Built with Rive
Animated Feature Cards for Infisical
Animated Feature Cards for Infisical
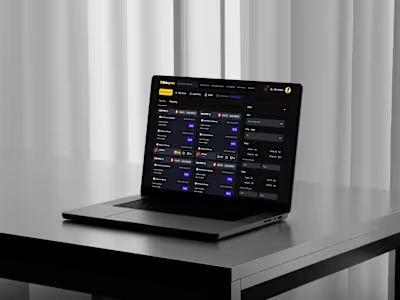
I animated a series of feature cards for Infisical, a platform that helps developers securely manage secrets and infrastructure access.
The goal was to transform abstract security concepts like SSH, KMS, and AI-powered monitoring into visual stories through motion. By using subtle, looping animations, I made these complex features both approachable and memorable.
Tools used: Rive, Figma
My Process
I created a set of animations where each motion design metaphor matched the feature itself. Here are the highlights:
Key Management System (KMS)
Objective
Show how Infisical encrypts, decrypts, and protects data through its Key Management System.
Approach
I created a clockwise orbital animation where documents and keys revolve around a central lock icon. The continuous motion symbolized the lifecycle of encryption and decryption, showing how data is secured in motion.
Outcome
The animation gave form to the otherwise invisible process of key management. Developers could intuitively connect the looping orbit with Infisical’s ability to protect and cycle data securely, making the feature more tangible and approachable.
PKI
Objective:
Visualize how Infisical manages certificate flow and authority hierarchies, making an abstract security process approachable for developers.
Approach:
For the PKI card, I animated file icons looping through a polygonal orbital path with elasticity. This motion represented certificates being issued, verified, and trusted within a hierarchy. The subtle “bounce” made the flow feel alive and emphasized the movement of credentials across authorities.
Outcome:
The animation turned a dense, hard-to-explain concept into a visual metaphor for trust chains. It gave viewers an immediate sense of structure and flow, reinforcing Infisical’s authority in managing PKI without requiring them to parse technical details first.
Dynamic Secrets & Secret Rotation
Objective
Show how Infisical continuously rotates and regenerates secrets to keep infrastructure secure.
Approach
I designed a smooth orbital loop where keys move around a central core, cycling endlessly to imply regeneration. The motion was deliberately subtle, creating the sense of continuous activity without overwhelming the design.
Outcome
The loop conveyed the ephemeral nature of secrets always moving, never static. Developers could quickly understand that secrets are automatically refreshed, building trust in Infisical’s proactive security measures.
Security Advisor
Objective
Communicate how Infisical’s AI-powered security advisor monitors and prevents issues like overprovisioned access and secret leaks.
Approach
I placed the AI core at the center and animated multiple icons (file, magnifier, database, clock) orbiting around it in smooth loops. This design choice represented constant, 360-degree scanning across systems.
Outcome
The result was an always-on visualization of Infisical’s monitoring capabilities. Instead of reading paragraphs of copy, users could instantly grasp that the advisor continuously watches, detects, and prevents risks in the background.
SSH
Objective
Illustrate how Infisical issues ephemeral SSH credentials for short-lived and centralized infrastructure access.
Approach
I designed a left-to-right flow moving from Client → SSH → Server. The linear animation simulated the lifecycle of temporary credentials, highlighting their directionality and short duration.
Outcome
The flow offered a simple but powerful metaphor for secure, time-bound connections. Developers could understand SSH’s purpose at a glance, reinforcing trust in Infisical’s short-lived credential approach.
Preview Link
For Partnership And Collaboration
Whether you’re building a new product or refining an existing product, Let's lcollaborate and ship your idea to life
📧Email: davecsko@gmail.com
Like this project
Posted Aug 20, 2025
Animated feature cards for Infisical to visualize security concepts.