Security Testing for iOS and Android Mobile ApplicationsDragos Moruz
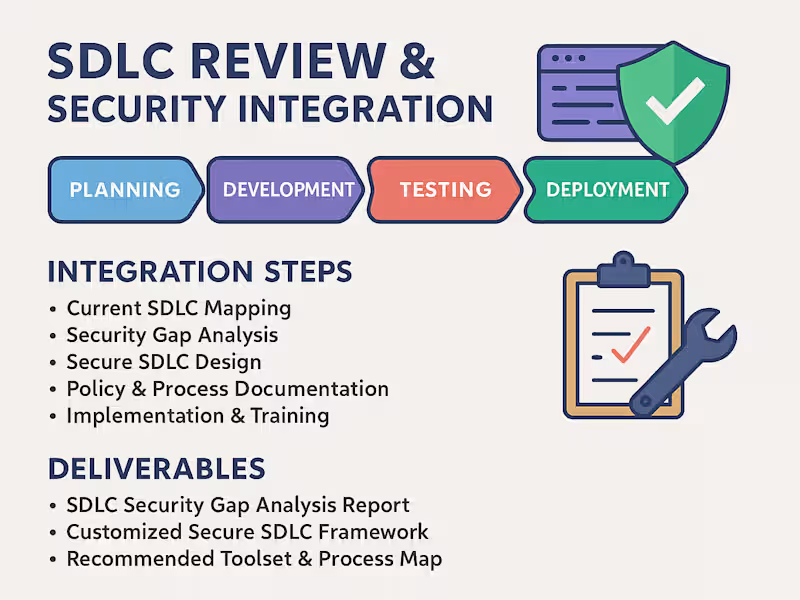
I provide comprehensive cybersecurity solutions designed to safeguard your applications, networks, APIs, and cloud environments from modern cyber threats. With expertise in automated vulnerability scanning, manual penetration testing, and cloud security assessments, I ensure your systems comply with industry standards like CIS Benchmarks, OWASP Top 10, NIST, and ISO 27001.
What's included
Security testing for iOS and Android mobile applications
I provide end-to-end security testing for iOS and Android mobile applications to identify vulnerabilities and strengthen app security. My approach includes testing for data leakage, insecure storage, API vulnerabilities, and encryption flaws, ensuring compliance with OWASP Mobile Top 10 standards.
Whether you’re launching a new app or improving an existing one, I deliver manual and automated assessments to secure sensitive data, protect user privacy, and prevent unauthorized access.
Key Deliverables Include
-Detailed vulnerability reports with severity ratings.
-Proofs of Concept (PoC) demonstrating identified weaknesses.
-Actionable remediation plans to fix vulnerabilities.
-Retesting support to validate fixes and improvements.
Secure your mobile app today and provide users with trust and confidence!
Cybersecurity Regulation
NIST Cybersecurity Framework, PCI DSS
FAQs
I test for data leaks, insecure storage, API vulnerabilities, weak encryption, reverse engineering risks, and insecure network communication following OWASP Mobile Top 10 standards.
Testing is done using a combination of manual techniques and automated tools to simulate real-world attacks, covering source code analysis, network communication, and API behavior.
No, testing is performed in staging or test environments to ensure it doesn’t disrupt production systems. (Testing is invasive if it's in production.)
Yes! I provide remediation guidance and retesting support to validate fixes and improvements.
Timelines depend on the scope and complexity of the application. A typical test takes 5–10 business days, but this may vary based on requirements.
Contact for pricing
Tags
Acunetix
Cybersecurity Specialist
Mobile Engineer
Security Manager
Service provided by

Dragos Moruz Timișoara, Romania
- 5.00
- Rating
- 3
- Followers

Security Testing for iOS and Android Mobile ApplicationsDragos Moruz
Contact for pricing
Tags
Acunetix
Cybersecurity Specialist
Mobile Engineer
Security Manager
I provide comprehensive cybersecurity solutions designed to safeguard your applications, networks, APIs, and cloud environments from modern cyber threats. With expertise in automated vulnerability scanning, manual penetration testing, and cloud security assessments, I ensure your systems comply with industry standards like CIS Benchmarks, OWASP Top 10, NIST, and ISO 27001.
What's included
Security testing for iOS and Android mobile applications
I provide end-to-end security testing for iOS and Android mobile applications to identify vulnerabilities and strengthen app security. My approach includes testing for data leakage, insecure storage, API vulnerabilities, and encryption flaws, ensuring compliance with OWASP Mobile Top 10 standards.
Whether you’re launching a new app or improving an existing one, I deliver manual and automated assessments to secure sensitive data, protect user privacy, and prevent unauthorized access.
Key Deliverables Include
-Detailed vulnerability reports with severity ratings.
-Proofs of Concept (PoC) demonstrating identified weaknesses.
-Actionable remediation plans to fix vulnerabilities.
-Retesting support to validate fixes and improvements.
Secure your mobile app today and provide users with trust and confidence!
Cybersecurity Regulation
NIST Cybersecurity Framework, PCI DSS
FAQs
I test for data leaks, insecure storage, API vulnerabilities, weak encryption, reverse engineering risks, and insecure network communication following OWASP Mobile Top 10 standards.
Testing is done using a combination of manual techniques and automated tools to simulate real-world attacks, covering source code analysis, network communication, and API behavior.
No, testing is performed in staging or test environments to ensure it doesn’t disrupt production systems. (Testing is invasive if it's in production.)
Yes! I provide remediation guidance and retesting support to validate fixes and improvements.
Timelines depend on the scope and complexity of the application. A typical test takes 5–10 business days, but this may vary based on requirements.
Contact for pricing