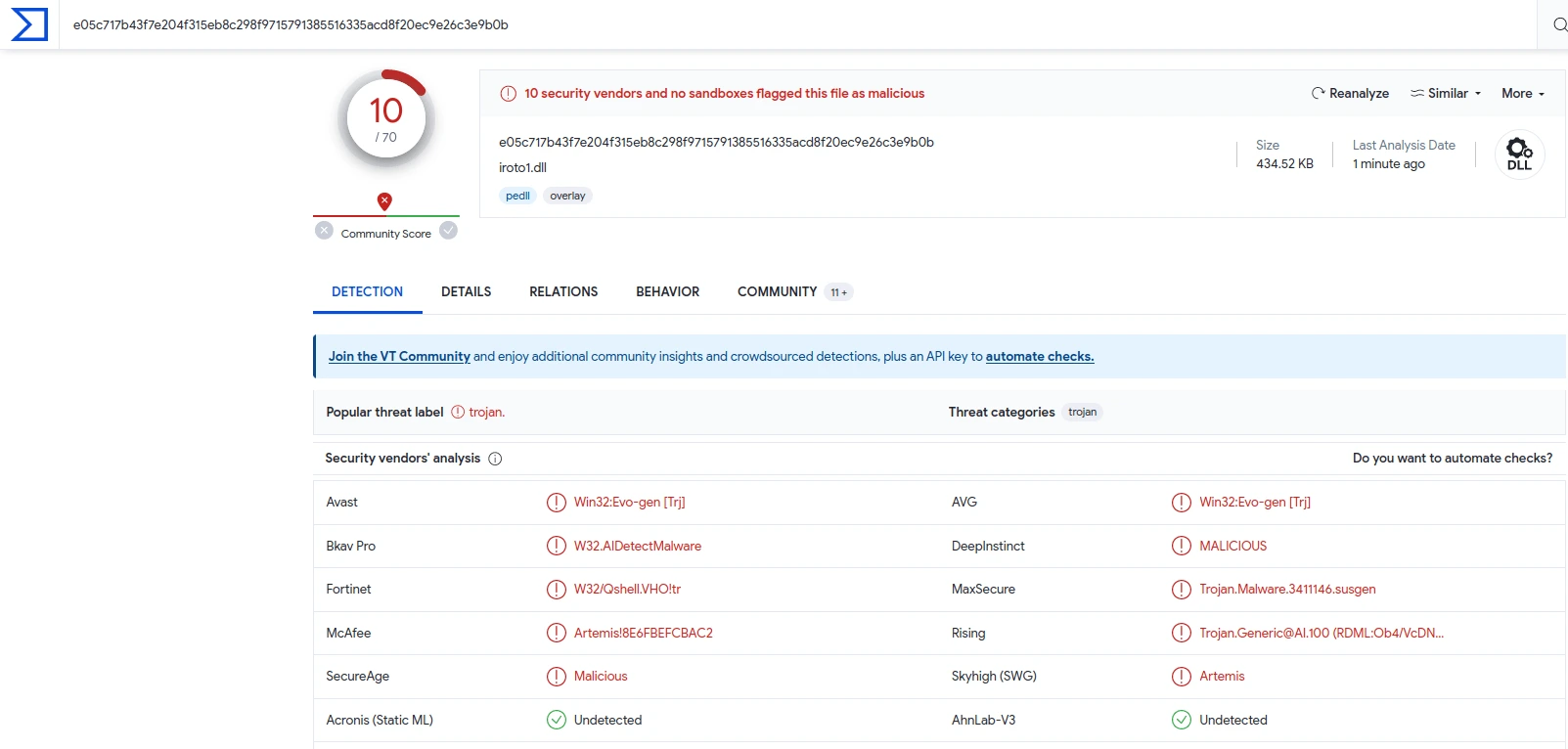
iroto1.dll is malicious
iroto.dll
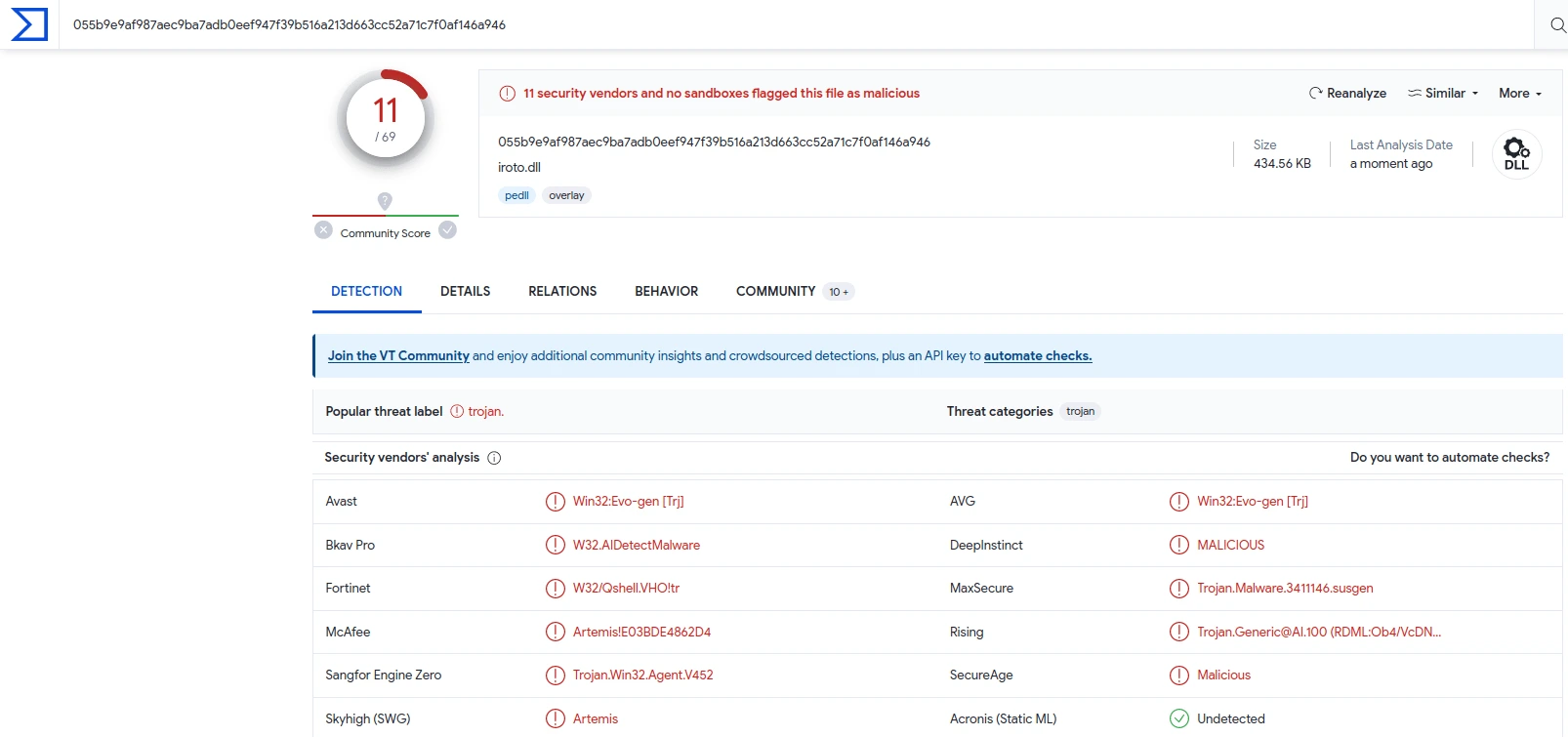
iroto.dll is malicious
research-1646684671.xls
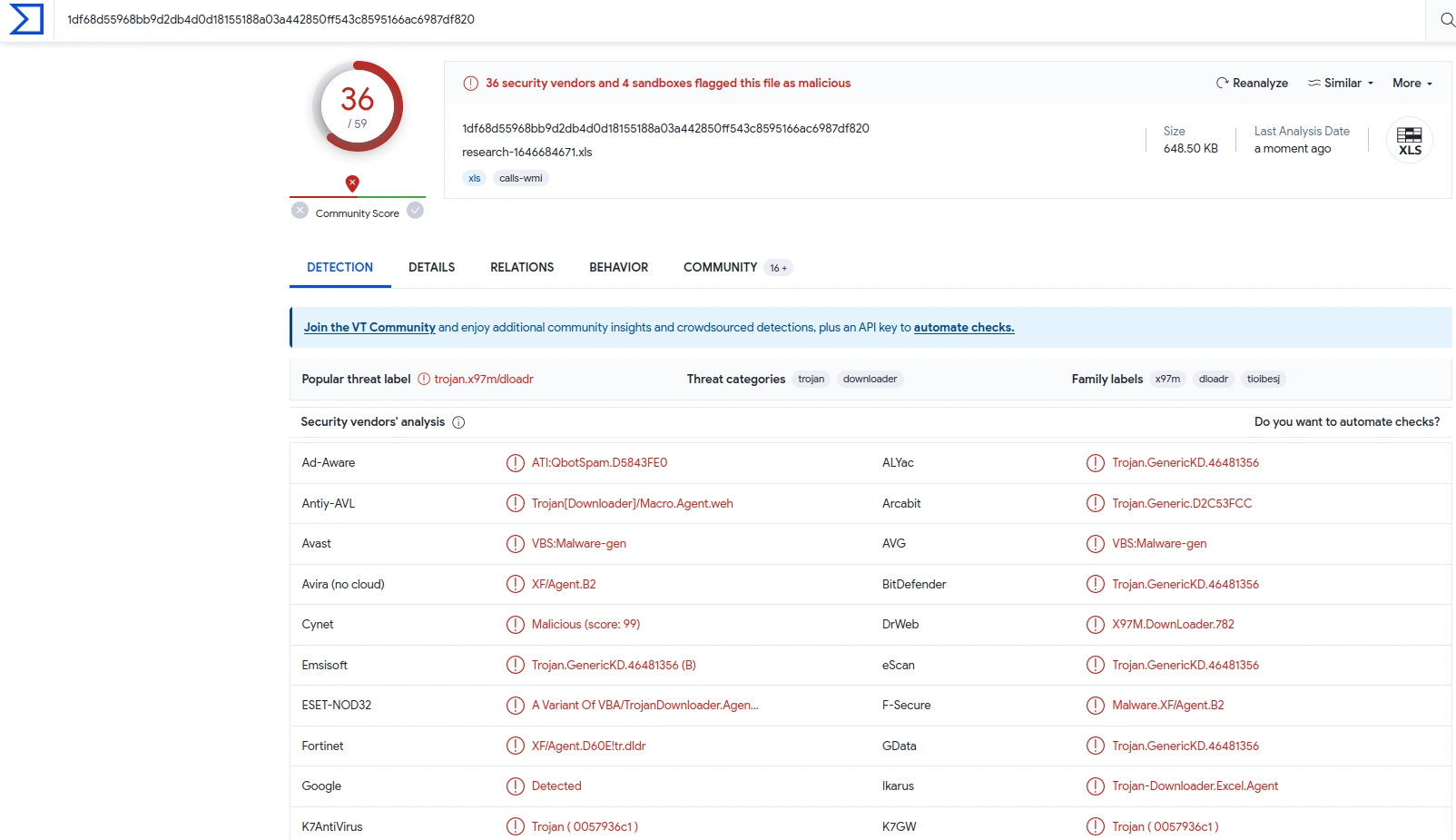
research-1646684671.xls is malicious
Based on Virustotal.com, those three files are flagged as malicious;
All of the 36 security vendors or antivirus detected that the file was malicious
We can see that the file is trojan malware.
ANY.RUN Analysis;
Any.run is an interactive malware analysis sandbox this is where the dynamic analysis is utilized. Here's the full report from Any.run
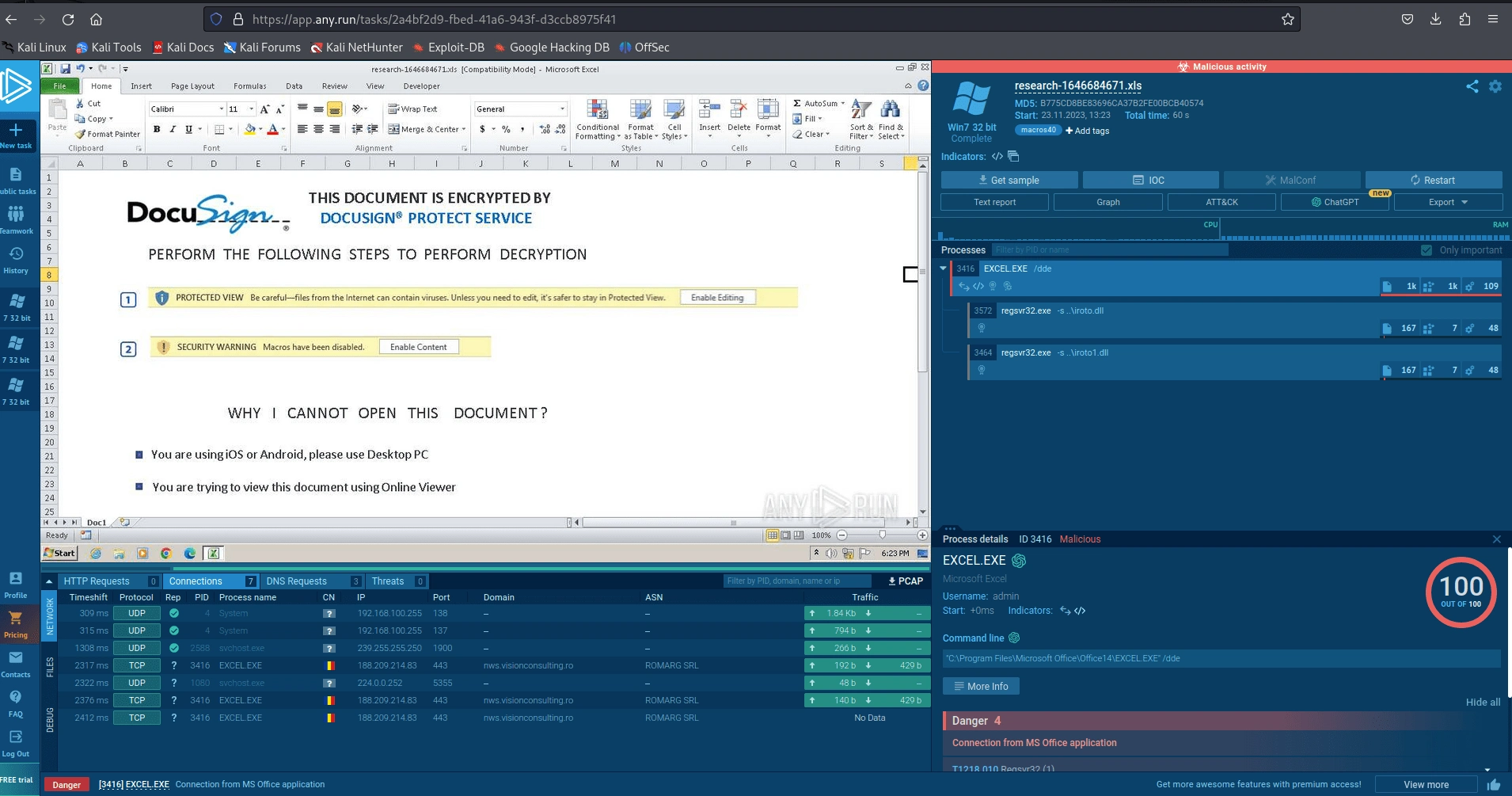
research-1646684671.xls on ANY.RUN
The file was executed in a sandbox environment, and it executed malicious processes such as EXCEL.EXE.
The Behavior Graph
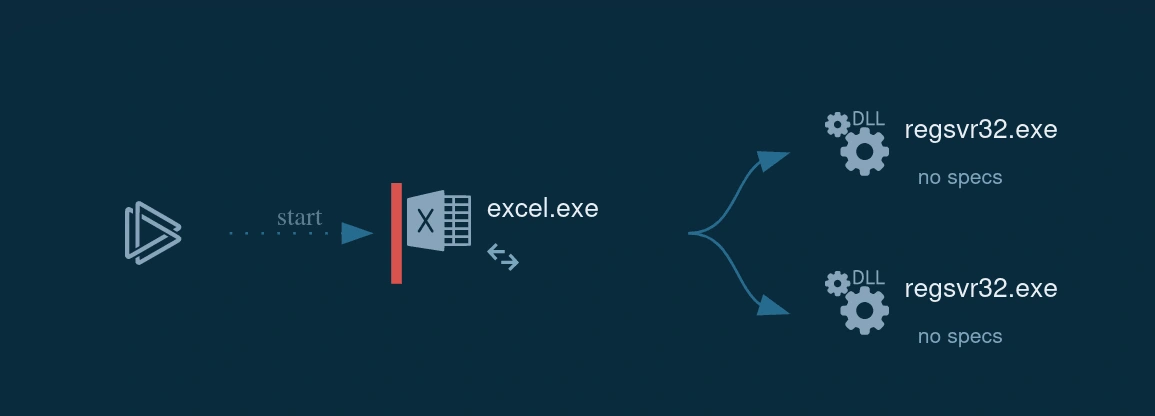
behavior graph
The behavior graph shows under all processes, indicators are presented, which give an idea about the activity of a specific process. In this case, the excel.exe has two regsvr32.exe command-line programs.
Regsvr32 Summary
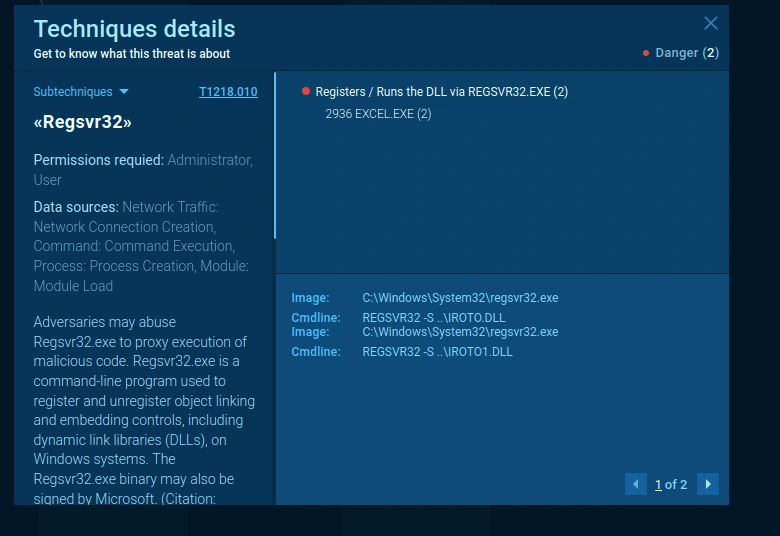
Mitre Att&ck Matrix Info on ANY.RUN
Malicious usage of Regsvr32.exe may avoid triggering security tools that may not monitor the execution of, and modules loaded by, the regsvr32.exe process because of allowlists or false positives from Windows using regsvr32.exe for normal operations.
reference: attack.mitre.org
Network Activity
Connections
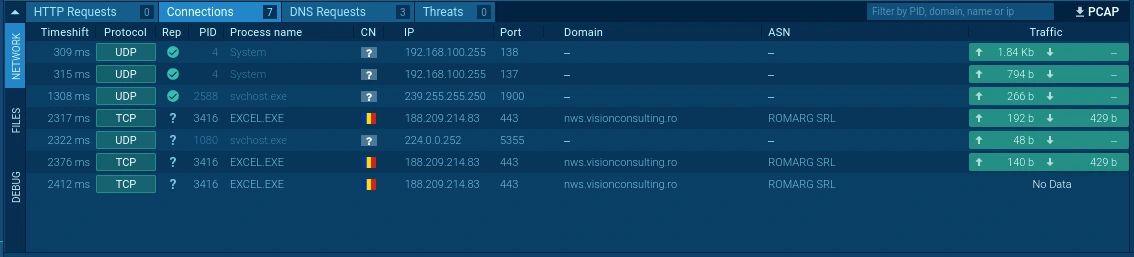
Connections
DNS Request

DNS Request
Details of Process Summary
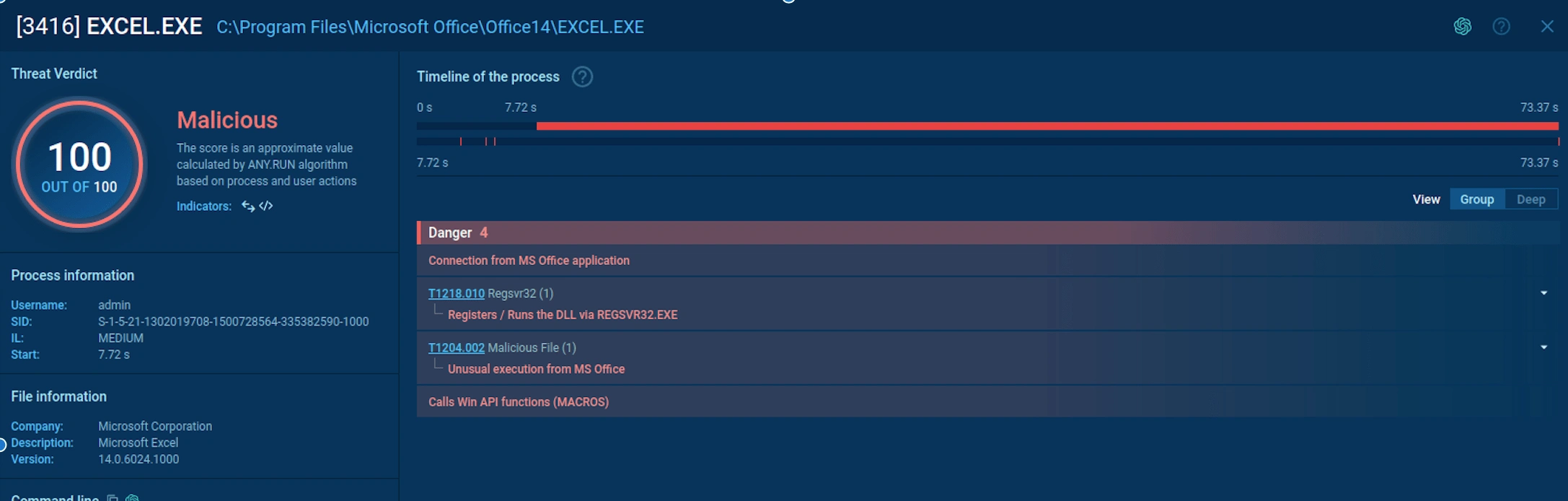
EXCEL.EXE Summary
Contacted Domains
nws.visionconsulting.ro
royalpalm.sparkblue.lk
ctldl.windowsupdate.com
Log Management
Now we will check if someone opened the malicious file or link by examining the C2 addresses
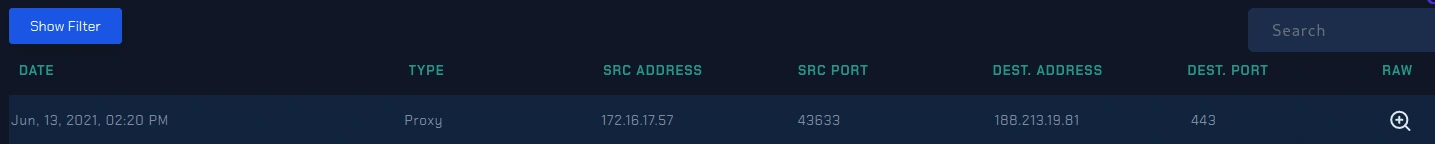
188.213.19.81
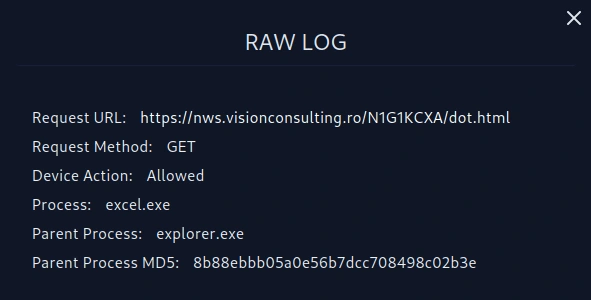
Raw log
192.232.219.67
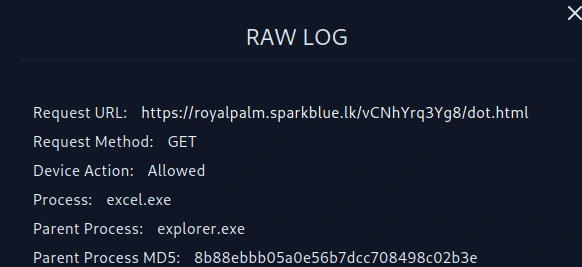
Raw Log
Requested URL
URL: https://royalpalm.sparkblue.lk/vCNhYrq3Yg8/dot.html
URL: https://nws.visionconsulting.ro/N1G1KCXA/dot.html
Endpoint Security
Proceed to endpoint security then containment of the LarsPRD user it is the victim. After that can proceed to investigate the victim's workstation.
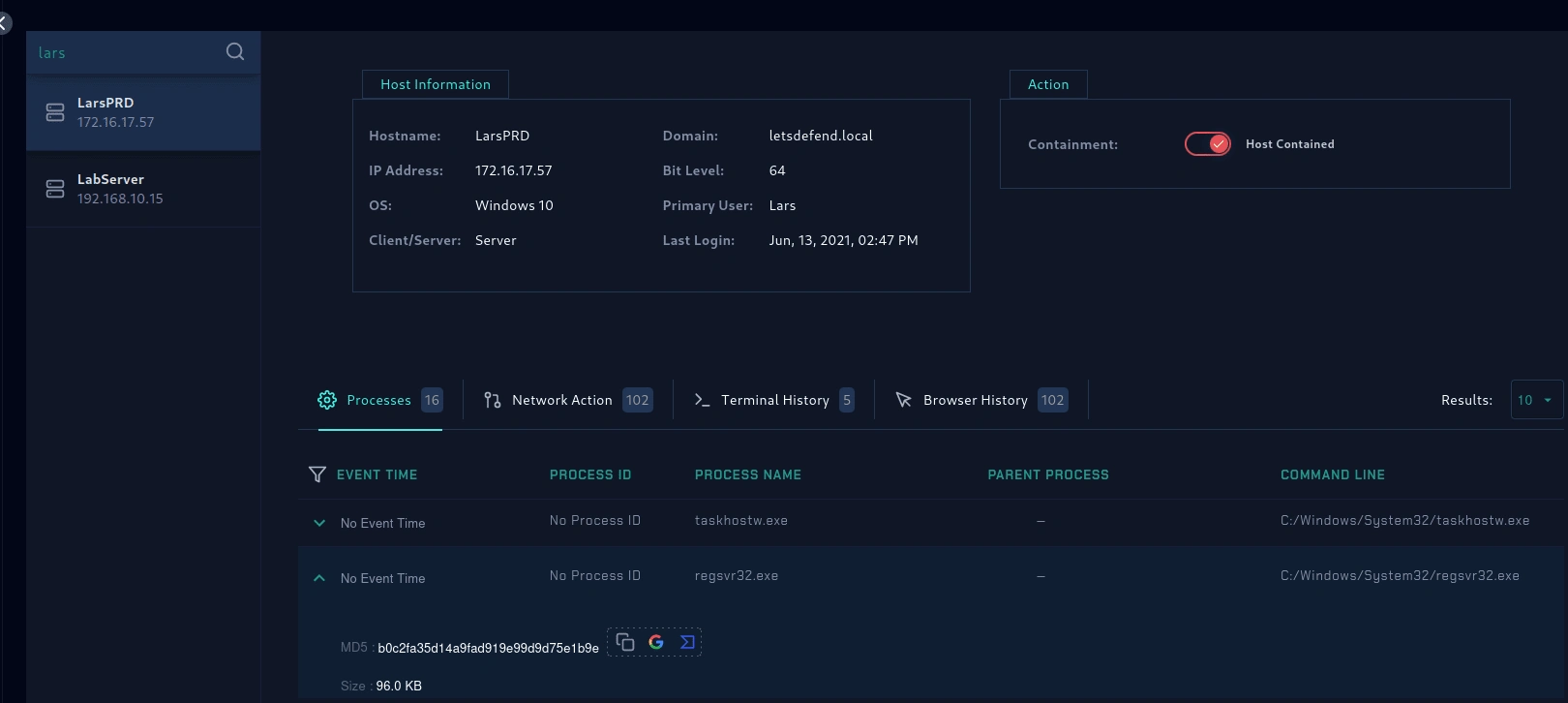
containment on larsPRD
I have the option to look on the endpoint security features which are Processes, network action, terminal history and browse history.
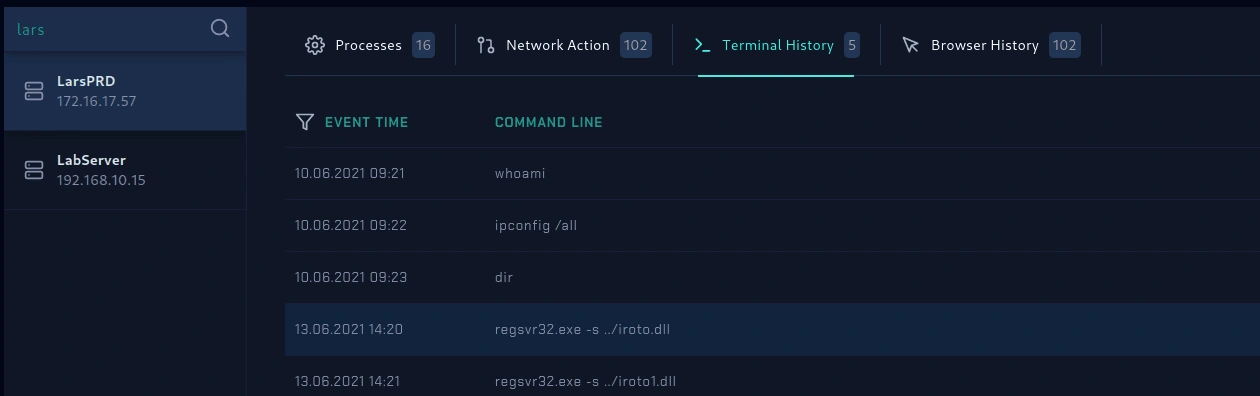
terminal history
I can see that the regsvr32 commands were executed on the victim's machines in the terminal history
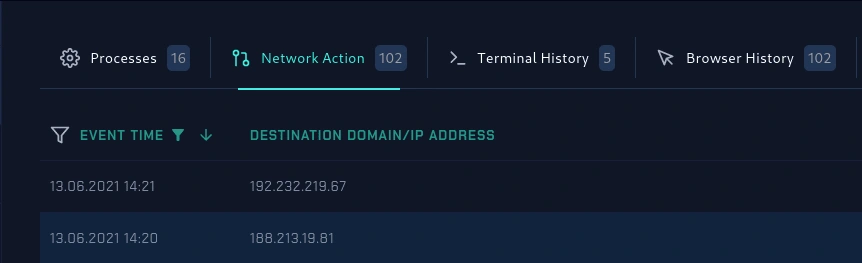
network action
Above are the two malicious IPs communicating with the victim's machine
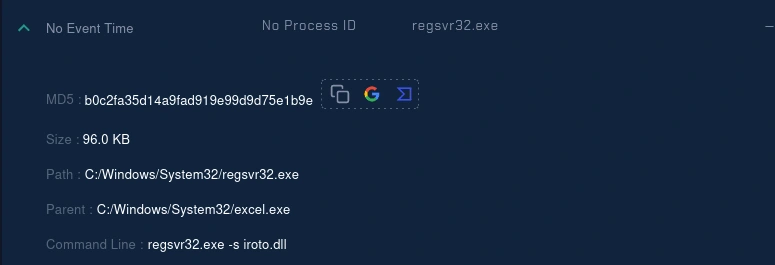
processes
It is shown that Processes regsvr32.exe run by excel.exe known to be the parent process. The command line is ;
regsvr32.exe -s iroto.dll
Conclusion
As a result of the sandbox analysis of the Excel file attached to the e-mail, it is seen that it is harmful. In the sandbox analysis, c2 addresses are obtained. When c2 addresses are searched through log management, it is seen that there is access, therefore it is understood that the malicious excel file is run. When the source address is determined on Log Management and searched on Endpoint Management, it is observed that it is a LarsPRD device. When the Browser History and Network Connections of the LarsPRD device are examined, it has been clarified that the LarsPRD device communicates with malicious addresses. When LarsPRD's CMD History is examined, it is observed that the regsvr32 command, which is included in Excel 4.0 macros, is run.
Playbook details :
Parse email
Playbook
When was it sent?
What is the email's SMTP address?
What is the sender address?
What is the recipient address?
Is the mail content suspicious?
Are there any attachment?
Are there attachments or URLs in the email?
Playbook
Yes
Analyze Url/Attachment
Playbook
Yes
Check if Mail Delivered to User?
Playbook
Delivered
Check If Someone Opened the Malicious File/URL?
Playbook
Opened
playbook
Delete
playbook
Opened
playbook
Next
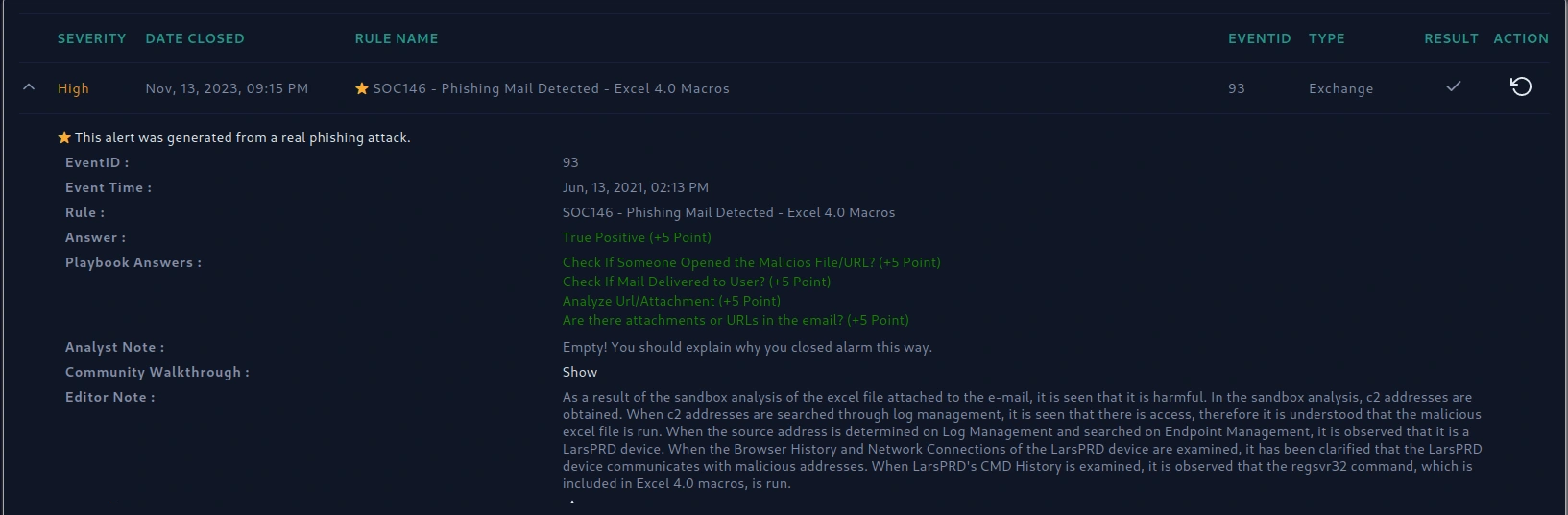
playbook answers
Like this project
Posted Nov 19, 2023
Investigating the Excel 4.0 Macros vulnerability - Phishing Mail Detected from a SIEM Environment. From Letsdefend.io SOC Analyst Fundamentals Course Training.




![EventID: 92 - [SOC145 - Ransomware Detected]](https://media.contra.com/image/upload/w_400,q_auto:good,c_fill/project-cover-06_s9kkre.avif)