Affordable Cybersecurity Strategies for SMBs
Like this project
Posted May 31, 2025
Developed affordable cybersecurity strategies for SMBs.
Likes
0
Views
1
Timeline
May 19, 2025 - May 20, 2025
Clients

HER
Cybersecurity For Small And Medium Sized Business: Affordable Strategies That Actually Works.
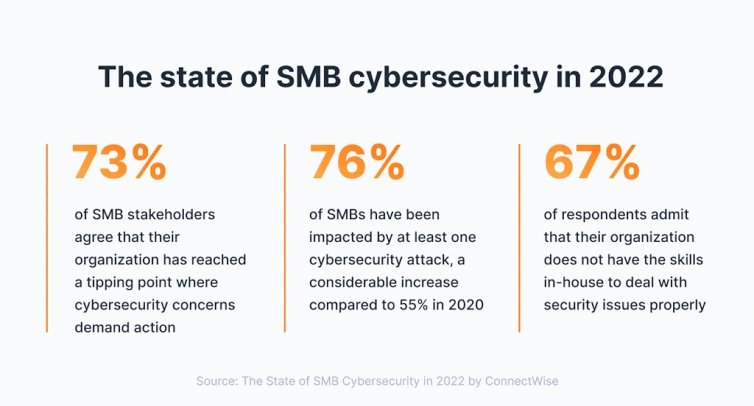
From extortion to robbery, small and medium sized businesses are mostly targeted by cyber criminals. Today small businesses greatest threat is cyber attack. According to statistics several cases has been reported on cyber attack among SMB over seventy seven percent of all cybercrimes are focused on small businesses. Only 42 percentage of small business owners are concerned about this attacks.
How small and medium sized businesses can defend themselves without enterprise budget.
We often talk about cybersecurity and how to protect industries and businesses from cyber threats with valid measures to prevent cyber threat. A very good topic which should be addressed with practical measures but this measures are mostly focused on big businesses owners that can afford high technology and infrastructure leaving small business and medium business owners to figure things out on there own.
Startups with a budget trying to pay employees, build the right infrastructure, get computers, devices, systems and network with little to no support. Some startups get money from the bank and they have to pay loans back combined with all this expenses listed above, it can be overwhelming and frustrating on the business owner. Big companies might hire security analysts, cyber security teams and high profile individuals to protect themselves from cyber threat, they hire them because they can afford it and still run the company in the long run without one departmental issues affecting another.
Start ups sometimes hire remote workers to cut down cost and reduce expenses. In a world that tend to neglect small businesses and focus on the big ones, small business owners have to figure things out on their own. They look out for themselves in the best way they can to keep the company or business going. There are some budget friendly and affordable strategies that still work and will make you one step ahead of cyber threats. Even though cyber criminals nowadays are utilising high and advanced technology to their advantage.
Cyber criminals don’t send quack emails anymore, they draft a persuasive and compelling mails to trick their target and avoid suspicion. They utilise generative AI to mimic voice, impersonate video communication and messages to get the trust of their target and attack when they are more vulnerable. Cyber criminals nowadays don’t just sit around dark rooms with hoodies, they are out there learning new skills, making use of new technologies and looking for new tricks that will scale there game from one percent to hundred. Cyber threat should not be addressed with levity especially among small and medium business owners. They don’t have enough capital to run the business and one big cyber attack could stop the business, shorten the life span or kill a dream that could help nations. It could lead to high financial loss which could results to debts, when the business owners starts paying huge amounts of debt, they sell properties and when they can’t pay it off the CEO either get depressed or get themselves killed. A bad situation that should be avoided, a lot of people have died because of one cyber threat that striped them of every they have ever worked for.
This is literally every thing that could go wrong, now let us focus on the positive aspect. How do we avoid this and stop it from happening this takes us to the next phase
Affordable Preventive Measures Small And Medium Size Business Can Enforce To Protect Themselves From Cyber Threat.
Listed below are some effective and affordable strategies small and medium businesses can enforce to protect themselves. This strategies are budget friendly strategies. No worries it won’t cost you a fortune
Educate your employees: The first step to protect yourself from cyber threats is awareness, you can only find solutions to a problem you know, something you are aware of this gets you prepared, you would be able to spot tricks and schemes and you would know how to strike or avoid them. In a traditional business setting, the training offered to employees are quack video, long and boring one hour video that everyone will forget after few weeks, it not educative enough, does not reveal the danger cyber criminals pose it just a video. As a small business owner if you are still using that technique in 2025 ditch that immediately. In a world where technology is evolving and revolving you don’t want to stick to the past. It’s like using the past to solve the present, building 18th century house in 21st century or carrying a table fork to World War Two. How do you expect to protect yourself when you are still stuck with traditional technology. In a world where generative AI has taken over, they could impersonate the CEO create a video of the CEO asking an employee to forward money to an account for a business partner, it’s your CEO ordering you to do that obviously you would do it. Does not sound realistic? It has happened to a finance company in 2024. The company is in Hong Kong, they lost millions of dollars in a short period of time. This is as a result of lack of awareness or quack video training.
The question now should be how do I step up the game when it comes to employees training about cyber security.
Create short and concise videos, a two to three minute TikTok video that is well educative and professional should be used instead of long boring hours video
Trainings should be divided in batch, they learn and practice what they’ve learnt
Trainings should be more of practical than theoretical
Don’t rely on annual training, stay updated and informed, cyber security training should be done regularly.
Use strong passwords and multi factor authentication: Some small business owners use their date of birth or child’s date of birth to secure website, systems devices or networks that secures sensitive information to the organisation. If you are still doing that in 2025 stop it. Hackers have cracked that strategy a long time ago they are ahead now. A strong password should be at least 12-14 characters which includes numbers, alphabet, signs or dots, these are combined to create a unique password that is hard to crack. Example of a unique password (2{^gh:&£LP/£&Gh<~.)
This password is hard to crack as it consists of different characters which does not include date of birth or names. After creating your killer unique password, the next thing is to use multiple factor authentication, there is two factor authentication but right now we are trying to protect sensitive informations like our life depends on it because it does with affordable strategy. It can be fraustrating putting passwords, biometrics, face recognition, passcodes and lots more to just open a server, device, system or network but this is better than been scammed of your hard earned savings. Ensure you use things that are very personal to you to secure your data, your voice, fingerprint, behavioural pattern, face recognition and lots more. Once the is put in place if there is any weird or suspicious activity on your account, they system automatically block the activity. Game over and you are protected. This strategy is cost effective, some devices or systems have most of this features inbuilt in them.
Update systems and software regularly: Outdated systems and softwares might pose an higher risk and make you vulnerable to a cyber attack. Updating systems and software ensures end to end encryption of data, new security patches which will help protect your data from cyber criminals. It would cost you less or nothing to update your softwares and systems. Do it now and be safe.
Back up your data: Ensure all your data are backed up which eliminates loss of important data. Cyber criminals now use a strategy called Ransomware, they encrypt important information and ask for ransom from the company to unlock this data. If your data is backed up you will be able to have access to your data which will help you escape this new tactics used by cyber criminals to get money from there target. Apart from that, theft or burglary attack could occur, but when data’s are backed up you would be able to access important informations without your lost device. Files can also be transferred to flash drives another means to recover lost data on a system or device.
Invest in a reliable anti virus system: Cyber criminals send malware’s, virus like Trojan, links, files and more to corrupt the system. Investing in reliable anti virus systems like firewalls, antivirus been installed in your system will protect your network, systems, devices and computers from antivirus attack. This antivirus detects virus and notify the user immediately. It also adds as an extra security patch on your system. This antivirus can be installed as software’s or hardware and both software and hardware antivirus can be used on one system. You do not need to spend a fortune to get a good and reliable antivirus system, there are affordable antivirus systems that are affordable that gets the job done just like the expensive ones. Look for the one within your budget that is also reliable and install them on your system.
Limit access to sensitive information: Not every employee working in your organisation should have access to all files and documents. A remote worker or intern should not have access to the financial records of the company, the receptionist should not have access to the CRM records. Limit access to files and documents based on responsibilities assigned to each department or employee. As we focus on outsider threats and unauthorised users, you should also monitor the activities that goes on inside the organisation, employees with malicious intent can attack within.
Phishing and social engineering attacks: Phishing and social engineering attack is one of the most popular threats affecting small and medium size businesses. Cyber criminals utilise emails, messaging app or softwares used for day to day work related communications to trick employees to spill sensitive information. Cyber criminals try to impersonate someone else to get target spill important information like credit card details, passwords or company financial record. In other to avoid this attack use advanced email filtering and anti phishing tools to block suspicious emails before they get their way through the inbox, use generative AI to detect AI generated fraud messages, voice or videos (They use AI technology against you it’s fair that you fight back as well), and confirm urgent calls demanding for urgent transfer of funds before you send the money.
Human defence and suspicions: Even with the advancement and development in technology, human vigilance still plays a massive role. Human vigilance is an everyday defense that still works.
Human defence and suspicions: Even with the advancement and development in technology, human vigilance still plays a massive role. Human vigilance is an everyday defence that still works.
Here are your best bet. Use multiple factors authentication to secure your account, verify every request before taking action, see your boss physical before sending any money. Lastly make sure employees are trained regularly not annually, be updated with the new tactics and schemes criminals use and always put prevention measures to counter their attack. Long boring training video should be scraped, instead of theoretical training let there be practical training.
Conclusion
Have you been scammed before? The worrisome trends you might have encountered in the previous year and the years ahead of been attacked is understandable. You want to protect your business from cyber attacks but you don’t know how to start. The best thing is to be aware of the preventive measures that are available for you and also affordable. What are your essential documents, data, assets and what you are doing currently to protect them from unauthorised user or intrusion? This exercise is very essential to identify potential gaps in the security measures you use presently and how to add extra security patches. When the right measures are put it in place, it would relieve you of security vulnerabilities and will also illuminate persistent productive challenge. I understand it can be hard to get started, and you are not alone in this. Adding preventive measures against cyber security to your small or medium business does not require spending thousands of dollars or hiring your own security analysts, or IT experts you just have to utilise the preventive measures I highlighted in this article and be aware always. Read articles that educate you on cyber threats.







