SDLC Security Integration and Review
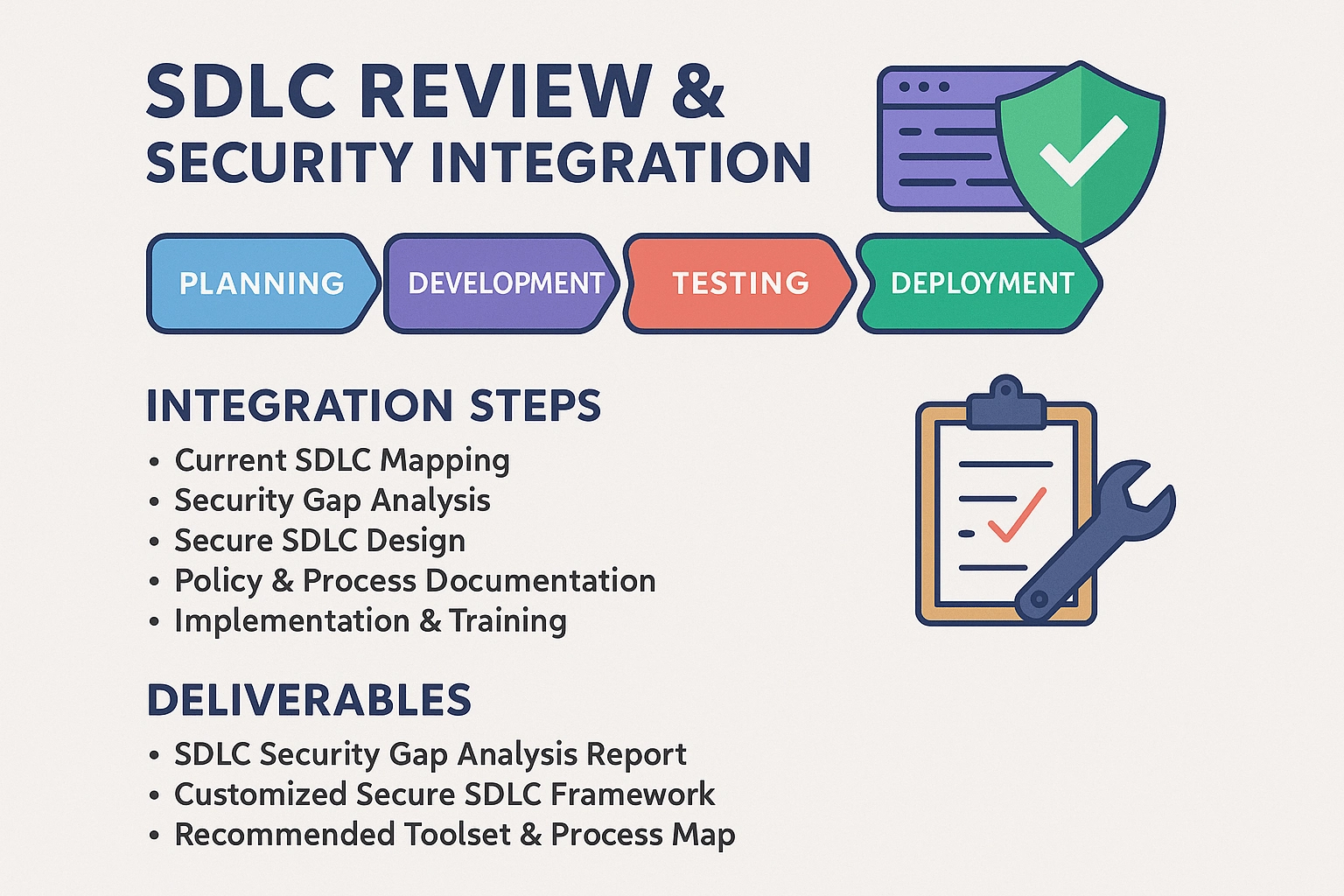
🔄 SDLC Review & Security Integration
I offer a comprehensive review of your Software Development Life Cycle (SDLC) to integrate security best practices at every stage—from planning to deployment. This ensures your development process supports secure coding, early vulnerability detection, and compliance with standards like OWASP SAMM, NIST SSDF, and ISO 27034.
🧭 Process
1. Current SDLC Mapping
Review your existing SDLC phases (Waterfall, Agile, DevOps, etc.)
Identify key stakeholders, tools, and workflows used across development, testing, and deployment
2. Security Gap Analysis
Assess current security controls and checkpoints (e.g., code review, SAST/DAST tools)
Identify missing or weak security touchpoints across each SDLC phase
Evaluate alignment with frameworks like OWASP SAMM or NIST Secure Software Development Framework (SSDF)
3. Secure SDLC Design
Propose enhancements: threat modeling, secure coding guidelines, automated scanning, security gates in CI/CD
Recommend tools and practices for each stage: requirements, design, coding, testing, release, and maintenance
4. Policy & Process Documentation
Document secure SDLC workflows and approval processes
Develop security checklists, developer guidance, and review protocols
5. Implementation & Training (Optional)
Support tool integration (e.g., SAST in CI pipelines)
Conduct workshops or training for dev, QA, and security teams
📄 Deliverables
SDLC Security Gap Analysis Report
Customized Secure SDLC Framework tailored to your team and tooling
Recommended toolset and process map
Developer-friendly security checklists and guidance
Training materials or workshop sessions (if included)

CRUSADER NETWORK
Like this project
Posted May 5, 2025
Integrated security into every phase of the SDLC, enhancing development workflows with proactive controls and secure coding best practices.
Likes
1
Views
14
Timeline
May 5, 2025 - Ongoing








