SOC165 - Possible SQL Injection Payload Detected
SOC Alert - LetsDefend.io - Possible SQL Injection Payload Detected.
This is a report on what I have done training at the SOC Analyst Fundamentals course on letsdefend.io. Letsdefend.io is a good platform for blue team training.
Table Of Contents
SOC ANALYST REPORT
Incident Details:
Incident ID: Event ID: 165 - [SOC165 - Possible SQL Injection Payload Detected]
Date and Time of Detection: Feb 25, 2022, 11:34 AM
Incident Severity: High
Incident Category: Web Attack
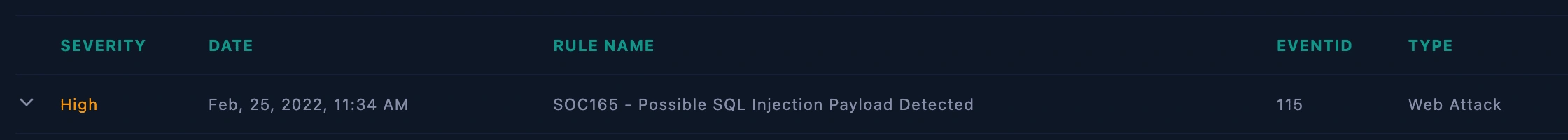
Siem Alert on SOC165 - Possible SQL Injection Payload Detected
Summary:
The SOC detected a security event Event ID: 165 - [SOC165 - Possible SQL Injection Payload Detected] indicating the potential presence of a SQL injection payload. This report outlines the analysis, investigation, and mitigation steps taken.
Incident Description:
Upon analysis of the SIEM simulation, Event ID: SOC165 triggered an alert due to the detection of a possible SQL injection payload on the victim's IP address (172.16.17.18) WebServer1001. The attack was unsuccessful due to a server error. The alert raised concerns about a potential security incident, prompting further investigation.
SQL Injection is a type of attack the attacker uses malicious code in SQL Statements via a search bar or web input to retrieve unauthorised access of information from database.
Investigation Steps:
Initial Triage:
Reviewed the SIEM alert dashboard for relevant details.
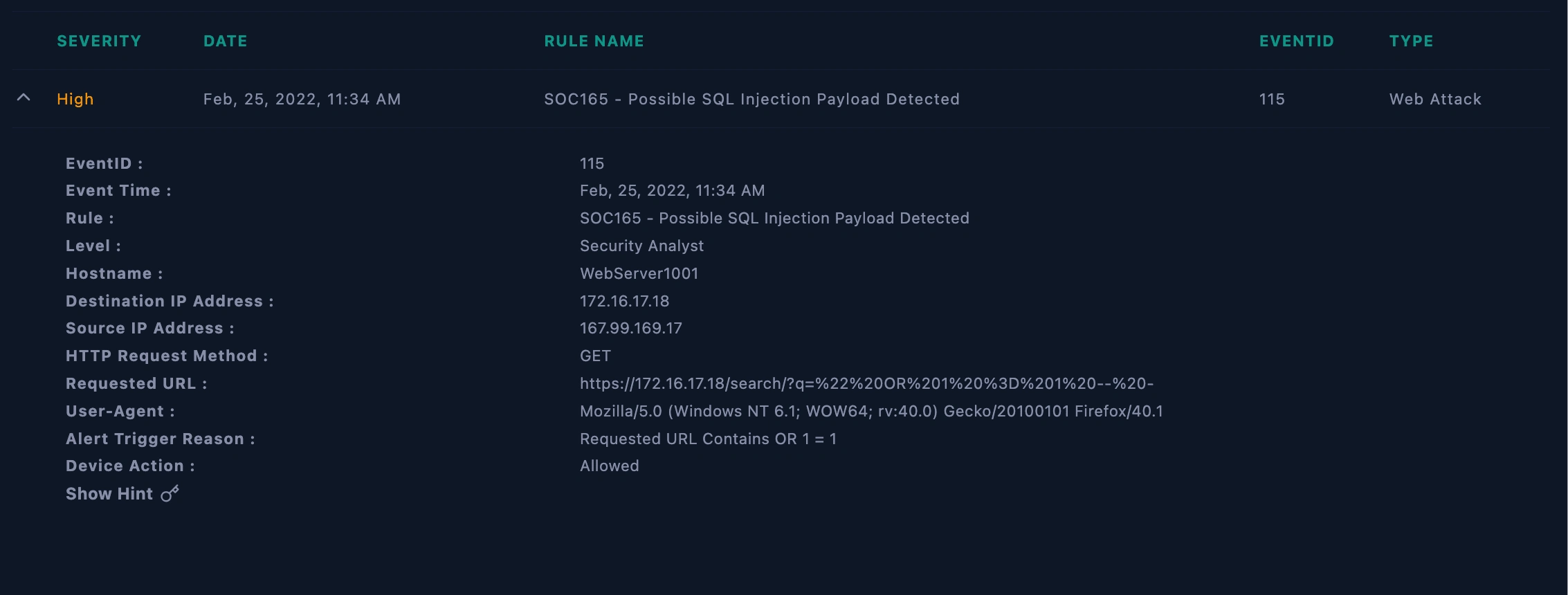
Alert details
Event Analysis:
Examined the details of Event ID: SOC165 to understand the characteristics of the detected SQL injection payload.
URL Decoding
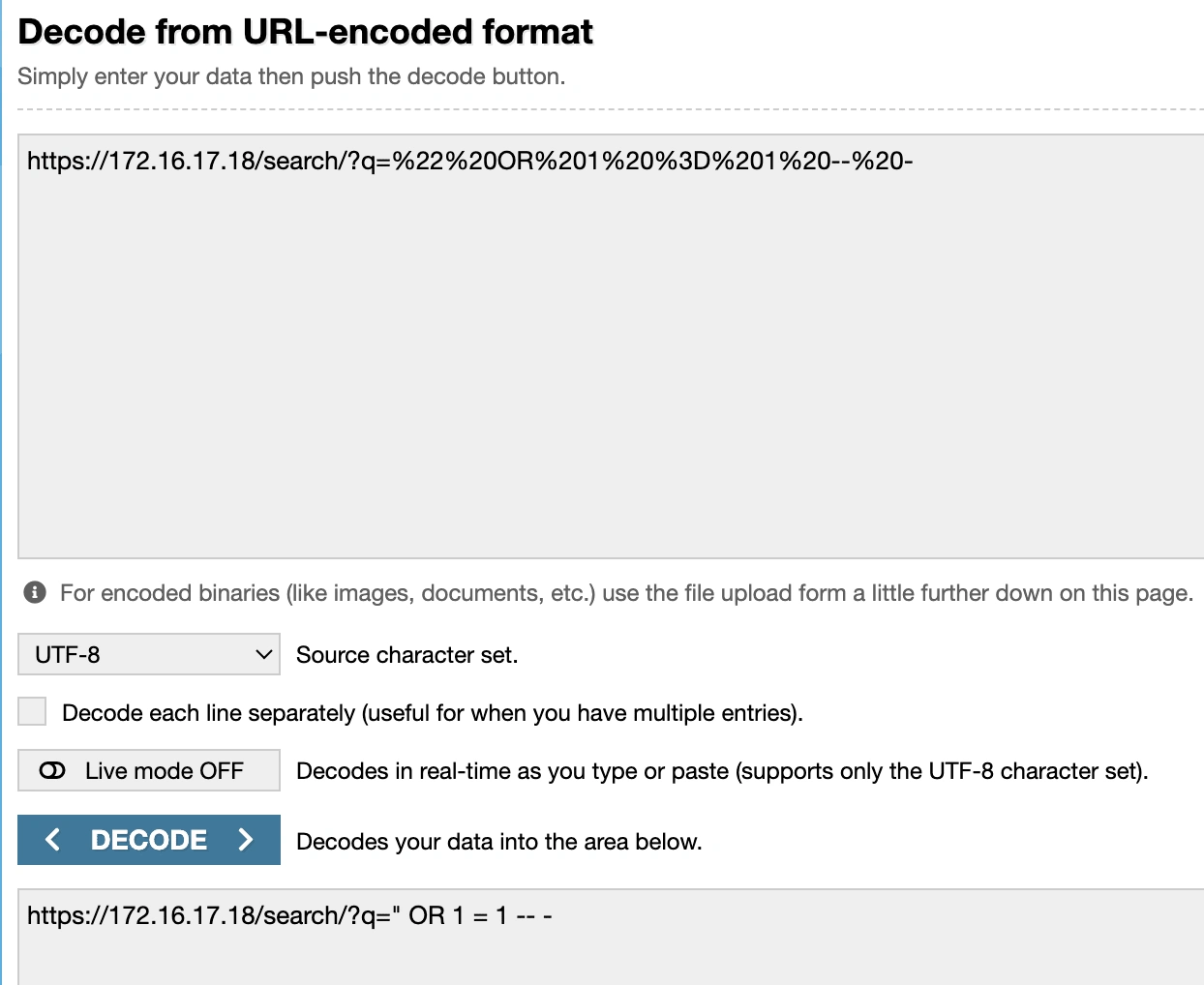
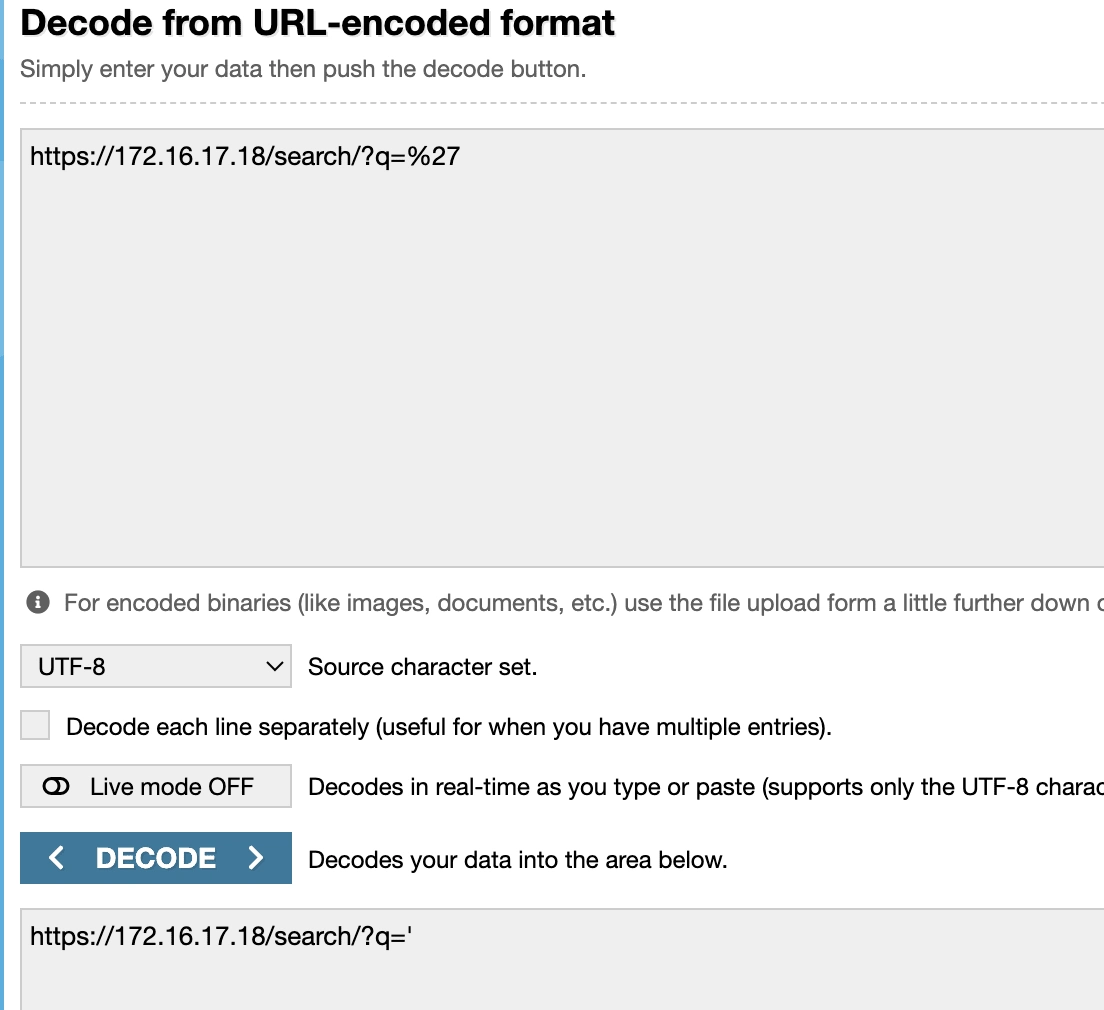
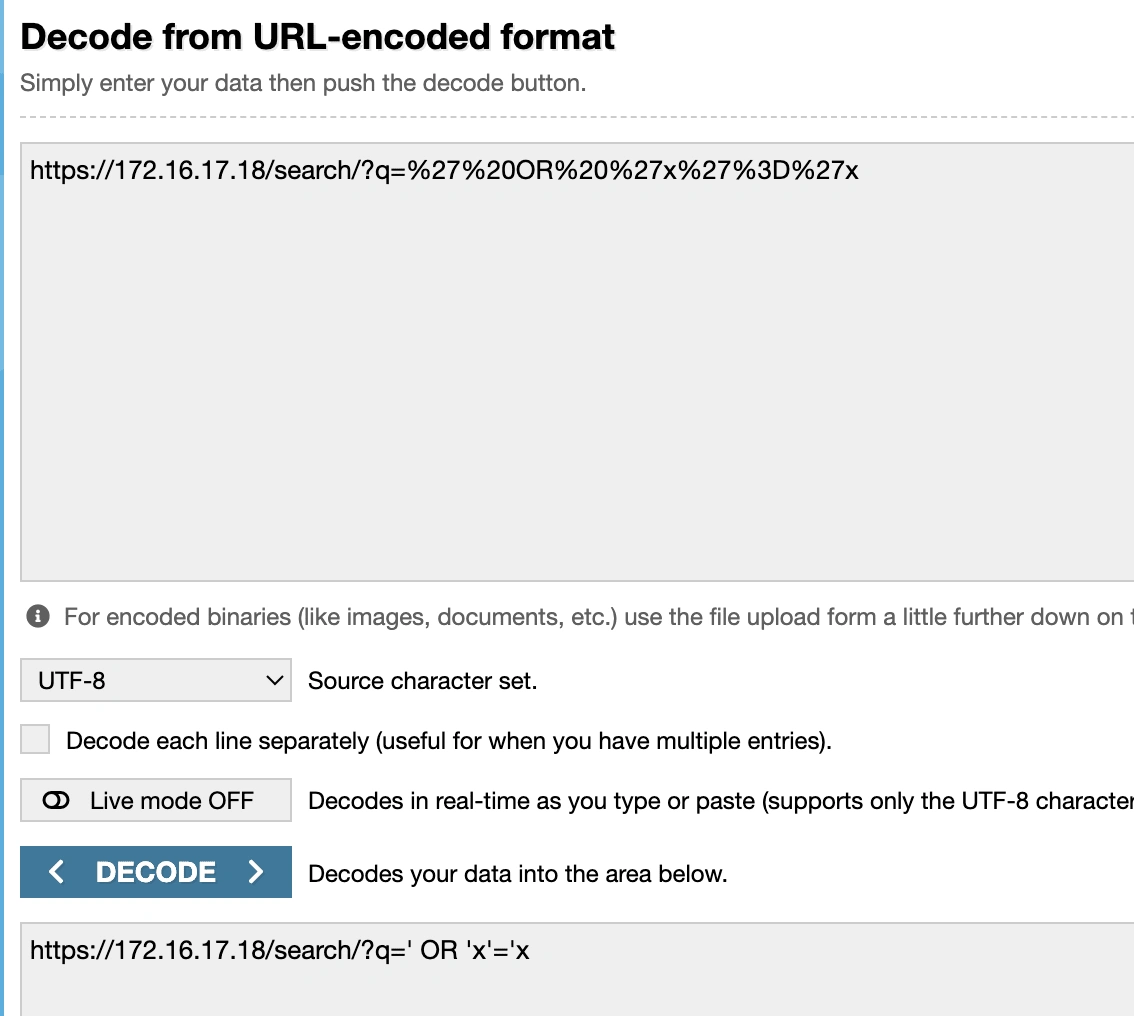
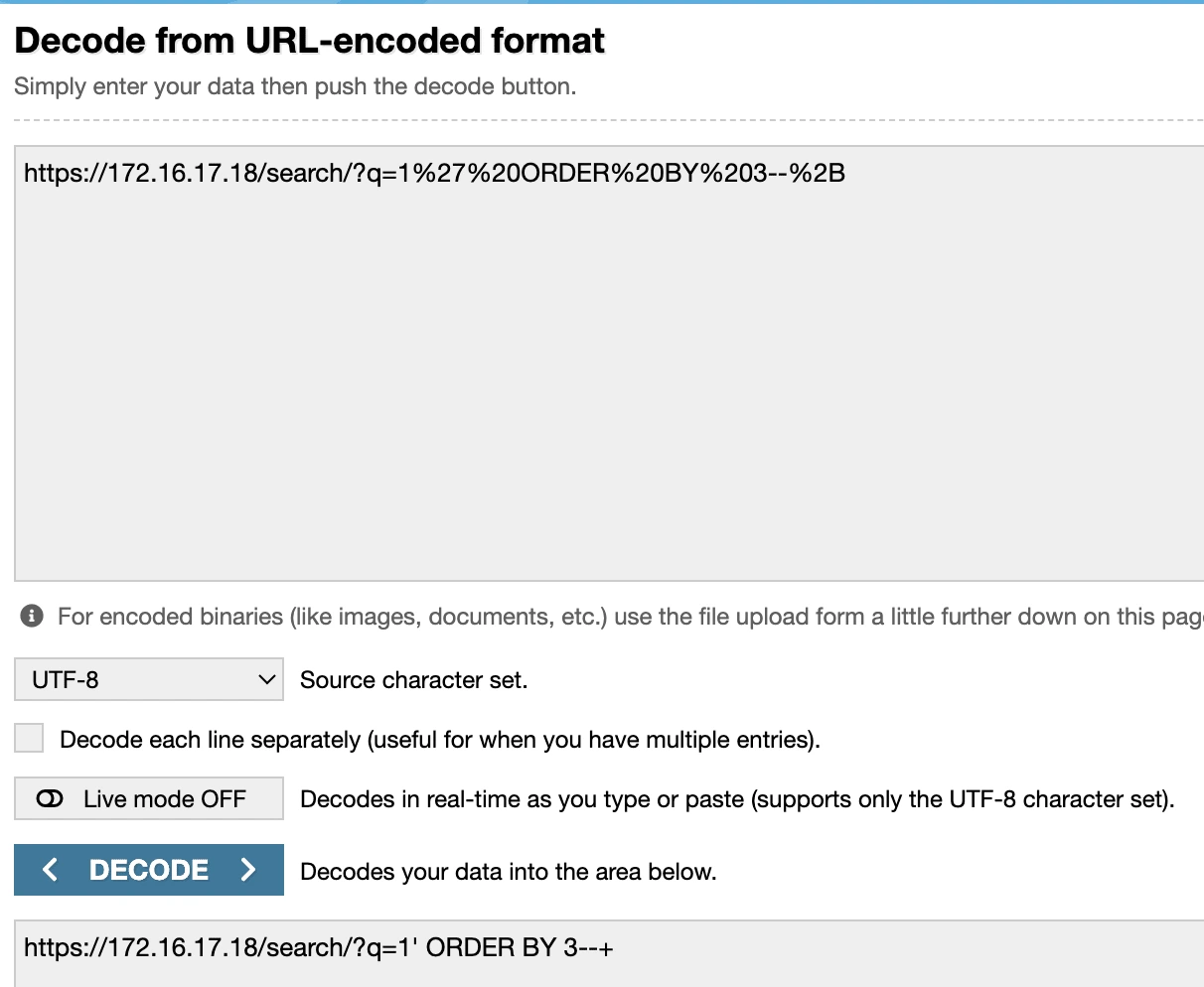
Decoded URL
This shows that the attacker leveraged
OR 1 = 1 it is a classic condition in SQL injection attemptsGathered information on the affected system and user accounts involved.
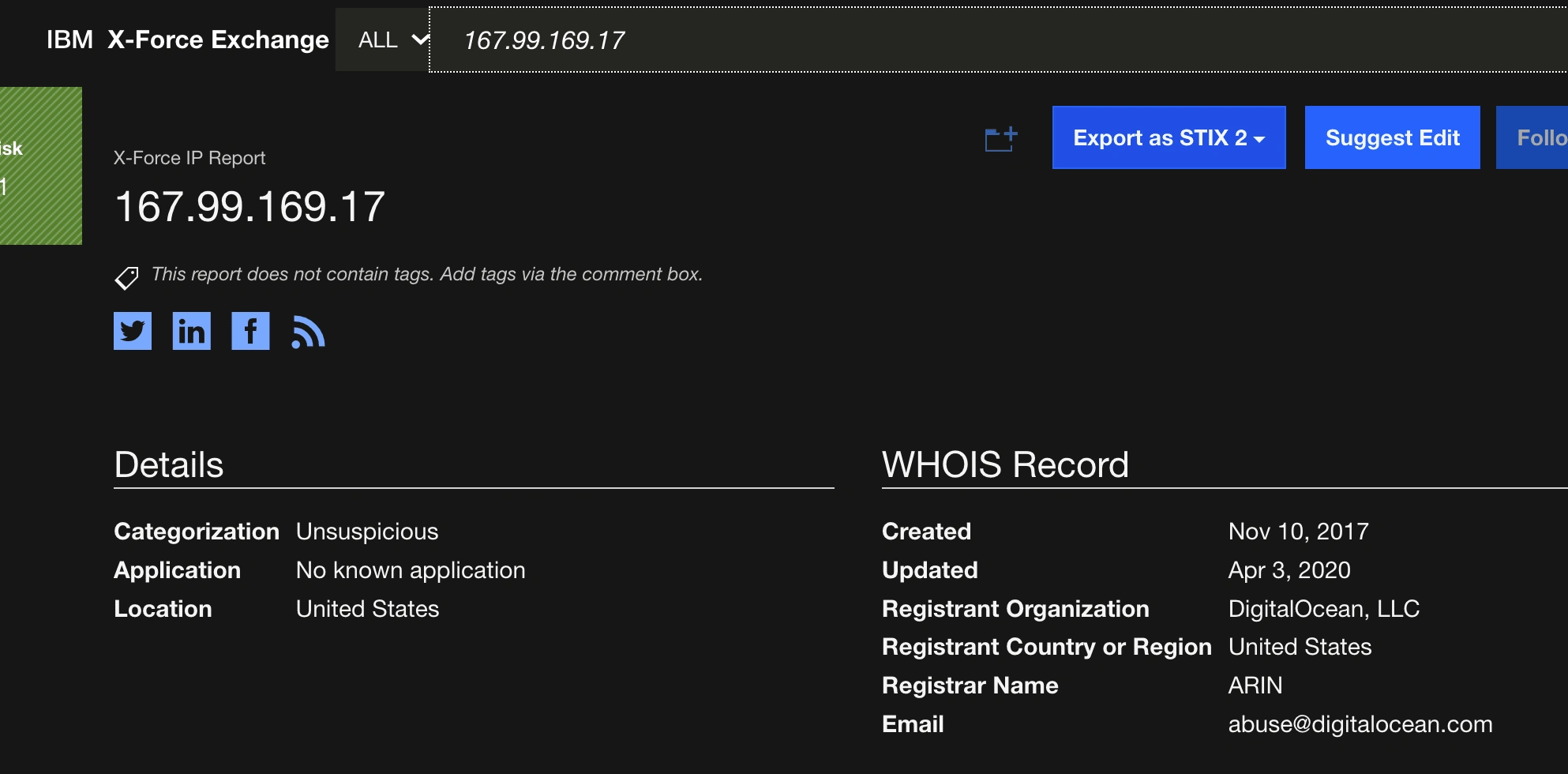
IBM X-FORCE EXCHANGE details on malicious IP
Log Management:
WebServer1001 logs for signs of SQL injection attempts.
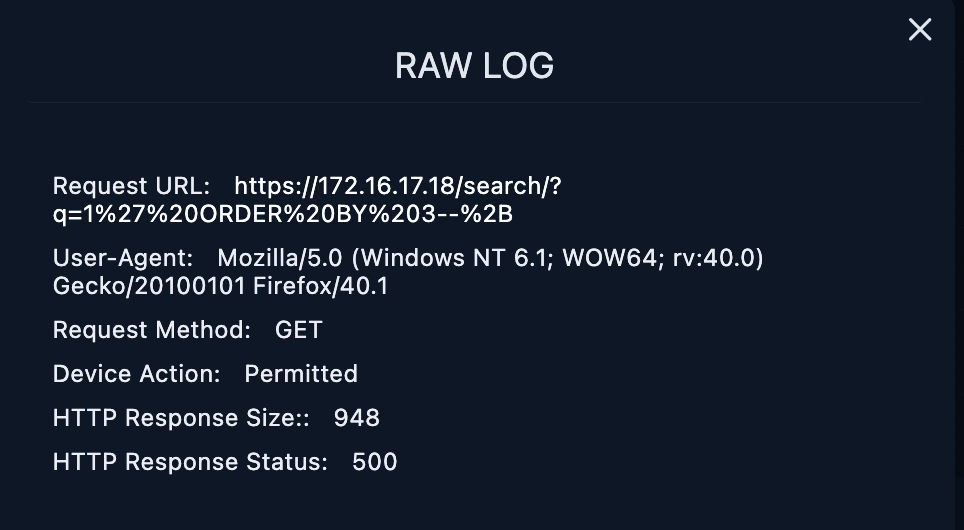
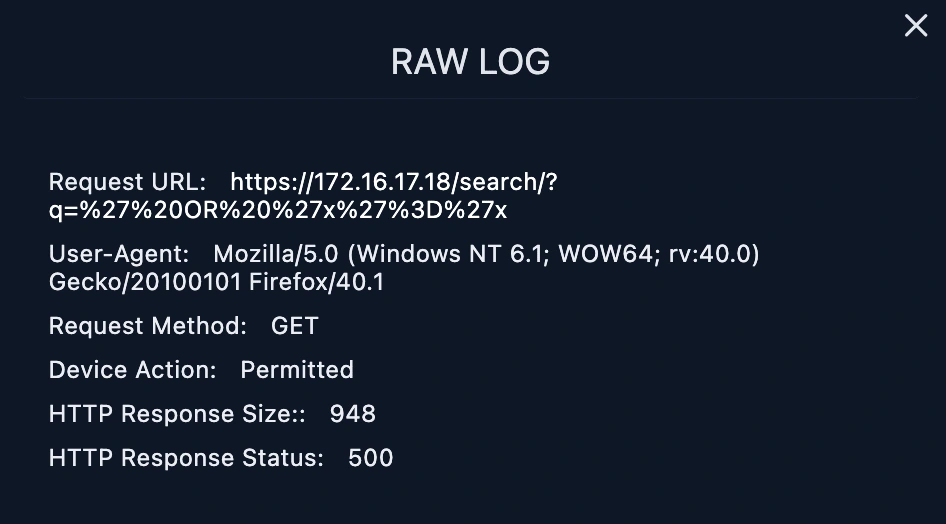
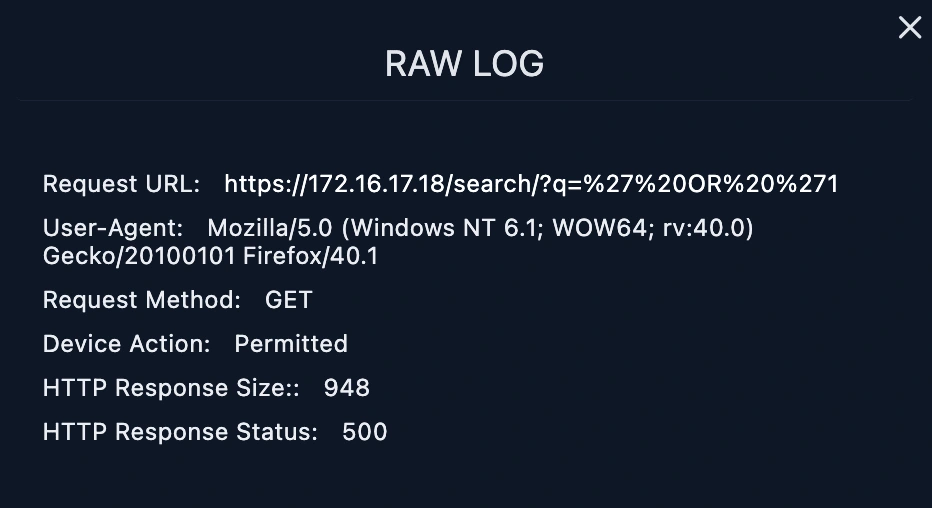
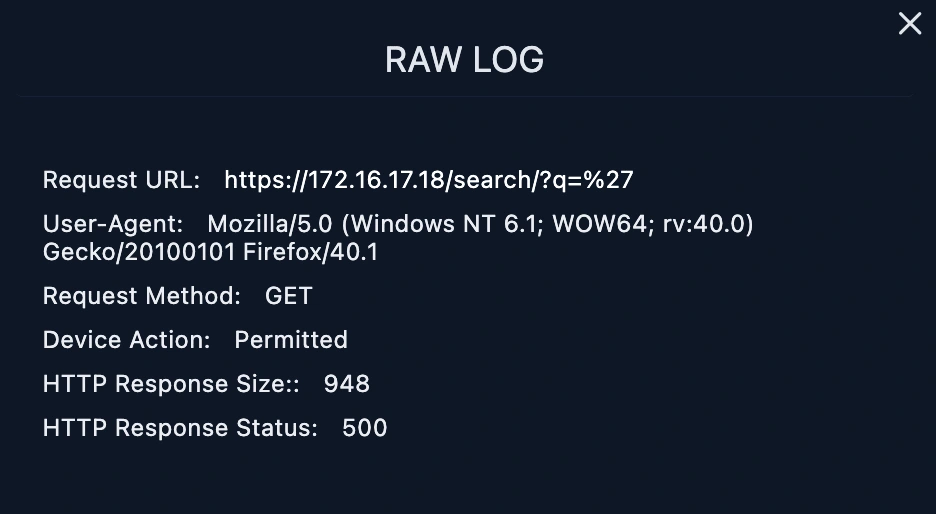
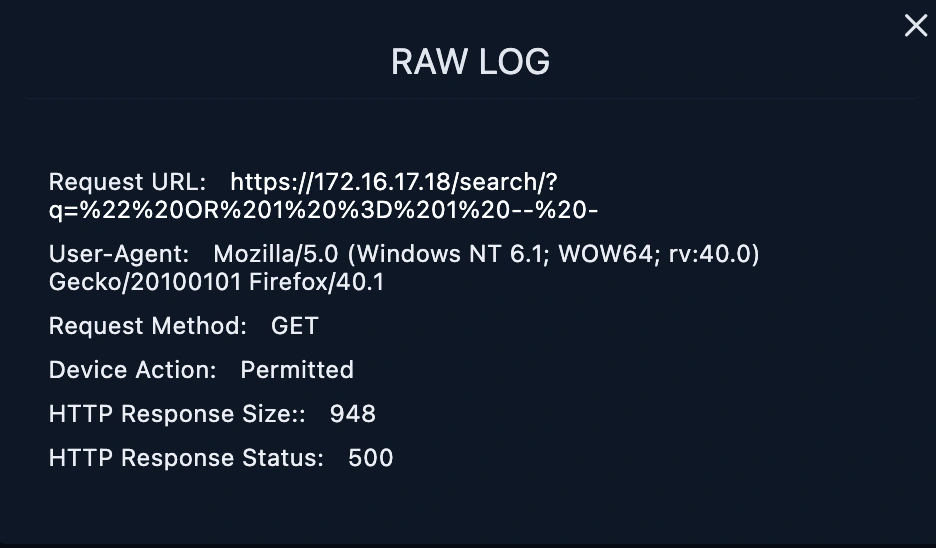
The malicious request URL from 167.99.169.17 was not successful because the log management showed HTTP response 500 means it countered the server error.
Findings:
SQL Injection Indicators:
Source of the Payload:
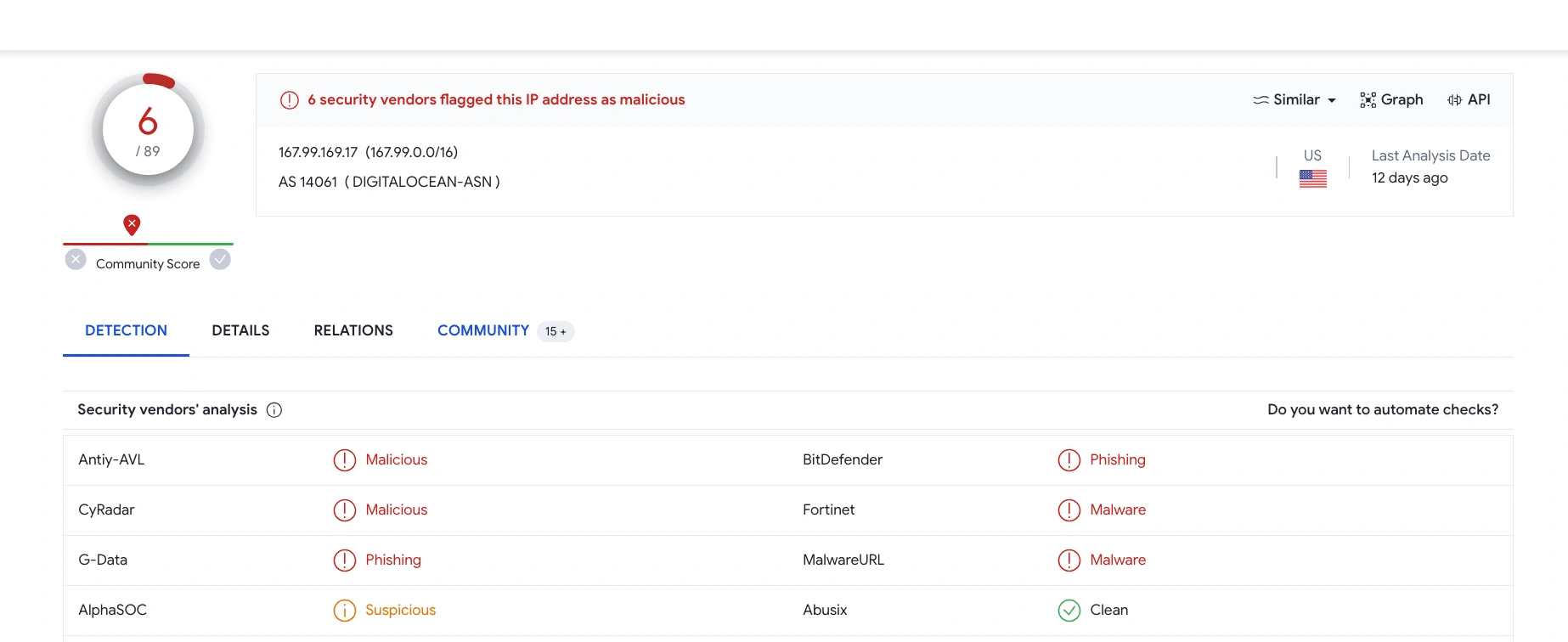
Virustotal
Mitigation and Response:
Isolation:
User Notification:
Recommendations:
Incident Documentation:
User Training:
Conclusion:
The incident was successfully mitigated through prompt detection, analysis, and response. Continuous monitoring and proactive security measures are essential to prevent SQL injection attacks and protect critical web applications.
Lesson Learned
We put the Requested URL into URL Decoding and find the payload sent by the attacker. After URL Decoding, it has been confirmed that it is SQL Injection. When we filtered by source address from the Log Management page, we saw other requests made. When the requests were examined, we saw that all of them were related to the SQL Injection vulnerability.
When the Response size of all requests is examined, it is seen that they are all the same and the response status is 500. The SQL Injection attack is unsuccessful, as there will be different response sizes and 200 response status, it seems that the attack was not successful.
Like this project
Posted Dec 5, 2023
The SOC detected a security event that detects the potential presence of a SQL injection payload on a server.



![EventID:116 [SOC166 - Javascript Code Detected in Requested URL]](https://media.contra.com/image/upload/w_400,q_auto:good,c_fill/project-cover-06_s9kkre.avif)