Top Cyber Threats in 2025 and How to Protect Your Business
Like this project
Posted May 31, 2025
Overview of top cyber threats in 2025 and prevention strategies for businesses.
Likes
0
Views
1
Timeline
Apr 30, 2025 - May 1, 2025
Top 5 Cyber Threats Targeting Your Business In The Year 2025
Don’t wait for a breach in your system, network or device, verify your defense system and make sure you are ahead of the threats posed by cyber criminals. Your peace of mind should be your utmost priority. Learn more about the most significant cyber threats in 2025.
Cyber crime is the biggest enemy of business in 2025, with high rate of corruption worldwide, hackers or cyber criminals are developing new means and tactics to disrupt business, defraud, steal informations and important data to either stop the continuity of a business, sell them to competitors in the same niche or demand for ransom. The rate at which hackers increase daily is alarming, they are persistent and use any means to get what they want.
Businesses have to be well informed to protect themselves from unforeseen circumstances that could lead to financial debt or loss of important information. Employees of the companies need to be well informed about the tactics and means in which cyber criminals operate so as to avoid any suspicious link, codes or malicious software that could be sent to the network, system or device.
As technology progresses and advances, cybercrime also increases, cybercrime is not only increasing but the incidents reported by several organisations are getting more sophisticated and dangerous day by day. Cyber criminals deploy new means and new techniques to attack, this is the main reason why a business owner should be well informed and updated of their techniques and schemes.
Wondering what are the top cyber threats in 2025 and how to protect yourself from them, you are in the right place.
Cyber crime is one of the biggest challenges successful business owners, startups and small brands face most of the time. Every business, especially startups, believe only 40% of new businesses and developing businesses will face a cyber threat but 72% of these businesses face or expect an attack from hackers. Cyber criminals target small businesses more because they believe they do not have all the adequate resources to protect. Small businesses are easier for hackers to breach unlike big businesses and they are not well recognised by the media.
Let dive right into the main topic
Top 5 cyber threats faced by small businesses
Let’s address the meaning of cyber crimes and cyber threats to give new business owners who has little to no knowledge about what this might mean or the threats this could cause to their brand.
Cyber crime is any criminal activity that involves a computer, network device or a network. Most cyber crimes are carried out in order to generate profits for hackers or cyber criminals. These crimes are carried out against computers or devices directly to damage or disable them, spread malware, steal secret information and more.
Cyber threats is a destructive act which seeks to steal, disrupt or defraud the target. They steal vital information, disrupt networks and systems which might result to business espionage.
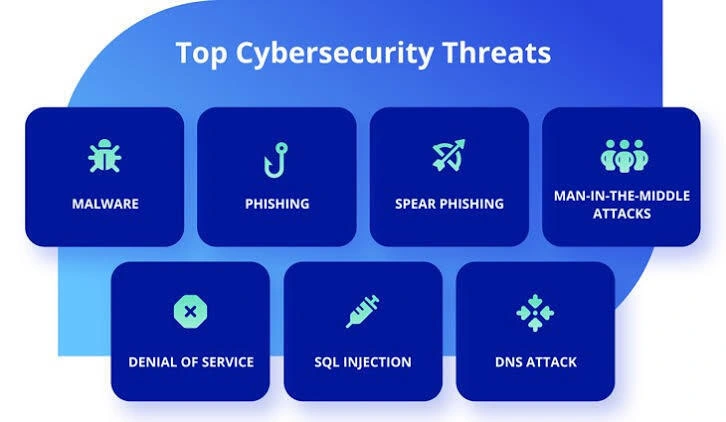
These are the 5 significant cyber threats in 2025 every business owners should be aware of.
Ransomware attack: The revolution of ransom ware in 2025 is one of the highest and most persuasive form of cyber threat. Ransom attack is predicted to be more sophisticated which will target more businesses in 2025. This attack is meant to attack critical infrastructure, cloud environments and infrastructure. Cyber criminals are adopting more tactics to extort businesses by threatening to leak encrypted informations to the public. Ransomware attack can be referred to as the encryption of essential data relevant to the company, cyber criminals encrypt information and demand for ransom to unlock the files and data in their systems.
Insider threats: Insider threat is getting significantly high either by malicious intent of an employee or unintentionally clicking a link that exposes the system, network or device to threat. This cyber crime originates from within the organisation, it could come from a previous employee, customer, contractor, vendor or business partner who is an authorised user that misuse their secured access which could negatively affect the organisation and disrupt system, data and devices. Motives behind this threat could be for fraud, theft, espionage, sabotage, violence, routine violations of organisation policy and more.
Phishing attack: Phishing attack is when a cyber criminal impersonates a real individual to deceive the end user in reavealing delicate information, it could be passwords, card details, data and informations. Cyber criminals often use fake emails, messages or websites link to penetrate and get access to sensitive informations. The goal of the cyber criminals is to defraud, access important informations or install malicious malware on a system, network or device. Cyber criminals also use voice phishing, to attack their target by impersonating an authorised entity voice. Phishing is not only targeted to businesses, they also target high profile individuals like CEO, celebrity or governmental parastatals. Cyber criminals using phishing as a form of attack uses urgent call to action or threats on their targets.
Denial of service: Denial of service is done by an attacker to disrupt an organization's network or system, they send a lot of traffic to the website which makes it crash and temporarily available to use at that time. They use botnets to generate a lot of traffic to the website which leads to slow performance, disruption of service on the website and difficulty accessing the online services. They render the online service useless for the main time and attack during this period.
AI and machine learning in attack: Artificial intelligence can be used for good cause by defenders but cyber criminals are utilising it to their advantage, it has become a destructive weapon in the hands of hackers. The attacks are become more sophisticated, they use AI to draft compelling messages that could convince their target, they create mails with AI that looks professional enough to convince anyone without any suspicion. AI attacks has increased over 300 percent in the past years targeting big and small business owners through phishing. Business owners must stay updated to combat the trick and tactics deployed by this scammers which is a big threat to business owners.
There are a lot of threat cyber criminals use to achieve there aim, for the purpose of this newsletter five has been explained in layman terms to inform business owners of the danger ahead.
Here are some list of various cyber threat that is detrimental to the growth and development of business owners with a pictorial example of what this threat looks like and how they can be identified.
Malware attack
Deep fake technology
Cloud configuration errors
Cryptojacking
Supply chain attack
5g network security
AI governance
Talent shortage
Data governance and privacy and lots more
This is why business owners should educate themselves and put prevention measures in place to protect themselves from cyber crimes.
How To Prevent And Protect Business Owners From Cyber Threats.
These are practical step you can take as a preventive measure to protect your business from cyber criminal and reduce your vulnerability to cyber threats.
Use strong passwords and two factor authentication: A strong password should consist of 12 to 14 alphabet, number and sign, it could be more than that but make sure it is strong enough and cannot be easily cracked. Don’t use important dates like date of birth, make sure you use unique and strategic passwords. After securing your password, use two factor authentication which means after putting in your password you need something else the authorised user has such as fingerprint, face identity, voice recognition before anyone could have access to the system computer or network. This serves as an extra layer of protection to your devices. Two factor authentication also send code to an authorised user device before access is allowed. It could be sent as a mail, message or a voice call to verify if the user is an authorised user and not a scammer. This gives business owners an edge against scammers.
Update softwares regularly: Business owner are strong advice to update every software and system used for the day to day running of the business, cyber criminals often exploit vulnerabilities in outdated software and systems. It is advisable to update apps, system software, operating softwares to ensure you are updated with the latest security patches.
Backup important data: Important data relevant to the company should be backed up, so it will be accessible to the business. Cyber criminals might encrypt important informations and threaten the business to pay ransom to unlock the information. This attack is called Ransomware attack. Backing up information essential to the business will enable you restore and access the information without falling victim of the threat, ransom or fraud. Back up files regularly with an external hard drive or use a trusted cloud service. Also develop and test a recovery plan.
Secure your network: Use antivirus, firewalls, intrusive detective systems and other softwares and hardwares to secure your network from malicious wares like Trojan, virus, botnet and more. Cyber criminals attack with dangerous malware and target it to the system, computer or device, when your system is secured it prevent this malware from affecting your networks. Also monitor network regular traffic for irregular activities. Cyber criminals use malicious wares like botnet to send huge traffic to the network which will lead to slow productivity or it can disrupt the network and make it inaccessible to authorised users.
Security awareness training: Business owners should provide regular security awareness to employees, to help them identify a threat and equip employees to recognise and know how to respond to such threats.
Limit and manage access: Not employees, client, vendor or business partner should have access to some files, some should be only accessible to high officials in the business that makes the biggest decision. An intern for instance should not be able to access the financial report of the organisation and a receptionist does not need access to the entire CRM of the organisation. Make sure sensitive data are only accessible to authorised employees in the organisation. Make sure permission to certain file is adjusted when someone leaves or there is a change in the organisation. By doing this you ensure important information are safe and it will not end up on the street or in the hands of cyber criminals.
Have a clear roadmap when an incident occurs: While preventive measures are put it place, cyber criminal are developing new trend daily, if an incident happens make sure you establish an incident response plan. Know the right things to do when things go wrong - The right person to call, the right measures to put in place, what system to shut down, investigate to know if it’s an insider or external crime. Detect the responsible party for the crime and organize a cyber fire drill.
Cyber security is a step by step process not a one time action. Apply this tips listed above will help protect your organisation from cyber threats and ensure your informations, system, network or devices are safe and resilient in the digital age.
What are some of the danger of not having the right and proper cyber security measures in place for businesses
If the right protection measures are not put in place, it could affect the organisation in the long run. cybersecurity measures should be put in place for businesses to avoid several danger, including:
Data breaches: Without the right protection of informations, network, devices or systems delicate customer and company data can be compromised, which could lead to financial loss, reputational damage, industry espionage and legal consequences
Financial loss: Cyberattacks can result in financial theft, ransom demands, or disruption of business operations, leading to significant financial losses that could end the business.
Reputational damage: A cybersecurity incident can erode customer trust and damage a company's reputation, making it difficult to regain customer confidence. A business without customer base will not stand the test of time.
Final Thought:
In a world where cyber threats is becoming a norm and threats evolve by the hour, cybersecurity cannot be an afterthought. Whether you are a startup or an enterprise, securing your endpoints and training your team is no longer optional, it is your first defense.