Blockchain Security Demystified
Protecting Data in a Connected World
Introduction
The digital world is rapidly evolving, and with it comes an unprecedented level of connectivity and globalization. We are more connected than ever, with our digital identities spanning across social networks, e-commerce platforms, and online services. However, this increased connectedness also brings heightened risks, making it harder to safeguard our digital footprints online. Blockchain technology has emerged as a revolutionary solution, offering unparalleled security benefits to address these modern challenges.
What You’ll Learn
In this paper, we’ll explore:
What blockchain is and how it works
Key features that make blockchain a game-changer for security
Real-world use cases in supply chain, IoT, identity, and finance
The Collective Notebook
Imagine a "community notebook" where everyone in a village writes down important events on their own personal copy of the notebook. If one person tries to change the story or rewrite a past event, everyone else in the village can point to their own copy to prove what was originally written. The only way to change the story would be to convince more than half of the villagers to change their copies as well — an almost impossible task. This "community notebook" represents the blockchain, where each page is a block, the chain links the pages together, and the whole village acts as a decentralized network that agrees on what’s true.
Now that we've visualized blockchain through the community notebook metaphor, let's take a closer look at the mechanics behind this technology.
The Mechanics of Blockchain
Blockchain is a distributed ledger technology (DLT) that enables secure, transparent, and tamper-proof record-keeping. Unlike traditional centralized databases, blockchain operates on a decentralized network of nodes, each maintaining a synchronized copy of the ledger. Changes to the ledger are validated through a consensus mechanism, ensuring that no single entity can alter records without the agreement of the network.
Centralized vs Decentralized Network
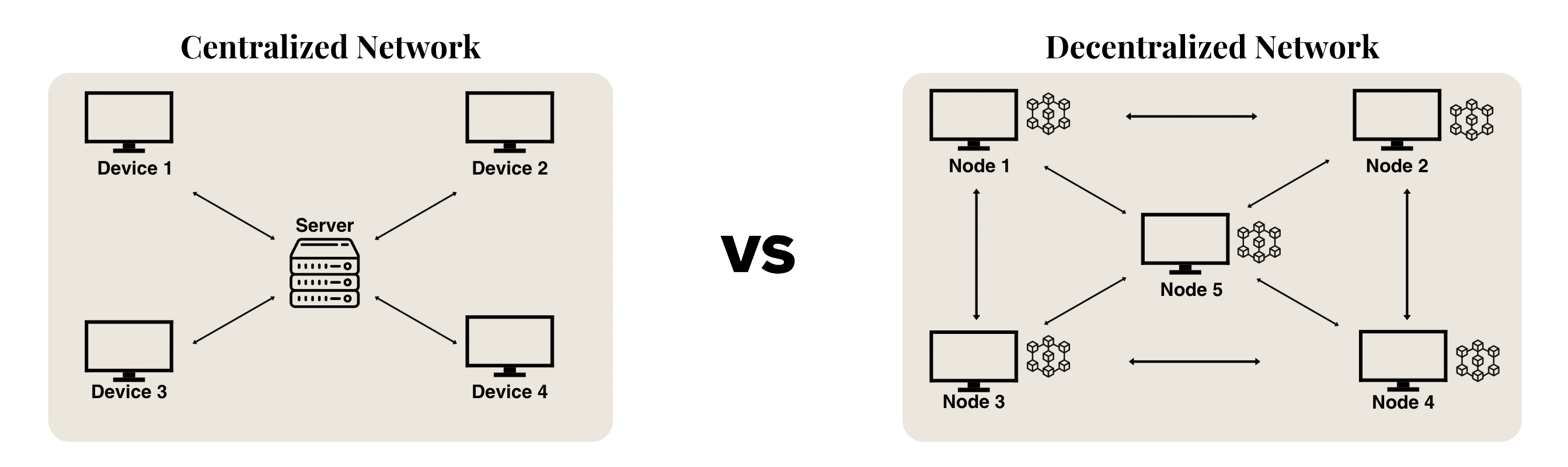
How devices exist between different networks
How a Transaction is Added to the Blockchain
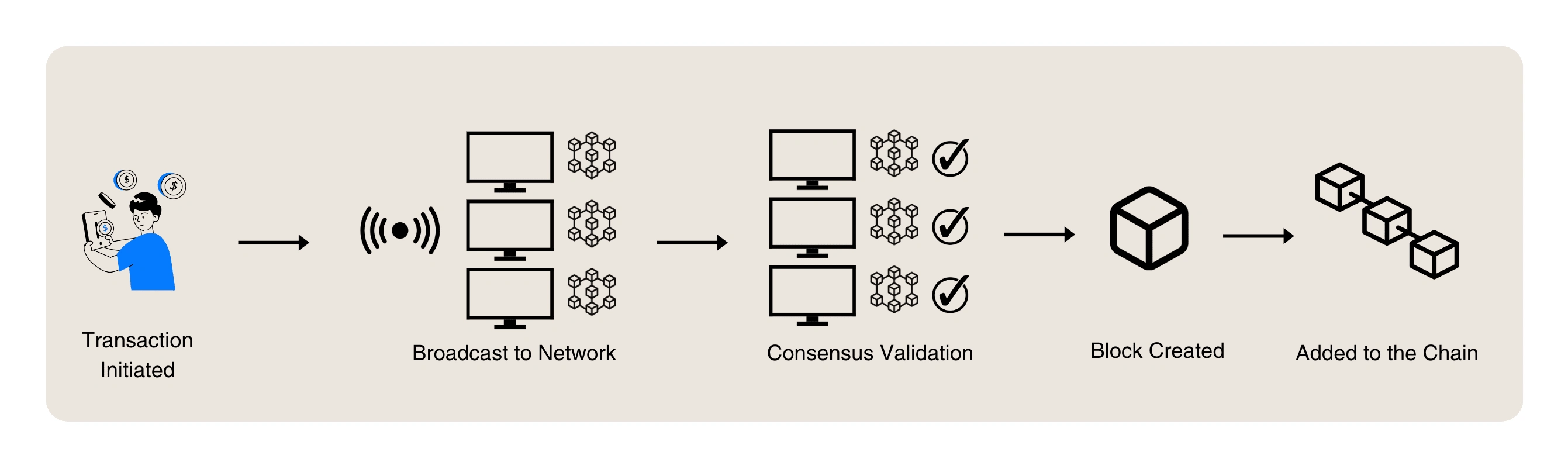
Building blocks of blockchain
Key Components of Blockchain
Blocks: Data packages containing transaction records, timestamps, and a unique cryptographic hash.
Chain: Blocks are linked together in a sequential, immutable chain.
Decentralization: No single entity controls the network; it’s maintained by a distributed network of nodes.
Consensus Mechanisms: Algorithms (like Proof of Work or Proof of Stake) that ensure agreement on changes to the blockchain.
Cryptographic Hashing: A method to encode data into a unique, fixed-length string, making it practically impossible to alter data without detection.
The Security Power of Blockchain
Blockchain’s architecture provides robust security features that address key vulnerabilities in traditional systems.
Immutability
Once data is recorded on the blockchain, it cannot be changed or deleted. This immutability ensures that records remain accurate and verifiable over time. In security terms, this means:
Tamper-resistance: Hackers cannot alter past records without consensus from the majority of nodes.
Audit trails: Every change is permanently recorded, providing a clear history of data changes.
Decentralization
Unlike centralized systems that rely on a single point of control, blockchain operates on a distributed network, reducing the attack surface for bad actors.
No single point of failure: Without a central server to target, cyberattacks are significantly harder to execute.
Resilience: If one node fails or is compromised, the rest of the network remains operational.
Encryption and Cryptography
Blockchain employs advanced cryptographic techniques to secure data.
Public-key cryptography: Each user has a public and private key. Transactions are signed with a private key, and only the holder can authorize changes.
Hash functions: Transaction data is hashed, making it infeasible to reverse-engineer the original data.
Consensus Mechanisms
Consensus algorithms ensure that all participants agree on the state of the blockchain. Popular mechanisms include:
Proof of Work (PoW): Miners solve cryptographic puzzles to validate transactions, making attacks computationally expensive.
Proof of Stake (PoS): Validators lock up cryptocurrency to participate, reducing the economic incentives for malicious behavior.
Solving Security Challenges with Blockchain
Data Breaches and Hacking
Traditional databases are vulnerable to breaches, where hackers exploit a single point of failure to steal or alter data.
Notable Breach: The 2017 Equifax data breach exposed sensitive information of 147 million people due to a vulnerability in a centralized database. Hackers exploited this single point of failure, gaining access to names, Social Security numbers, and other personal data.
Solution: Blockchain’s decentralized structure ensures there is no central database to target, and the use of cryptography makes unauthorized access nearly impossible.
Insider Threats
Centralized systems rely on trusted administrators who have privileged access. If an insider goes rogue, they can alter records undetected.
Notable Breach: The Edward Snowden NSA leak revealed how insiders with privileged access can exploit centralized systems to leak classified information. Snowden’s actions highlighted the risks of insider threats within centralized, trust-based systems.
Solution: Blockchain’s immutability and audit trail make it impossible to alter past records without detection, discouraging malicious activity.
Data Integrity and Authenticity
Traditional databases can be altered or corrupted without notice.
Notable Breach: The Wells Fargo fake accounts scandal involved the unauthorized creation of millions of fake customer accounts by employees attempting to meet aggressive sales targets. The lack of a verifiable audit trail allowed this fraudulent activity to go undetected for years.
Solution: Blockchain’s cryptographic hashing and decentralized validation ensure that any tampering is immediately visible to all network participants.
Distributed Denial-of-Service (DDos) Attacks
Centralized systems can be overwhelmed with traffic from DDoS attacks.
Notable Breach: In 2016, the Dyn DDoS attack took down major internet platforms like Netflix, Twitter, and Reddit by flooding the Dyn DNS provider with massive traffic from compromised IoT devices. The attack highlighted how central points of failure can be exploited by malicious actors.
Solution: Blockchain’s distributed nature ensures that even if some nodes are targeted, the system as a whole remains operational.
Real-World Use Cases for Blockchain Security
Supply Chain Security
Problem: Counterfeit goods infiltrating supply chains, leading to substantial economic losses and pose serious health and safety risks. Counterfeit and pirated goods accounted for approximately 3.3% of global trade in 2019, equating to around $1.77 trillion.
Blockchain Solution: By tracking the origin and movement of goods on an immutable ledger, companies can verify the authenticity of products at every stage.
Where It’s Working: Maison Margiela and Aura Blockchain Consortium use NFC tagging combined with blockchain technology to verify the authenticity and traceability of luxury fashion items. This approach ensures product transparency, combats counterfeiting, and allows customers to access product information by scanning an embedded NFC chip.
Cybersecurity for IoT Devices
Problem: IoT devices are vulnerable to hacking and exploitation as they often lack robust security protocols. In 2022, there were over 112 million cyberattacks targeting IoT devices worldwide.
Blockchain Solution: Devices can register on a blockchain with a unique identifier, and their actions are recorded immutably. Decentralization reduces the risk of hijacking.
Where It’s Working: Organizations like Media Sourcery have integrated with the Helium Network to develop secure IoT solutions addressing climate change, demonstrating the network's capability to support secure data transmission in critical applications, such as environmental monitoring, climate data collection, and energy usage tracking. These applications enable real-time analysis and decision-making, supporting initiatives to combat climate change and promote sustainability.
Security Identity Management
Problem: Identity theft and data breaches affect millions of people annually. In 2023, the Federal Trade Commission received over 1 million reports of identity theft with more than $10.3 billion total losses.
Blockchain Solution: Decentralized identity (DID) systems store user credentials on the blockchain. Users control their own private keys, reducing reliance on third-party services that can be hacked.
Where It’s Working: Microsoft ION is a decentralized identity system built on the Bitcoin blockchain. It allows users to control their digital identity without relying on third-party identity providers.
Financial Transaction Security
Problem: Online payments and financial transactions are susceptible to fraud. Global e-commerce losses due to online payment fraud were estimated at $41 billion in 2022 and are projected to increase in the coming years.
Blockchain Solution: Cryptocurrency transactions are secured using cryptographic techniques and consensus protocols. Once a transaction is recorded, it cannot be reversed or altered.
Where It’s Working: Ripple provides blockchain-based financial transaction solutions for cross-border payments. By using Ripple's network, financial institutions can process international payments faster and with greater transparency than traditional banking systems.
Key Takeaways
Blockchain’s decentralized nature removes single points of failure, making it more secure than traditional systems.
Immutability ensures that records cannot be altered, offering trust and transparency.
Advanced cryptographic techniques, including hashing and public-key cryptography, secure transactions and user data.
Consensus mechanisms like PoW and PoS prevent unauthorized alterations to the blockchain.
Conclusion
Blockchain’s unique features make it a powerful solution for addressing modern security challenges. From supply chain integrity to IoT security, the technology’s ability to provide decentralization, immutability, and cryptographic protection is transforming industries worldwide. As adoption grows, we’ll see more innovative applications of blockchain to ensure security in digital and physical spaces alike.
All content and materials in this resource are the intellectual property of Quyen Tran and Gentle World Collective. Unauthorized distribution, reproduction, or sharing of any part of this material without written consent is strictly prohibited.
Disclaimer: This litepaper is a sample created for portfolio purposes and is not affiliated with or representative of any specific project, platform, or organization. The content is intended to demonstrate technical writing proficiency and provide an overview of blockchain concepts.
Like this project
Posted Dec 21, 2024
This litepaper shows how blockchain enhances security, solving challenges like data breaches with real-world examples across industries.
Likes
0
Views
10