SDLC Review & Security IntegrationDragos Moruz
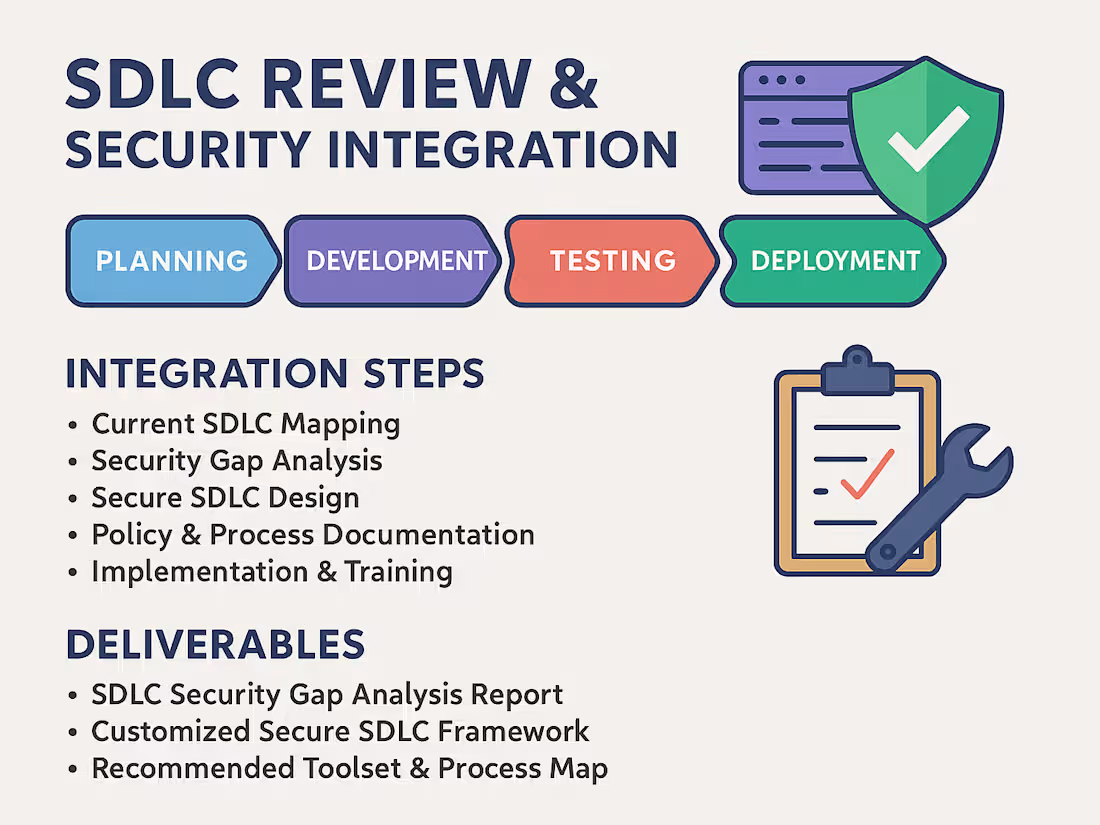
I offer a comprehensive review of your Software Development Life Cycle (SDLC) to integrate security best practices at every stage—from planning to deployment. This ensures your development process supports secure coding, early vulnerability detection, and compliance with standards like OWASP SAMM, NIST SSDF, and ISO 27034.
What's included
SDLC Security Gap Analysis Report
A detailed report identifying weaknesses in your current development process, mapped against industry standards like OWASP SAMM and NIST SSDF.
Customized Secure SDLC Framework
A tailored security-enhanced SDLC model built around your team’s workflows, technologies, and development methodology (Agile, DevOps, etc.).
Recommended Toolset & Process Map
A curated list of security tools (e.g., SAST, DAST, secrets scanning) and an implementation-ready process map for integrating them into your pipeline.
Developer Security Checklists & Guidance
Practical, easy-to-follow checklists and documentation for developers to follow secure coding practices at each phase of the SDLC.
Training Materials & Workshop Sessions (Optional)
Custom training decks or hands-on workshops to upskill developers, testers, and DevOps teams on integrating security into their daily work.
FAQs
Penetration testing happens late in the cycle. A secure SDLC helps embed security from the beginning, reducing rework and catching issues early—saving time and cost.
No. The review aligns security with your existing SDLC—whether Agile, DevOps, or Waterfall—by adding security practices within your current structure.
Yes. Based on your stack, I’ll recommend tools for SAST, DAST, dependency scanning, secret detection, etc., along with guidance on integration in CI/CD.
It can be either. Many clients begin with a one-time review and design, then engage for ongoing support, training, or tool tuning as needed.
Success is tracked through metrics like vulnerability reduction over releases, mean time to remediation, and developer adoption of secure practices.
Example work
Contact for pricing
Tags
Burp Suite
GitHub
Kali Linux
Oracle APEX
Solidity
Cloud Security Engineer
Security Engineer
Security Manager
Service provided by

Dragos Moruz Timișoara, Romania
- 5.00
- Rating
- 3
- Followers

SDLC Review & Security IntegrationDragos Moruz
Contact for pricing
Tags
Burp Suite
GitHub
Kali Linux
Oracle APEX
Solidity
Cloud Security Engineer
Security Engineer
Security Manager
I offer a comprehensive review of your Software Development Life Cycle (SDLC) to integrate security best practices at every stage—from planning to deployment. This ensures your development process supports secure coding, early vulnerability detection, and compliance with standards like OWASP SAMM, NIST SSDF, and ISO 27034.
What's included
SDLC Security Gap Analysis Report
A detailed report identifying weaknesses in your current development process, mapped against industry standards like OWASP SAMM and NIST SSDF.
Customized Secure SDLC Framework
A tailored security-enhanced SDLC model built around your team’s workflows, technologies, and development methodology (Agile, DevOps, etc.).
Recommended Toolset & Process Map
A curated list of security tools (e.g., SAST, DAST, secrets scanning) and an implementation-ready process map for integrating them into your pipeline.
Developer Security Checklists & Guidance
Practical, easy-to-follow checklists and documentation for developers to follow secure coding practices at each phase of the SDLC.
Training Materials & Workshop Sessions (Optional)
Custom training decks or hands-on workshops to upskill developers, testers, and DevOps teams on integrating security into their daily work.
FAQs
Penetration testing happens late in the cycle. A secure SDLC helps embed security from the beginning, reducing rework and catching issues early—saving time and cost.
No. The review aligns security with your existing SDLC—whether Agile, DevOps, or Waterfall—by adding security practices within your current structure.
Yes. Based on your stack, I’ll recommend tools for SAST, DAST, dependency scanning, secret detection, etc., along with guidance on integration in CI/CD.
It can be either. Many clients begin with a one-time review and design, then engage for ongoing support, training, or tool tuning as needed.
Success is tracked through metrics like vulnerability reduction over releases, mean time to remediation, and developer adoption of secure practices.
Example work
Contact for pricing