Automated Vulnerability Scanning - Discover & Secure QuicklyDragos Moruz
I provide comprehensive cybersecurity solutions designed to safeguard your applications, networks, APIs, and cloud environments from modern cyber threats. With expertise in automated vulnerability scanning, manual penetration testing, and cloud security assessments, I ensure your systems comply with industry standards like CIS Benchmarks, OWASP Top 10, NIST, and ISO 27001.
What's included
🔐 Key Services Offered
I offer comprehensive automated vulnerability scanning services using Nessus and Burp Suite to identify and remediate security weaknesses across infrastructure, applications, and networks.
🖧 Network and Infrastructure Scanning (Nessus)
Automated vulnerability assessments for servers, endpoints, and network devices
Compliance checks based on industry standards (e.g., CIS Benchmarks, NIST)
Configuration auditing and patch verification
🌐 Web Application Security Testing (Burp Suite)
Scan web applications for OWASP Top 10 vulnerabilities
Identify SQL injection, XSS, CSRF, and authentication flaws
Perform manual and automated analysis to ensure secure coding practices
Cloud Security Review (MS365 & Azure)
Assess cloud configurations against CIS Benchmarks for Microsoft 365 and Azure
Review identity and access management, data security, and logging practices
Provide detailed reports and remediation steps for compliance gaps
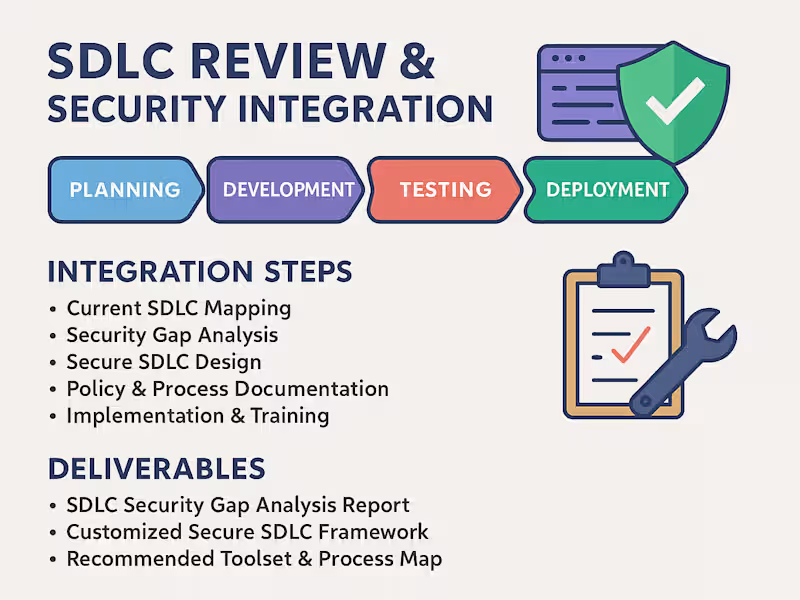
Deliverables
Detailed vulnerability assessment reports
Risk prioritization and remediation guidelines
Compliance status and audit-ready documentation
FAQs
Automated vulnerability scanning is a process that uses tools to detect security weaknesses in systems, applications, and networks by identifying misconfigurations, outdated software, and vulnerabilities.
It detects vulnerabilities such as SQL injection, cross-site scripting (XSS), misconfigurations, weak encryption, unpatched software, and insecure authentication mechanisms.
Automated scans are effective for identifying common vulnerabilities but may produce false positives or miss complex logical flaws, which is why manual testing is often recommended as a follow-up.
The duration depends on the size and complexity of the target environment. Small web applications may take a few hours, while larger infrastructures could take several days.
You'll receive a detailed report outlining detected vulnerabilities, risk ratings, proofs of concept, and remediation recommendations to fix the issues.
Contact for pricing
Tags
Burp Suite
Chainlink
Docker
Oracle APEX
Solidity
Cloud Security Engineer
Security Engineer
Security Manager
Service provided by

Dragos Moruz Timișoara, Romania
- 5.00
- Rating
- 3
- Followers

Automated Vulnerability Scanning - Discover & Secure QuicklyDragos Moruz
Contact for pricing
Tags
Burp Suite
Chainlink
Docker
Oracle APEX
Solidity
Cloud Security Engineer
Security Engineer
Security Manager
I provide comprehensive cybersecurity solutions designed to safeguard your applications, networks, APIs, and cloud environments from modern cyber threats. With expertise in automated vulnerability scanning, manual penetration testing, and cloud security assessments, I ensure your systems comply with industry standards like CIS Benchmarks, OWASP Top 10, NIST, and ISO 27001.
What's included
🔐 Key Services Offered
I offer comprehensive automated vulnerability scanning services using Nessus and Burp Suite to identify and remediate security weaknesses across infrastructure, applications, and networks.
🖧 Network and Infrastructure Scanning (Nessus)
Automated vulnerability assessments for servers, endpoints, and network devices
Compliance checks based on industry standards (e.g., CIS Benchmarks, NIST)
Configuration auditing and patch verification
🌐 Web Application Security Testing (Burp Suite)
Scan web applications for OWASP Top 10 vulnerabilities
Identify SQL injection, XSS, CSRF, and authentication flaws
Perform manual and automated analysis to ensure secure coding practices
Cloud Security Review (MS365 & Azure)
Assess cloud configurations against CIS Benchmarks for Microsoft 365 and Azure
Review identity and access management, data security, and logging practices
Provide detailed reports and remediation steps for compliance gaps
Deliverables
Detailed vulnerability assessment reports
Risk prioritization and remediation guidelines
Compliance status and audit-ready documentation
FAQs
Automated vulnerability scanning is a process that uses tools to detect security weaknesses in systems, applications, and networks by identifying misconfigurations, outdated software, and vulnerabilities.
It detects vulnerabilities such as SQL injection, cross-site scripting (XSS), misconfigurations, weak encryption, unpatched software, and insecure authentication mechanisms.
Automated scans are effective for identifying common vulnerabilities but may produce false positives or miss complex logical flaws, which is why manual testing is often recommended as a follow-up.
The duration depends on the size and complexity of the target environment. Small web applications may take a few hours, while larger infrastructures could take several days.
You'll receive a detailed report outlining detected vulnerabilities, risk ratings, proofs of concept, and remediation recommendations to fix the issues.
Contact for pricing