EventID:116 [SOC166 - Javascript Code Detected in Requested URL]
Table of contents
SOC - LetsDefend.io
This is a report on what I have done training at the SOC Analyst Fundamentals course on letsdefend.io. Letsdefend.io is a good platform for blue team training.
Javascript Code Detected in Requested URL Walkthrough.
SOC ANALYST REPORT
Incident Details:
Incident ID: Event ID: 116 - [SOC166 - Javascript Code Detected in Requested URL]
Date and Time of Detection: Feb, 26, 2022, 06:56 PM
Incident Severity: Medium
Incident Category: Web Attack
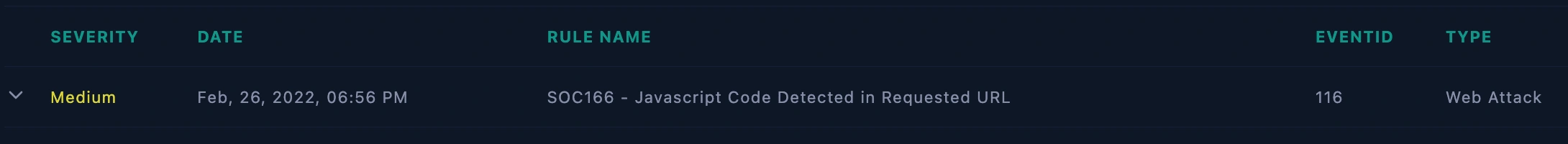
SIEM alert
Summary:
The SIEM simulation detected a security event (Event ID: 116 - [SOC166 - Javascript Code Detected in Requested URL] ) indicating the presence of Javascript code in a requested URL on host WebServer1002 ( 172.16.17.17 ). The attack was not successful due to the http server response code : 320 turns out to be a URL redirection. This report outlines the analysis, investigation, and mitigation steps taken.
Incident Description:
Upon analysis of the SIEM simulation, (Event ID: 116 - [SOC166 - Javascript Code Detected in Requested URL] ) triggered due to China attacker's ip address 112.85.42.13 has attempted to inject malicious java-script code or XSS Injection on the requested URL at host WebServer1002 ( 172.16.17.17 ). Hence the attack was not successful due to the http response : 320 turns out to be a URL redirection on the target website. The injection code was flagged as potentially malicious, warranting further investigation. Here's the full details on Cross site scripting XSS.
Cross-site scripting XSS attack is when the attacker to inject malicious codes into websites. This malicious code can affect other users that visits the targeted website such as stealing personal information or data breach. There are many types of XSS, it is better when the website developer has to follow secure coding practices and users should be careful about clicking links.
Investigation Steps:
Initial Triage:
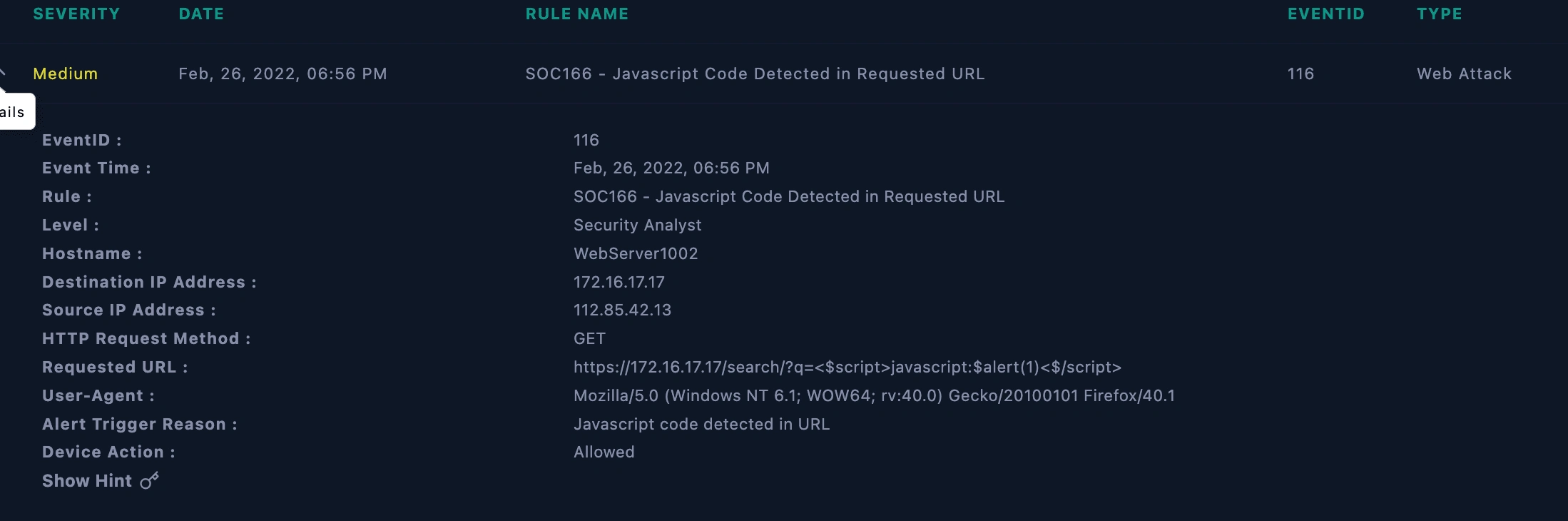
alert details
Traffic Analysis:
Examined network traffic logs to identify the source and destination of the suspicious URL.
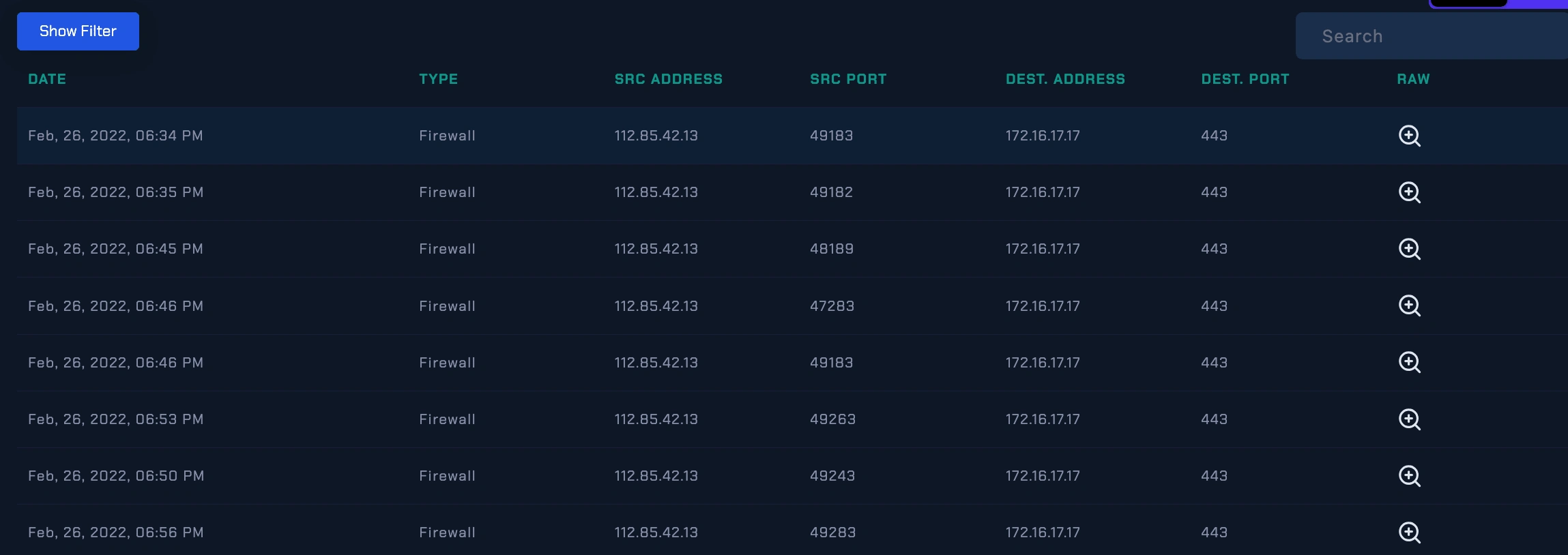
log management
The malicious (112.85.42.13) IP address tried to communicate with WebServer1002 (172.16.17.17) by requesting the following URL addresses;
https://172.16.17.17/search/?q=<$img%20src%20=q%20onerror=prompt(8)$>
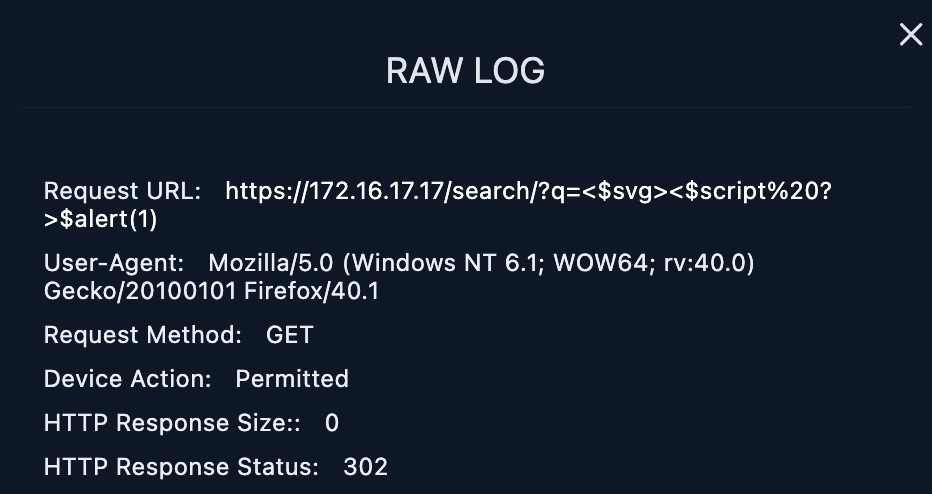
https://172.16.17.17/search/?q=<$svg><$script%20?>$alert(1)
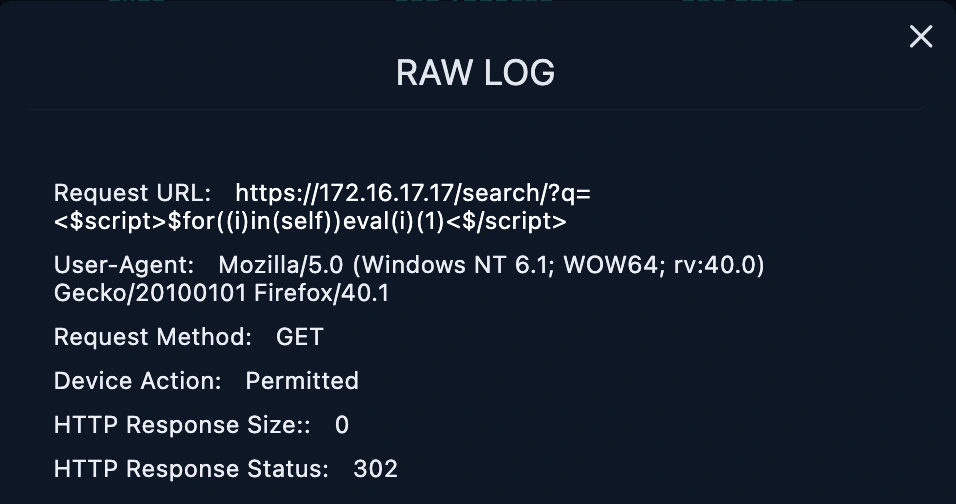
https://172.16.17.17/search/?q=<$script>$for((i)in(self))eval(i)(1)<$/script>
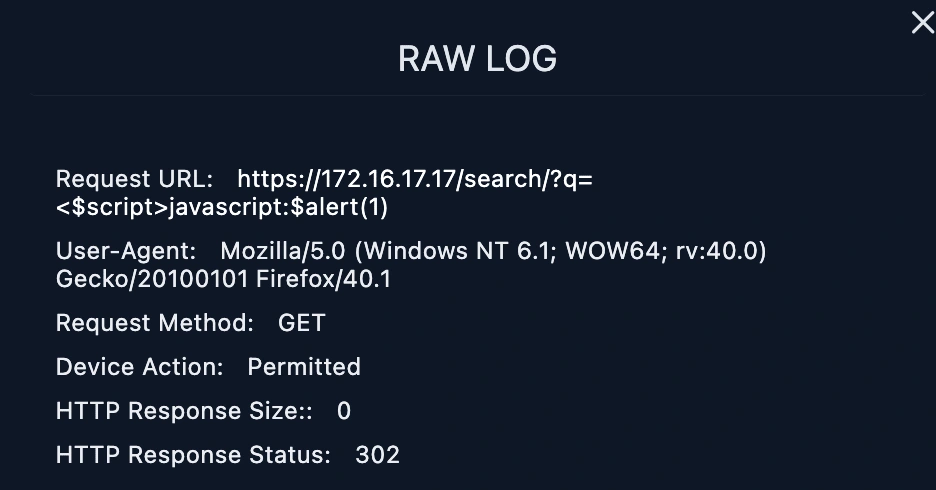
https://172.16.17.17/search/?q=<$script>javascript:$alert(1)<$/script>
The HTTP Response status is 302 meaning a common way of URL redirection and it returns error.
HTTP Response size is 0 meaning there's no data given during this attempt
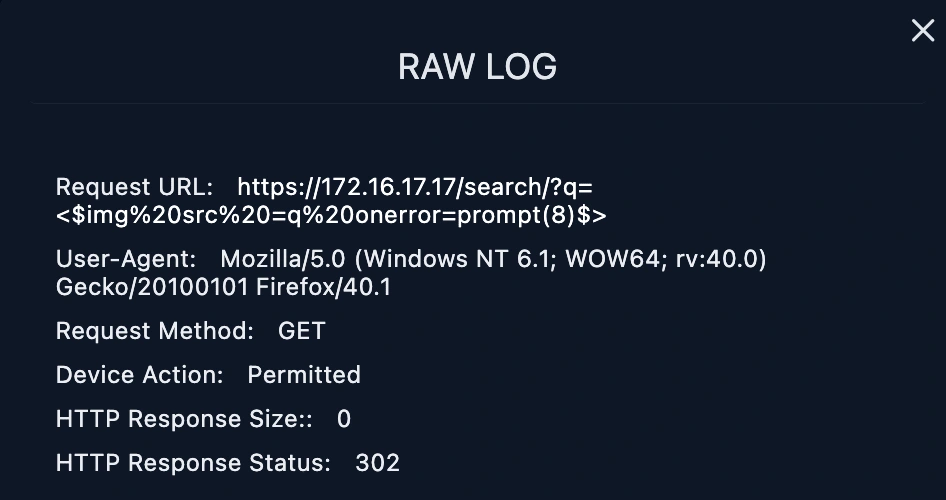
raw log details
raw log details
raw log details
raw log details
The use of “Log Management” to check if there is communication with a certain address and to see the details of this communication.
Logs are records of individual events or activities that occur within a system, and they often contain valuable information for troubleshooting, monitoring, and security purposes.
Code Analysis:
Extracted and analyzed the Javascript code from the URL.
The link URL starts with
https://172.16.17.17/search/?, which is a search bar functionality on the web app that's hosted at the targeted server WebServer1002 (172.16.17.17 ).The query parameter which is
q being used to pass the search query to the targeted server. The attacker puts malicious javascript code with a script tag <$script><$/script> inside this query parameter which is q=<$script>javascript:$alert(1)<$/script>. The
<$script><$/script> is for inserting a script tag.javascript:$alert(1) is the malicious javascript piece code that the attacker is trying to inject. It is attempt to execute the alert function which then displays a pop up alert box with the number "1".Output Analysis
As for the dynamic analysis we will be executing the malicious code inside a HTML compiler to view the output of this malicious code.
We will write the script inside the html code syntax and use the alert function.
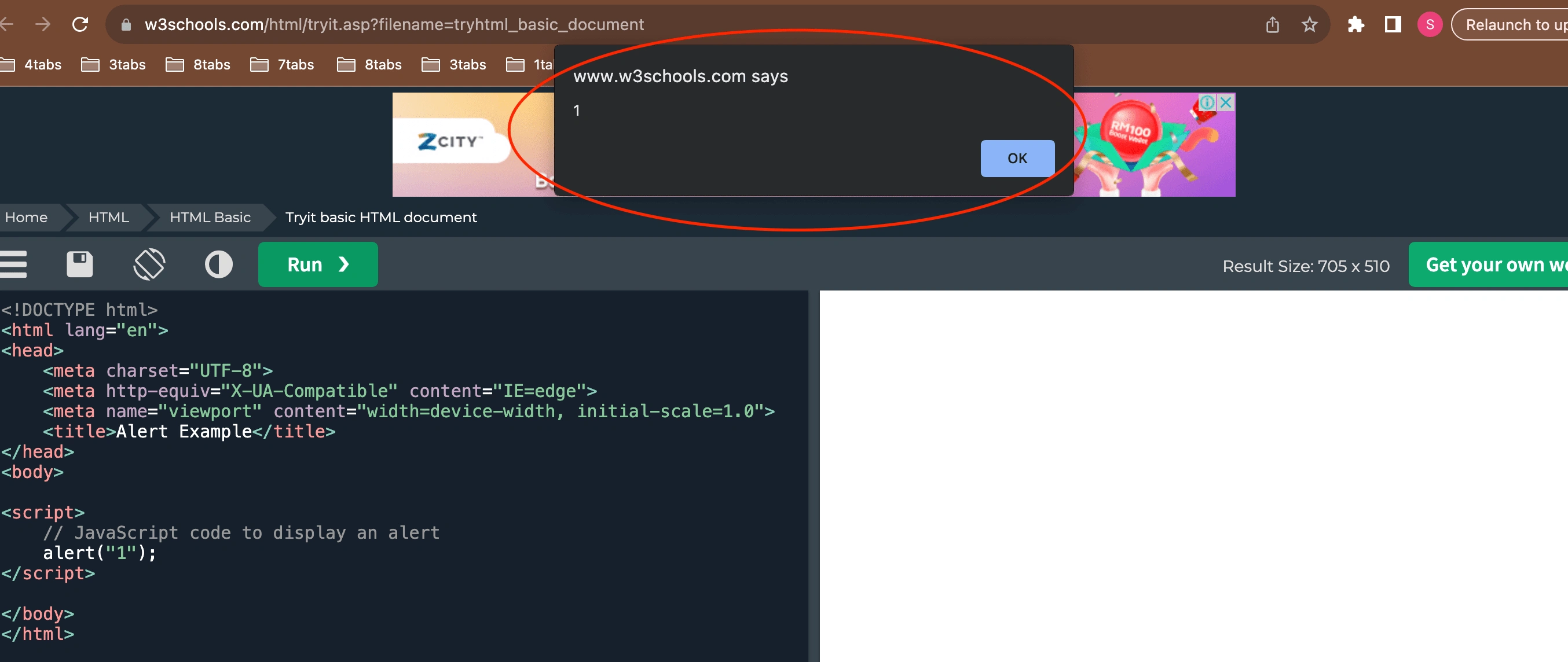
Alert box function
Endpoint Analysis:
Checked the affected endpoint for signs of compromise.
Findings:
Malicious Intent:
Source of the Code:
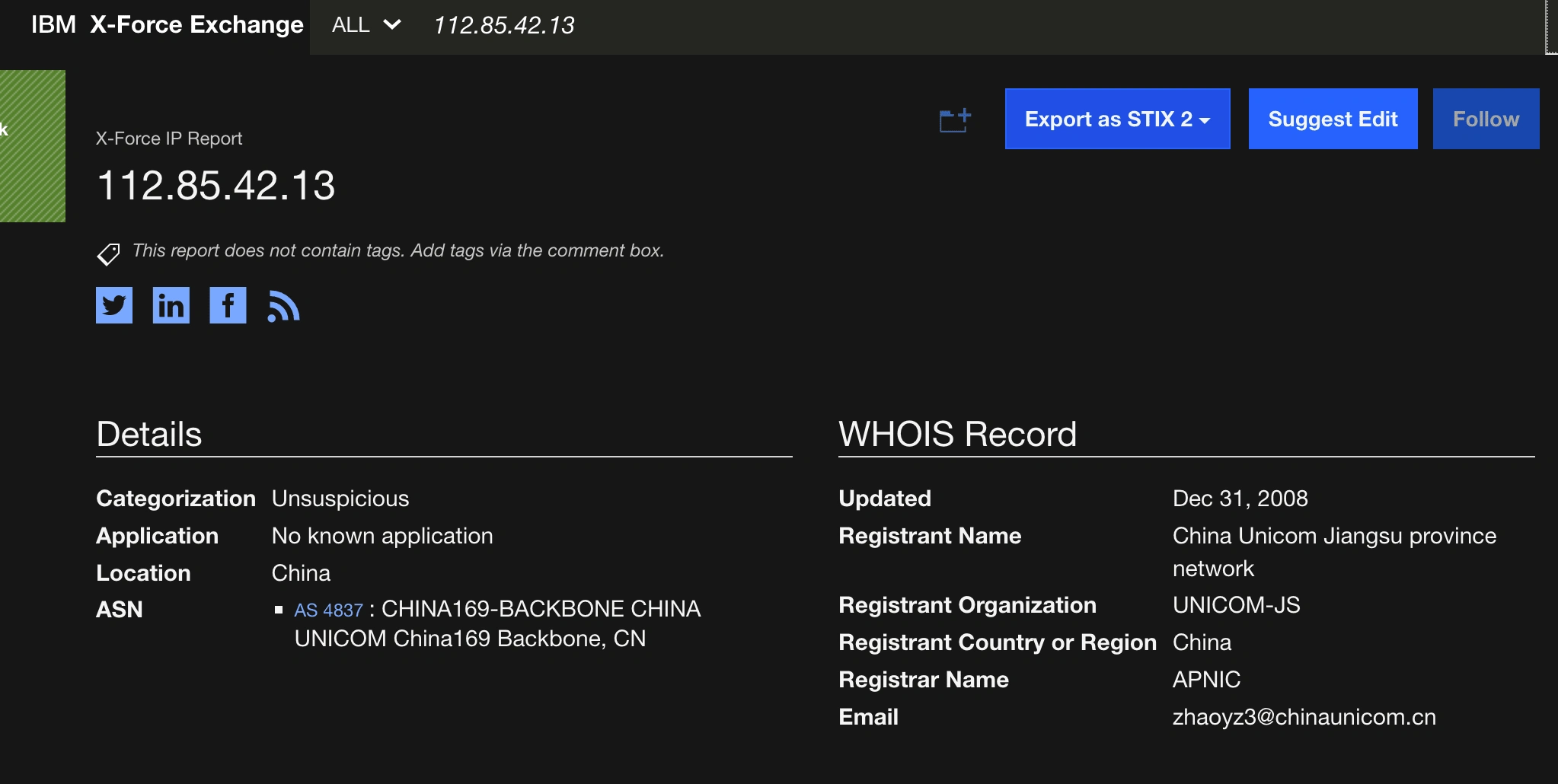
IBM X-Force Exchange
Mitigation and Response:
Isolation:
User Awareness:
Prevention:
Documentation:
Incident Documentation:
Lesson learned
When the q parameter is examined, we see that there is indeed an XSS payload. Since the payload is in the URL, it has been determined that it is a Reflected type XSS attack.
When we filter by source IP address on the Log Management page, we see that the attacker also tried different XSS payloads.
It was detected that the requests belonging to the attack were redirected with the 302 status code. For this reason, the attack was not successful.
Escalation to the next level is not required as the attack is not successful.
Conclusion:
The incident was successfully mitigated through prompt detection, analysis, and response. Tier 2 escalation is not needed. Continuous monitoring and proactive security measures are recommended to prevent similar incidents in the future.
Like this project
Posted Dec 6, 2023
Detected a security event indicating the presence of Javascript code in a requested URL. This report outlines the analysis, investigation and mitigation.



