Penetration Testing & Cybersecurity Services for Your BusinessDragos Moruz
Penetration testing services aligned with OWASP Top 10 standards to identify and mitigate vulnerabilities in web apps, mobile apps, APIs, and IT infrastructure. My testing approach uncovers critical risks, including misconfigurations to strengthen your security posture.
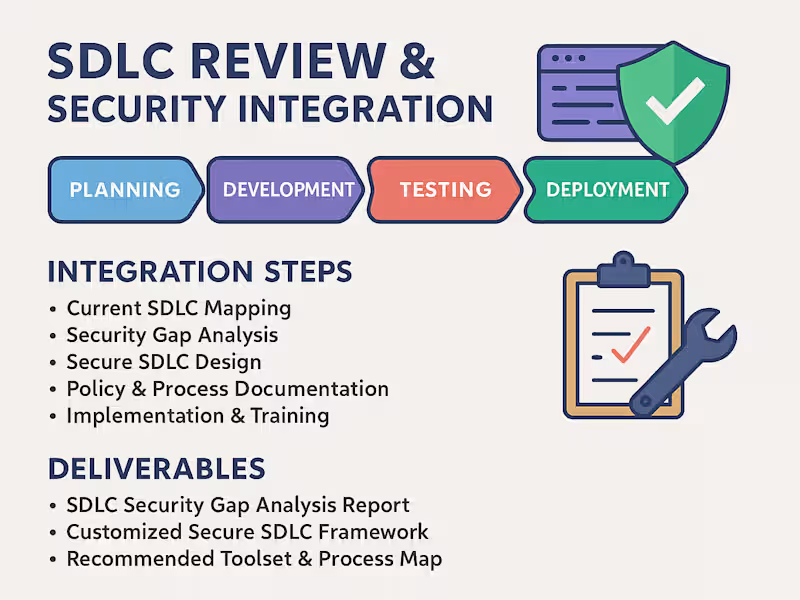
What's included
Expert Penetration Testing & Cybersecurity Services to Secure Your Business
Penetration testing services aligned with OWASP Top 10 standards to identify and mitigate vulnerabilities in web apps, mobile apps, APIs, and IT infrastructure. My testing approach uncovers critical risks, including misconfigurations to strengthen your security posture.
Web Application Testing
Detect OWASP Top 10 vulnerabilities like SQL Injection, XSS, and Broken Authentication.
Assess logic flaws, session handling, and input validation.
Mobile Application Testing
Analyze data encryption, API calls, and test for reverse engineering risks.
Evaluate insecure data transmission vulnerabilities.
API Security Testing
Review authentication, authorization, and data exposure for REST and SOAP APIs.
Test rate-limiting, security headers, and input validation.
Infrastructure Testing
Perform network scans, port analysis, and firewall rule reviews.
Assess VPNs and intrusion detection systems for weaknesses.
Deliverables
Comprehensive Reports with risks, vulnerabilities, and proofs of concept.
Remediation Plans with actionable fixes.
Compliance Mapping (OWASP, CIS, NIST).
Retesting Support to validate fixes.
Perfect for businesses seeking secure and compliant applications!
FAQs
Yes, delivery time and details can be different by the size of the project.
Yes. This includes both, Android and iOS. For some of the applications it is possible to ask the client to remove the SSL Pin.
Usually, an ecommerce website it's roughly 4+1. 4 days testing 1 day reporting.
API tests are scoped based on the number of functions the API has and the by the type of calls are made e.g GET/POST/PUT etc.
Yes, I can perform cloud reviews as well for Azure, AWS, MS365 etc.
Yes, I perform both external and internal infrastructure penetration testing to identify vulnerabilities such as open ports, misconfigurations, weak credentials, and firewall issues—simulating real-world attacks to strengthen your security posture.
Yes, I conduct firewall reviews to identify misconfigurations, validate rule sets, assess VPN and NAT settings, and ensure alignment with security best practices and compliance requirements.
Contact for pricing
Tags
Burp Suite
Chainlink
Docker
Oracle APEX
Solidity
Cybersecurity Specialist
Security Engineer
Security Manager
Service provided by

Dragos Moruz Timișoara, Romania
- 5.00
- Rating
- 3
- Followers

Penetration Testing & Cybersecurity Services for Your BusinessDragos Moruz
Contact for pricing
Tags
Burp Suite
Chainlink
Docker
Oracle APEX
Solidity
Cybersecurity Specialist
Security Engineer
Security Manager
Penetration testing services aligned with OWASP Top 10 standards to identify and mitigate vulnerabilities in web apps, mobile apps, APIs, and IT infrastructure. My testing approach uncovers critical risks, including misconfigurations to strengthen your security posture.
What's included
Expert Penetration Testing & Cybersecurity Services to Secure Your Business
Penetration testing services aligned with OWASP Top 10 standards to identify and mitigate vulnerabilities in web apps, mobile apps, APIs, and IT infrastructure. My testing approach uncovers critical risks, including misconfigurations to strengthen your security posture.
Web Application Testing
Detect OWASP Top 10 vulnerabilities like SQL Injection, XSS, and Broken Authentication.
Assess logic flaws, session handling, and input validation.
Mobile Application Testing
Analyze data encryption, API calls, and test for reverse engineering risks.
Evaluate insecure data transmission vulnerabilities.
API Security Testing
Review authentication, authorization, and data exposure for REST and SOAP APIs.
Test rate-limiting, security headers, and input validation.
Infrastructure Testing
Perform network scans, port analysis, and firewall rule reviews.
Assess VPNs and intrusion detection systems for weaknesses.
Deliverables
Comprehensive Reports with risks, vulnerabilities, and proofs of concept.
Remediation Plans with actionable fixes.
Compliance Mapping (OWASP, CIS, NIST).
Retesting Support to validate fixes.
Perfect for businesses seeking secure and compliant applications!
FAQs
Yes, delivery time and details can be different by the size of the project.
Yes. This includes both, Android and iOS. For some of the applications it is possible to ask the client to remove the SSL Pin.
Usually, an ecommerce website it's roughly 4+1. 4 days testing 1 day reporting.
API tests are scoped based on the number of functions the API has and the by the type of calls are made e.g GET/POST/PUT etc.
Yes, I can perform cloud reviews as well for Azure, AWS, MS365 etc.
Yes, I perform both external and internal infrastructure penetration testing to identify vulnerabilities such as open ports, misconfigurations, weak credentials, and firewall issues—simulating real-world attacks to strengthen your security posture.
Yes, I conduct firewall reviews to identify misconfigurations, validate rule sets, assess VPN and NAT settings, and ensure alignment with security best practices and compliance requirements.
Contact for pricing