UX Competitive analysis: Cybersecurity Training for users
MY ROLE
As a product manager intern, I was hired to work with other teams on the product. I worked with the engineering team, stakeholders, and product management team to expand the product vision. I managed the development as it passed through some stages of vision, research, user interview, and pitch.
It was a remote-based team.

UNDERSTANDING THE PRODUCT
Due to a lack of cybersecurity awareness, people often overlook the risk of being hacked. The product will help users to be up-to-date with current information on security risks in a simple and continuous way. The product keeps the conversation going by delivering cybersecurity information as it happens, correlated with current real impact. It helps your team understand cybersecurity risks with a simple summary and personal context, not just raw numbers.
My research included:
Gauging the product's strengths and weaknesses,
Identifying areas of improvement that can only be discovered through user research,
Informing the design process,
and revealing the biggest gaps across the entire market when it comes to features or functionalities
RESEARCH PROCESS
The research process includes competitive analysis research as well as user interview.
Competitive analysis report
Competitive analysis for UX research focuses on the similarities and differences between the user experience of your product or service compared to a competitor’s product.
The four websites selected for the competitive analysis are considered indirect competitors because they solve similar problems for the same target market with different products and services.
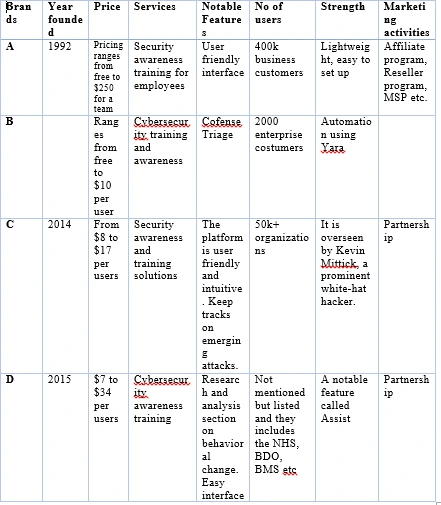
Table showing the features of cybersecurity training websites
These cybersecurity awareness companies have a strong and established reputation within the industry and a brand recognition that is trusted by potential customers. These websites have a more extensive library of content, including courses, tutorials, and resources that have been built up over time. These established websites have a larger user base compared to the new product I was working on. Also, there's a presence of established and sophisticated learning analytics tools that provides detailed insights into user progress and performance.
Product C, for example, is being overseen by Kevin Mitnick, a renowned white-hat hacker who rose to infamy when he was the FBI’s most wanted hacker in the 90s. His cybersecurity course can also be seen on the website. Product D, on the other hand, embraces user behavioral research to focus on changing user behavior through technology.
However, the product also has its potential, such as the ability to use more modern technology, incorporate the latest learning methods, and appeal to specific niche audiences.
User Interview
After the competitive analysis report, the next step I took was to carry out an open user interview to get the users' opinions of the product. Ten people were reached out to and three out of these ten had no idea what cybersecurity awareness and training was all about and this helped to streamline the target market. Based on the user interviews conducted with 7 users on the product, the following issues were identified:
65% wanted the training to be an upgrade to current knowledge on cybersecurity and also enlightening
39% desired that the training to increase employees’ awareness of cyberattacks and cybercrime
85% preferred the training to be conducted on different platforms so it can be accessible to almost everyone on their teams
93% recommended a user-friendly app that’ll be easy to use
69% wanted to get the training a few days a week.
RESULT AND TAKEAWAY
The research has shown that the product has the potential to be an effective tool for improving cybersecurity skills and knowledge among individuals and organizations. The evaluation of the product's features includes;
Making it user-friendly and accessible to a broad range of users including those with little or no cybersecurity experience.
Also, there should be continual improvement in the functionality of the product.
Enhancing the adaptability of the product to the evolving cybersecurity landscape.
Integrating social learning features to encourage collaboration and knowledge sharing.
Further testing and evaluation to ensure its ongoing effectiveness and relevance
Like this project
Posted Feb 14, 2023
A competitive analysis report was conducted for a cybersecurity training website and it includes a SWOT analysis of each company and its product.
Likes
0
Views
12