The Intelligence behind Gmail Security
In Gmail, an email starting with the button click of a sender, passes through a series of security filters before getting into the receiver’s inbox. This article covers the steps involved in between and how Google designed those security functions to work collectively.

The email has become an indispensable part of life for everyone, either personal or professional. Google’s Gmail is the top priority for anyone planning to start an email service. There won’t be anyone who needs an introduction to Gmail, regardless of age group. Email scams or Malware or even eavesdropping to an email is also becoming common. And from a corporate perspective, these issues are considered as a security threat. The Tech Giant works a lot on how they can ensure security for the users’ data and come up with some brilliant ideas which they worked out very well. The safety offered by Google starts even before an email gets delivered to your inbox, through you opening an email, writing a reply or new email, till it gets delivered.
Google works out the Spam filter with:
1. Self-Learning Models: The tech giant makes Use of Machine Learning and deep neural network models (AI) across its 1.5B+ users to keep 99.9+% of the spam out of our inbox.
2. User-Feedback Loop: It’s the method of Integrating user knowledge in their spam models. i.e. the use of “Click unsubscribe” and “Report spam” that helps in spam detection models to improve efficiency.
Google offers security in every step involved in sending/receiving an email. The life of an email is shown in the below image. From the message getting delivered to you through all possible outcomes of every action, you can do with that email.
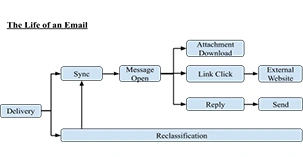
Let us walk through each step and see how the security is ensured in that step.
a. Delivery
Consider an email getting delivered to you. Before that email gets into your inbox, it will be going through a series of checks. They are:
1. Reputation Analysis: This step is to understand the sender of the email. Google will check the header, Sender etc.
2. Content Understanding: Google will go through the message and validate if there is anything risky in the content.
3. Clustering: Google groups similar results and finds patterns.
Once these 3 steps are over, Google will have a clear understanding of where to place the email - in inbox or spam.
b. Sync
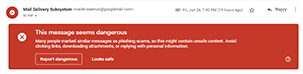
Most of the phishing emails will be filtered out in the earlier step and there will only be a few phishing emails which get past the former step. This is where Google adds security signs/buttons in the email content such as Report Spam etc. which we see in some email in a red banner.
c. Message Open
The email has been opened now. This is the critical situation where the user can help himself or just get hooked up in the phishing. The warning banners are quite big which the users won’t usually miss and download options for malicious content are turned off by default.
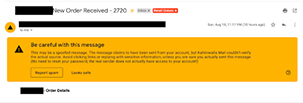
d. Reclassification
Even after the message gets delivered into your inbox, Gmail will be scanning your messages to find if there is any malicious email which is intelligent enough to pass the previous filtrations. If found anything suspicious, there will be a warning in that email too so that the users can be prepared. It is something which Google released recently -Outbreak Warning. If anyone from your organization reports an inbox email as suspicious, Google will propagate that information the very moment across your organization. So that there will be a warning in that email whoever has already received it.
We saw what Google does with an email which has malicious content. All phishing emails won’t be having those within them, but there will be some links which upon clicking may redirect to phishing sites. How Gmail offers security in this situation?
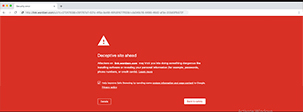
e. Link Click
Google tries to warn you about spam in this step. Suppose, you missed the warning shown earlier and you clicked the link, you will again be getting a warning like the one below. There will be a real-time check for the link you are opening and if it’s found to be suspicious, you are redirected to this page first where you can still get yourself out from phishing.
f. Reply
The email will be asking for some credentials or information which are supposed to be private – to you or the organization. It will be from the email id’s which seems very similar. So, if you put some thought and want to reply to the email as it seems so convincing, in the compose email window also you will be getting a warning.
g. Attachment Download
Downloading a malicious attachment will be a big threat to the organization’s privacy and security. Google has a very impressive malware protection technology.
1. Multi-Layered Scanning: To help prevent malware Google automatically scans attachment for viruses across multiple engines before a user downloading it
2. Block Untrusted Attachments: Encrypted attachments from untrusted senders are blocked and executable contents from all senders across the globe are blocked.
3. 0-Day Protection: Google detects malware still unknown to many AV engines by performing a static and dynamic analysis of the scripts inside files to identify malicious code and by opening the files on virtual machines (Security Sandbox).
In addition to multi-layered AV defences, G Suite provides Document preview by default, reducing the need to download them. Spam, phishing, and malware protection is on by default with Gmail and new protections are frequently added by the tech giant. G Suite integrated with Google Chrome browser gives the users even more security options like safe browsing, Password Alert Policy et cetera.
Last but not least, enabling 2-factor authentications(2FA) or 2-step verification(2SV) for every user should be the very first thing to do. 2FA or 2SV with a passcode is still vulnerable as the hackers will be able to eavesdrop. Usage of security keys or enabling Single Sign-On will reduce this risk at a large scale. Please read this article on Security Tools to enhance your protective measures.
G Suite – Layered Defenses
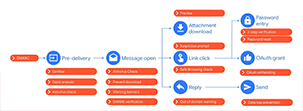
This is the image the same as the first one - The life of an email. But with security features of each step mentioned along with.
Impressive? Want to try G Suite for your organization? Want to add extra security for existing G Suite users with Single Sign-On – Reach out to one of the top Google Premier Partner and G Suite reseller in India: Infiflex Technologies or write an email to jeyaraman.t@infiflex.com. We will help you with setting these up for your organization.
Like this project
Posted Sep 11, 2023
In Gmail, an email starting with the button click of a sender, passes through a series of security filters before getting into the receiver’s inbox. This arti…







