Building a Robust Microservices Authentication System
Designed and developed a universal identity and access management system for my company that works both for users as well as services. Some of the technologies that I used are openfga, istio, opa, apigee, golang and more. Here’s how I approached it:
1. Establishing Requirements for Universal IAM
I started by defining the core requirements of the IAM system to ensure it could support authentication and authorization for both end users and service-to-service interactions. This included defining access policies, multi-tenancy support, role-based access control (RBAC), and fine-grained permissions management.
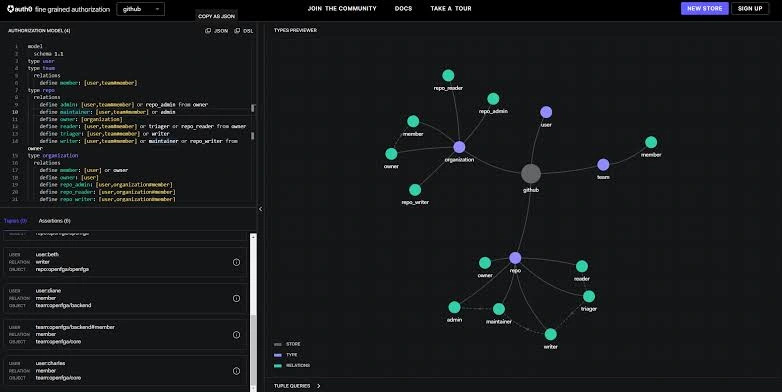
2. Building a Flexible Authorization Layer with OpenFGA and OPA
I used OpenFGA to handle complex relationship-based authorization needs, allowing us to define flexible policies that mapped directly to business roles and organizational hierarchies. For additional policy management and real-time authorization decisions, I integrated Open Policy Agent (OPA). OPA enabled dynamic, policy-based access controls with Rego policy language, ensuring that permissions could be centrally managed and applied at runtime.
3. Implementing Service Mesh Security with Istio
To secure communication between microservices, I integrated Istio as a service mesh, enabling mutual TLS (mTLS) and enforcing authentication and authorization policies across services. Istio’s ability to manage service-to-service encryption and policy enforcement provided an added layer of security within the cluster, supporting both user-based and service-based authentication.
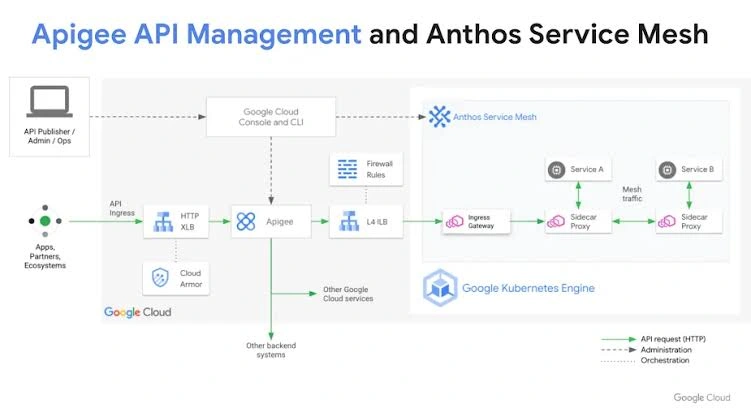
4. Setting Up API Management with Apigee
I used Apigee as our API gateway to manage and secure external access to services. With Apigee, I was able to define rate limiting, caching, and token-based authentication for APIs. This provided a centralized control point for all user and service interactions entering our environment, enhancing both security and observability.
5. Developing IAM Logic in Golang
I developed the core IAM components and services in Golang, taking advantage of its performance and concurrency support. Golang’s simplicity and speed allowed me to build a lightweight, scalable system that could handle high loads with minimal latency, ensuring a smooth experience for end users and services alike.
6. Integrating Authentication and SSO
To simplify user access, I implemented Single Sign-On (SSO) and federated identity support using standard protocols like OAuth2 and OpenID Connect. This enabled seamless login experiences across different applications and allowed for identity federation with external identity providers.
7. Testing and Validating Security and Scalability
Finally, I rigorously tested the IAM system for security, performance, and reliability. I conducted penetration tests, load testing, and policy validation to ensure that it could handle real-world scenarios, from high user traffic to complex, nested permission structures.
This IAM system now enables unified, secure access management across our organization, supporting both end users and services with a flexible, policy-driven approach. By combining technologies like OpenFGA, OPA, Istio, Apigee, and Golang, I was able to build a robust, scalable solution that aligns with our security and access needs.
Like this project
Posted Oct 5, 2024
Developed an authentication system that enhanced security and scalability for microservices, leading to increased client satisfaction and trust.
Likes
0
Views
22