Setup and Troubleshooting of AWS\Azure SitetoSite VPN Configure
Like this project
Posted Jul 5, 2024
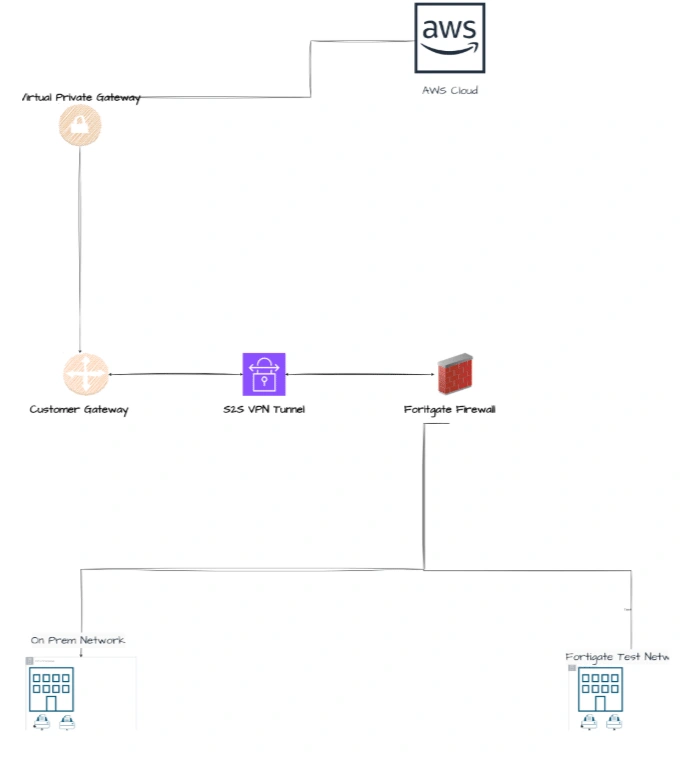
Configured and troubleshooted an AWS Site-to-Site VPN, ensuring secure connectivity between AWS Cloud and a client’s on-premises network, resolving connectivity
Comprehensive Troubleshooting and Resolution Report for AWS VPN Connectivity Issues
Authored by Alwatheq Zboun
Introduction
Following discussions and initial testing phases, I engaged with our AWS system, specifically seeking to address persistent network connectivity issues. My focus was to evaluate and, if necessary, reconfigure the VPN setup to ensure reliable interconnectivity.
Initial Troubleshooting Steps
1. Consultation with --- : I sought authorization from to independently assess and reconfigure the VPN setup within AWS for troubleshooting purposes.
2. Recreation of VPN Components:
• Virtual Private Gateway (VPG): Attempted to recreate the VPG to eliminate potential configuration errors.
• Site-to-Site VPN & Customer Gateways: Despite these efforts, the VPN tunnel failed to initiate, suggesting potential misconfigurations on Signature's network.
Hypothesis Testing
To validate the hypothesis that the issue resided with the external configuration (Signature’s network), I proceeded to establish a Site-to-Site connection to my personal FortiGate setup:
1. Test Virtual Gateway (VGW) Creation: Configured and associated with the Signature VPC for isolated testing.
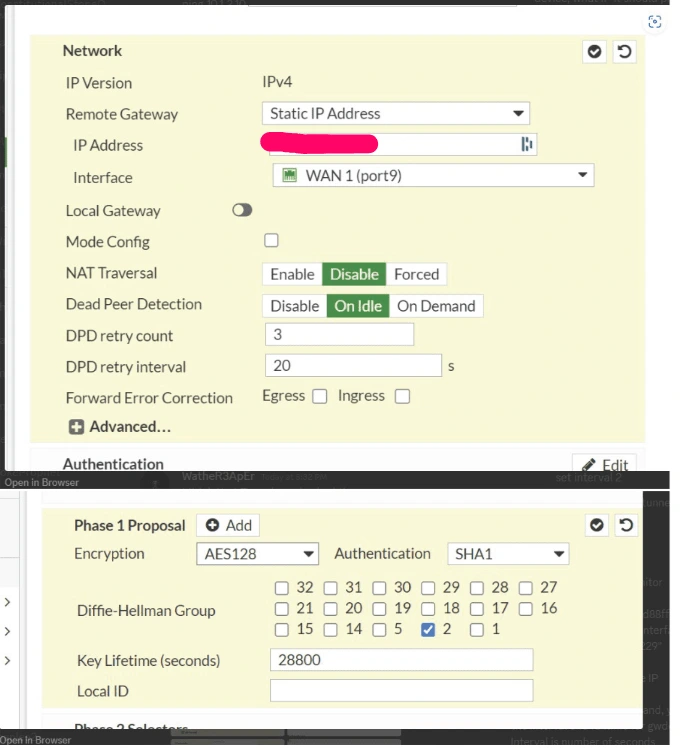
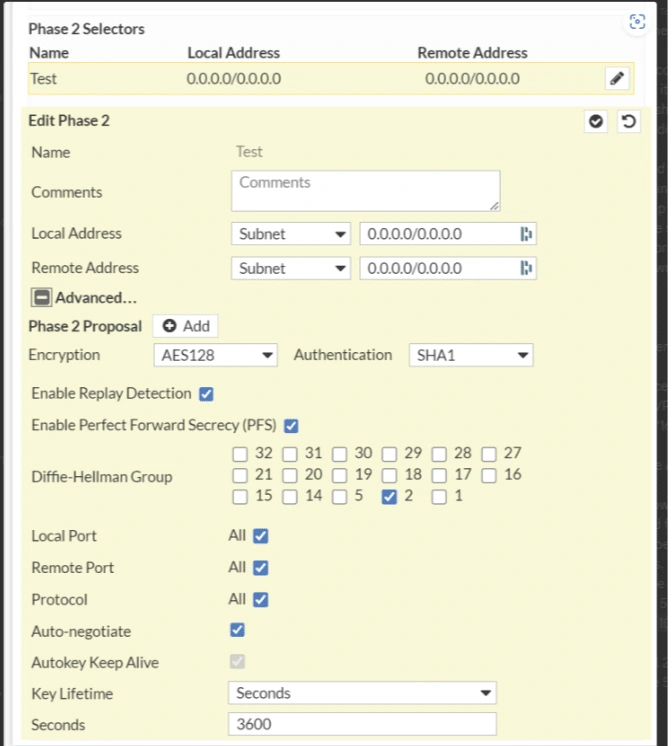
2. Customer Gateway Configuration: Set up using my FortiGate’s external WAN IP address.
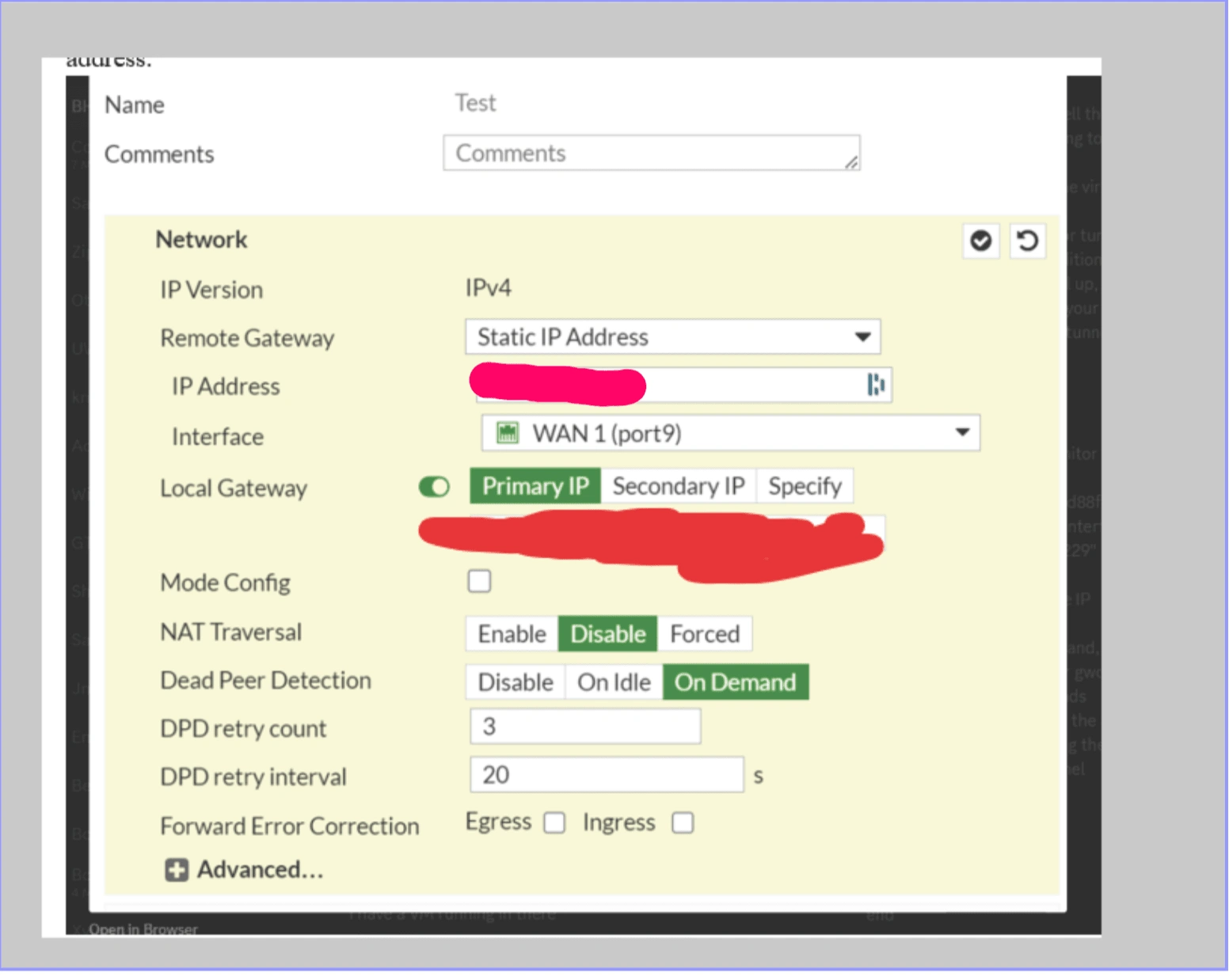
Despite replicating the existing VPN connection settings on my firewall, the tunnel remained inactive, indicating a broader issue than initially suspected.
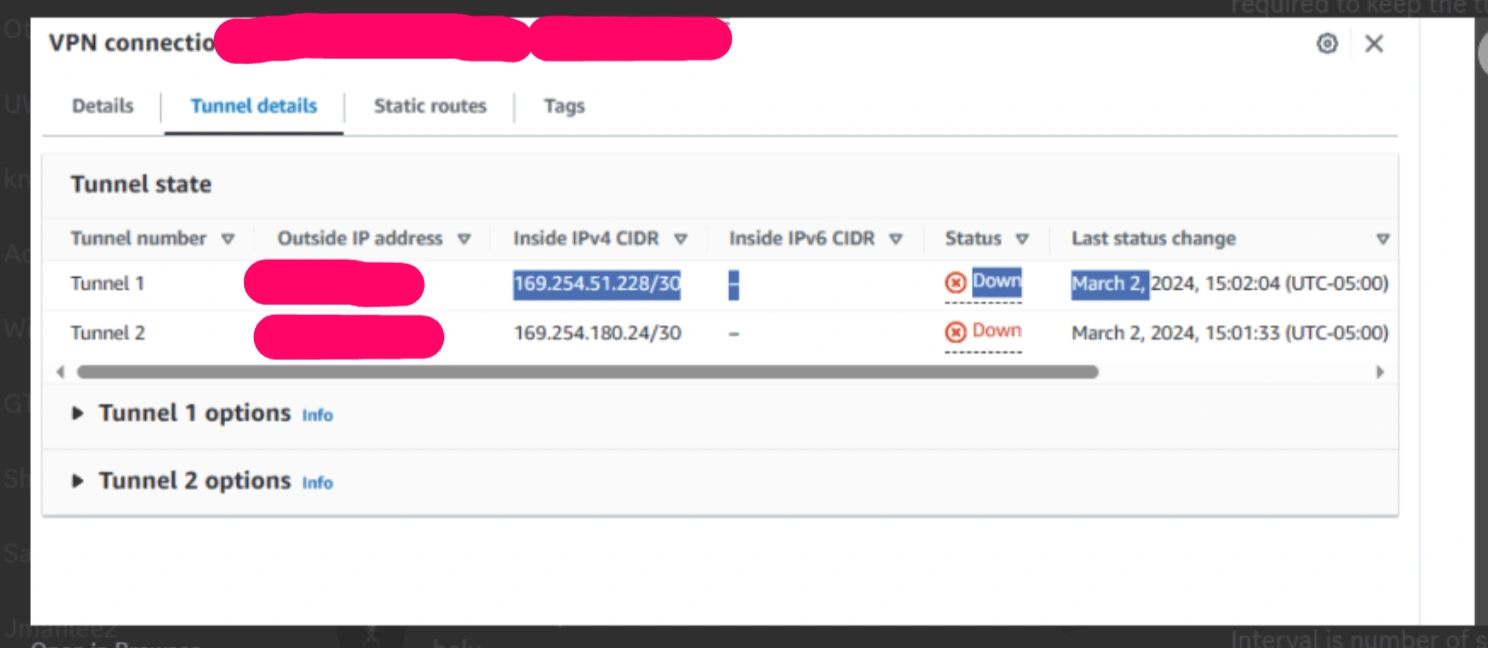
Resolution Efforts
Determined to identify a solution, I undertook the following steps:
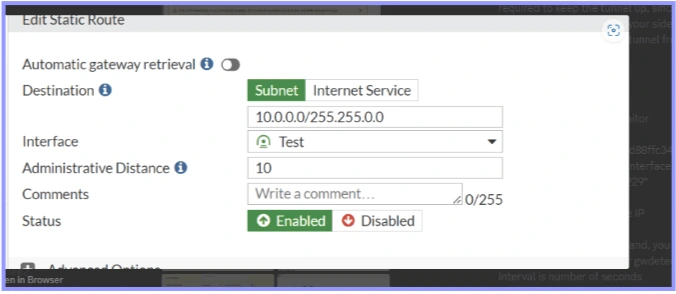
1. VPN Connection Overhaul: Opted to delete the existing VPN connection and establish a new test connection. This action successfully activated the tunnel, showcasing traffic flow and an active tunnel status.
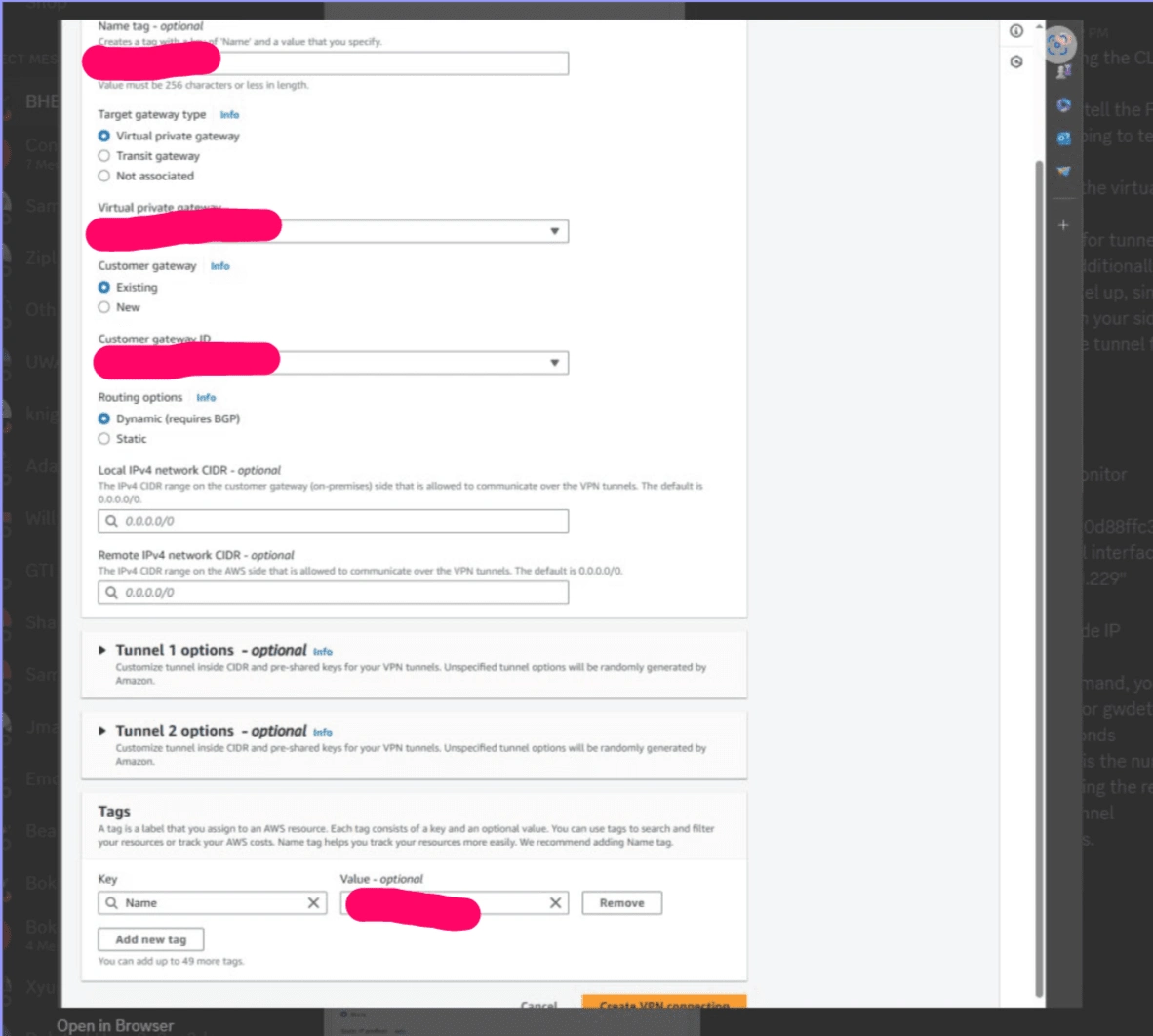
2. Firewall Policy Adjustments: Implemented necessary firewall policies on my FortiGate to facilitate traffic flow and enable ping tests across the network.
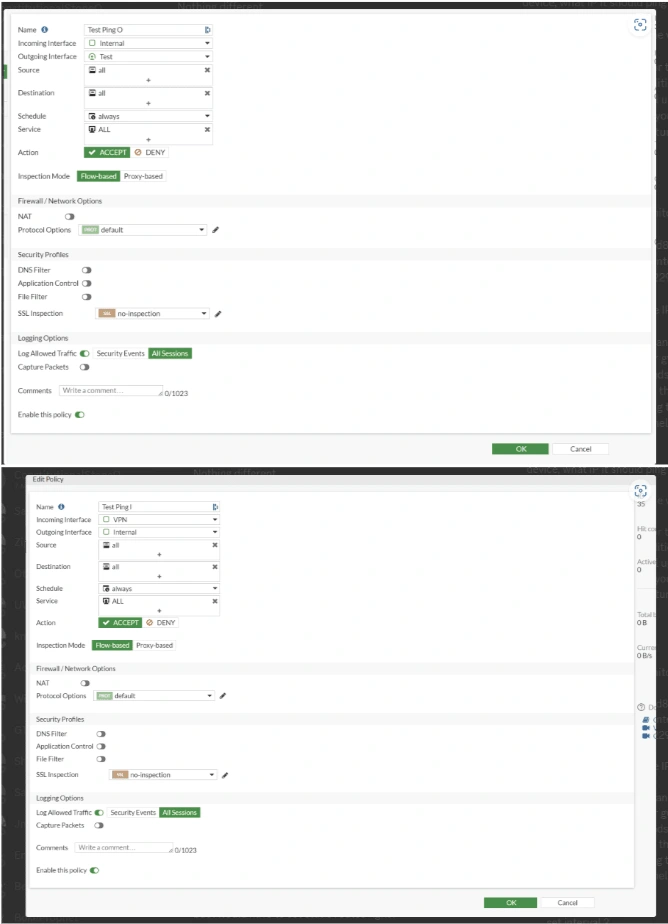
3. Successful Connectivity Tests: Conducted ping and RDP tests, confirming bidirectional network connectivity.
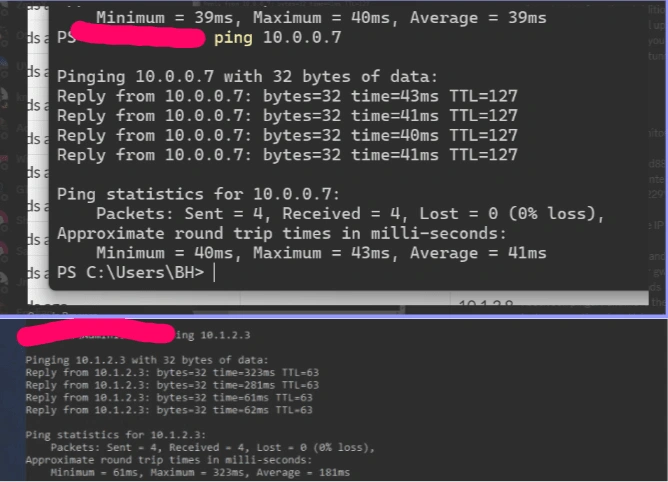
Conclusions & Recommendations
The successful establishment of a Site-to-Site VPN to my personal network environment underscores the likelihood of a compromised tunnel in the initial setup. Recommendations for Signature include:
• IP Configuration Update: Due to the recreation of the VPN tunnel, an IP change is necessary on Signature's end to align with the new tunnel settings.
• Firewall Configuration: While my test utilized FortiGate, the configuration principles should translate across different firewall systems. AWS provides a configuration guide tailored to various firewall models, which should be referenced to match Signature’s setup.
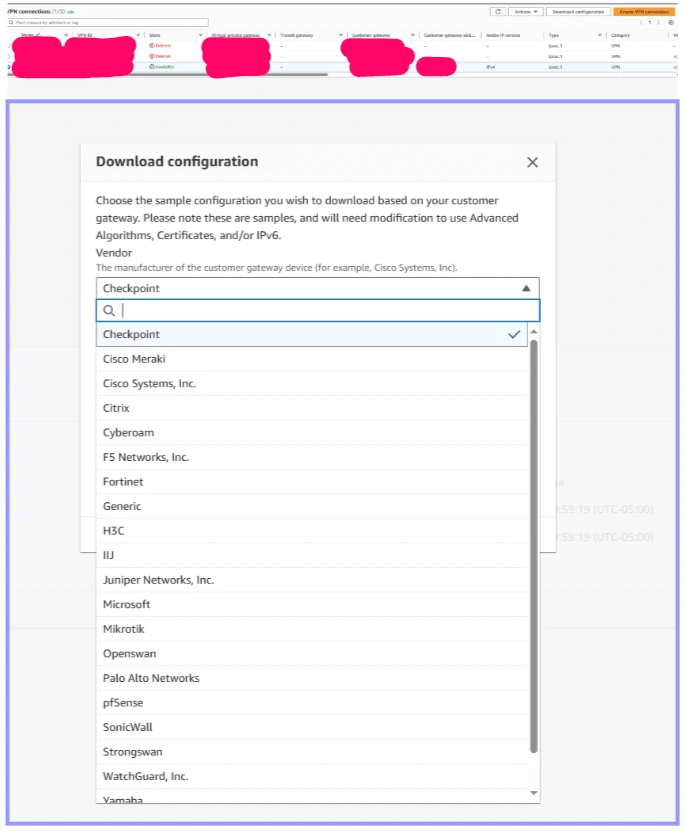
• Document Reference: It is advised that Signature’s technical team utilize the AWS-provided configuration file as a baseline for adjusting their firewall settings to ensure compatibility and connectivity.
Additional Notes
• The specific firewall settings and policies applied in this scenario were tailored to a FortiGate device; adjustments may be necessary to accommodate different firewall technologies.
• Continuous monitoring and testing are recommended post-configuration to ensure stable and secure connectivity.
This document aims to serve as a detailed account of the troubleshooting and resolution process for the VPN connectivity issues encountered. It is intended to guide similar future efforts and assist Signature in configuring their end of the VPN connection.