Firewall Configuration & Rule ReviewDragos Moruz
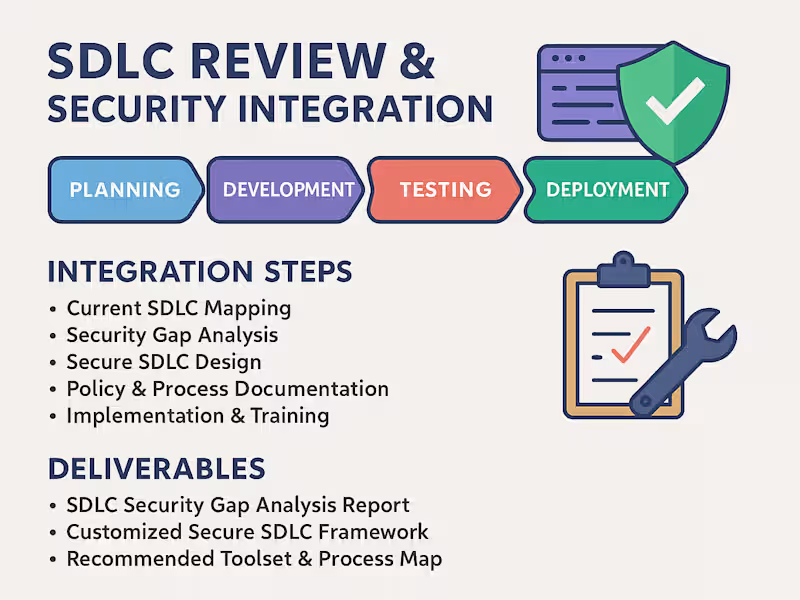
I provide in-depth firewall security assessments to evaluate rule sets, configuration practices, and overall posture across on-premises and cloud-based firewalls. This service ensures that your firewall is optimized to enforce least privilege, prevent unauthorized access, and align with security best practices such as CIS Benchmarks, NIST SP 800-41, and Zero Trust Architecture.
What's included
Applying industry standards
Firewall rule audit report with security findings and risk categorization
Optimization and support
Rule optimization recommendations and change planning support
Compliance alignment
Compliance alignment overview (CIS, NIST, Zero Trust principles)
Reporting
Executive summary and technical appendix for both leadership and engineering teams
FAQs
Even if your network appears secure, firewall rules can become outdated, overly permissive, or redundant over time. A review ensures rules follow least privilege principles, reduce your attack surface, and comply with security frameworks like CIS and NIST.
No. The firewall review is non-intrusive and based on configuration exports and documentation. There is no need to make live changes during the assessment, so your production systems remain unaffected.
You’ll receive a comprehensive report that includes:
A summary of current firewall posture
Identification of risky, unused, or misconfigured rules
Recommendations for optimization
Compliance alignment (e.g., CIS, Zero Trust)
Diagrams or visuals (if applicable)
Yes. I provide detailed remediation guidance and, if needed, hands-on support or collaboration with your network/security team to safely implement changes. I also offer validation testing after changes are made.
Example work
Contact for pricing
Tags
Burp Suite
Kali Linux
Oracle APEX
Solidity
Wireshark
Cloud Security Engineer
Security Engineer
Security Manager
Service provided by

Dragos Moruz Timișoara, Romania
- 5.00
- Rating
- 3
- Followers

Firewall Configuration & Rule ReviewDragos Moruz
Contact for pricing
Tags
Burp Suite
Kali Linux
Oracle APEX
Solidity
Wireshark
Cloud Security Engineer
Security Engineer
Security Manager
I provide in-depth firewall security assessments to evaluate rule sets, configuration practices, and overall posture across on-premises and cloud-based firewalls. This service ensures that your firewall is optimized to enforce least privilege, prevent unauthorized access, and align with security best practices such as CIS Benchmarks, NIST SP 800-41, and Zero Trust Architecture.
What's included
Applying industry standards
Firewall rule audit report with security findings and risk categorization
Optimization and support
Rule optimization recommendations and change planning support
Compliance alignment
Compliance alignment overview (CIS, NIST, Zero Trust principles)
Reporting
Executive summary and technical appendix for both leadership and engineering teams
FAQs
Even if your network appears secure, firewall rules can become outdated, overly permissive, or redundant over time. A review ensures rules follow least privilege principles, reduce your attack surface, and comply with security frameworks like CIS and NIST.
No. The firewall review is non-intrusive and based on configuration exports and documentation. There is no need to make live changes during the assessment, so your production systems remain unaffected.
You’ll receive a comprehensive report that includes:
A summary of current firewall posture
Identification of risky, unused, or misconfigured rules
Recommendations for optimization
Compliance alignment (e.g., CIS, Zero Trust)
Diagrams or visuals (if applicable)
Yes. I provide detailed remediation guidance and, if needed, hands-on support or collaboration with your network/security team to safely implement changes. I also offer validation testing after changes are made.
Example work
Contact for pricing