Who Hides a Zip File in an Image?

In this challenge, it says to find the flag in the below image. It’s obvious that it's steganography. In steganography, we can hide data in an image.
The hint showed,
Hmm rockyou. Maybe it would be a phrase or password to decipher the data encoded in this picture.
The first step I did was to use an online steg tool referred
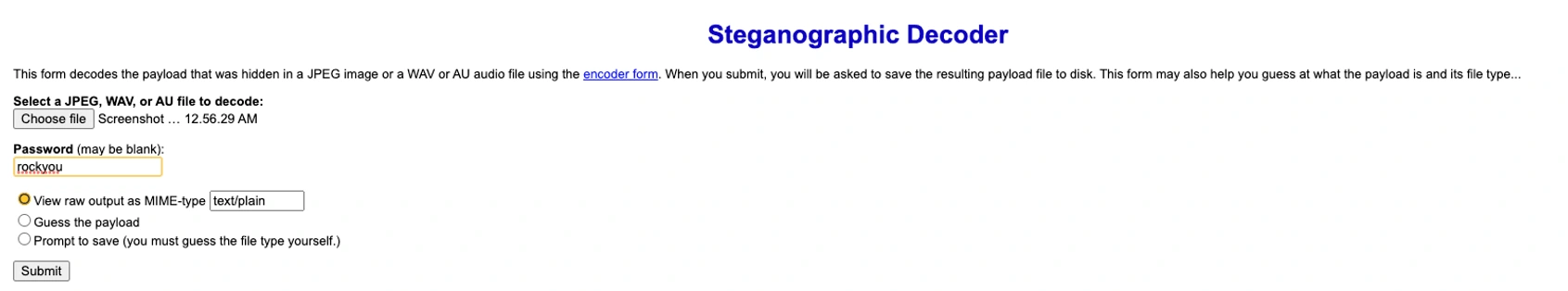
Uploaded the picture, and password as rockyou!
Waited for the results and got this.
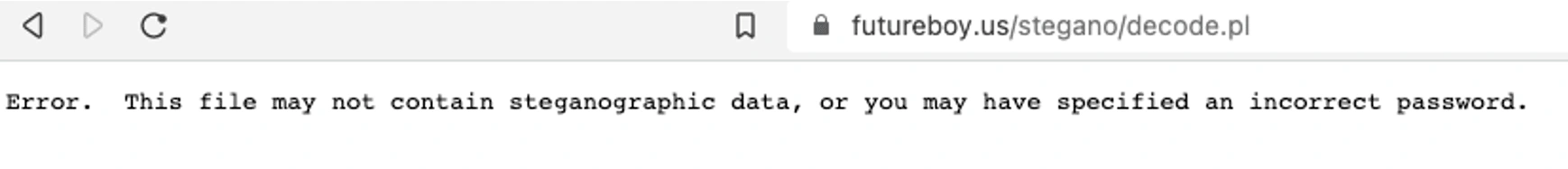
How bad of me . Let’s try another tool called steghide.

I downloaded it on desktop to check,
And ran the following command to run it
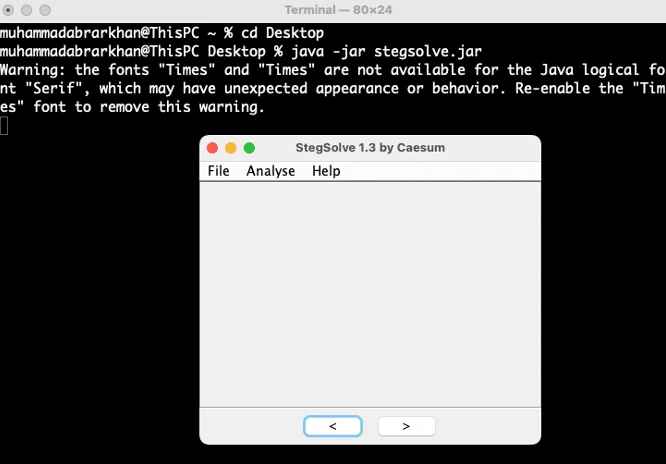
Now this tool will help us pass through this image from different filters and we can kind of see if information is hidden in pixels.

Sadly, didn’t find any hidden message. What a bad tool . Okay, Let’s try another tool online.
Referred: https://fotoforensics.com/

Why do I feel like something is written on meatball’s belly?

Tried my best to decode it but it's really blurry. It looks like something important but after trying so hard, it was a dead end with no luck.
Now I am left with no option but to see the content of this image. Using a hex editor, I opened this file.
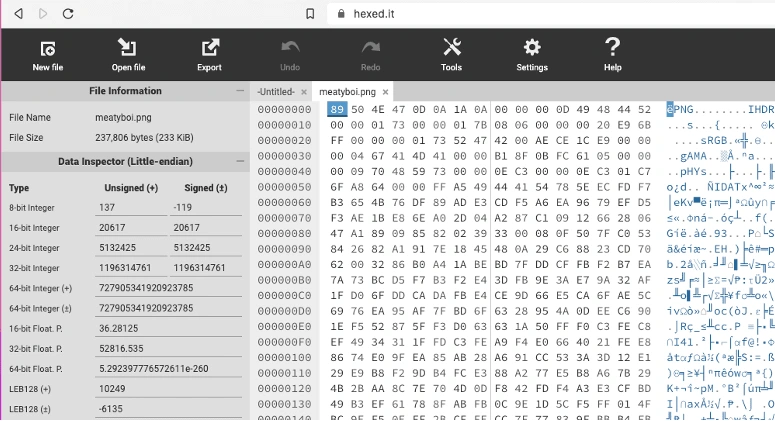
It is indeed a png file, let's see the contents. It seems like the content is kind of encrypted.

From the contents, I saw that there is a flag.txt and there is a ZIP file called getinsideme.zip.
Ooohh, Hiding Zip in a PNG. Quite marvelous.
Let's do the honors.
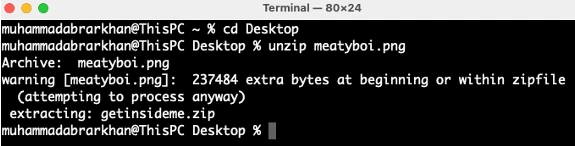
We have a zip file extracted from this png,
Let's unzip this zip file.
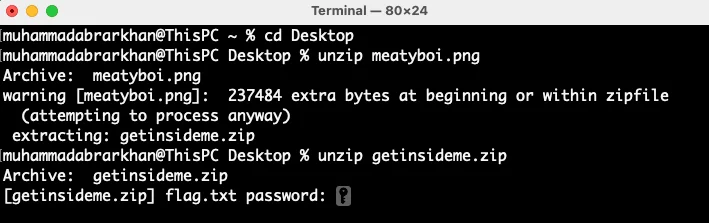
Its asking for a password.
Remember the hint? Rockyou.
Lets try it,
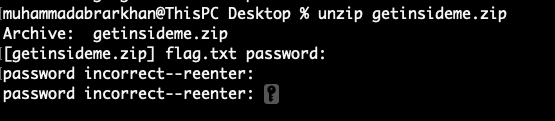
This is cheating!!
Rockyou is not the password.
Then I wasted some time trying random af passwords but got no luck until I searched rockyou online.
Ohhh this is a direction that we need to crack this zip file using this dictionary attack where rockyou.txt is the dictionary.
Downloaded the dictionary
Now we need to perform a dictionary attack.
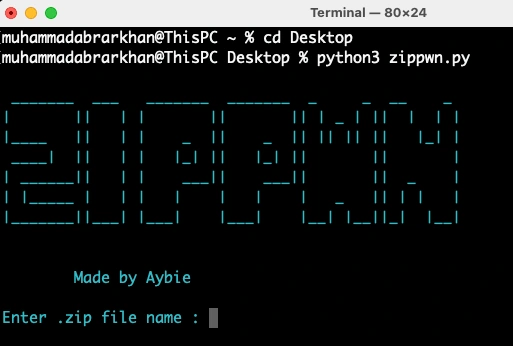
For that, I made my own tool (ZIPPWN) it asks for a dictionary and performs an attack to crack the zip password.
You can clone it. I would be super happy if you like it or give it a star. See here on my Github
Here’s the tool opened
Now I will enter the zip file name and the dictionary name.
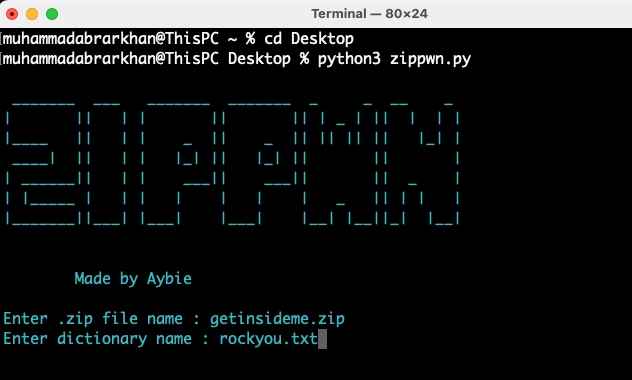
As soon as I entered the names, the script goes through trying each combination in the dictionary and trying the right password.
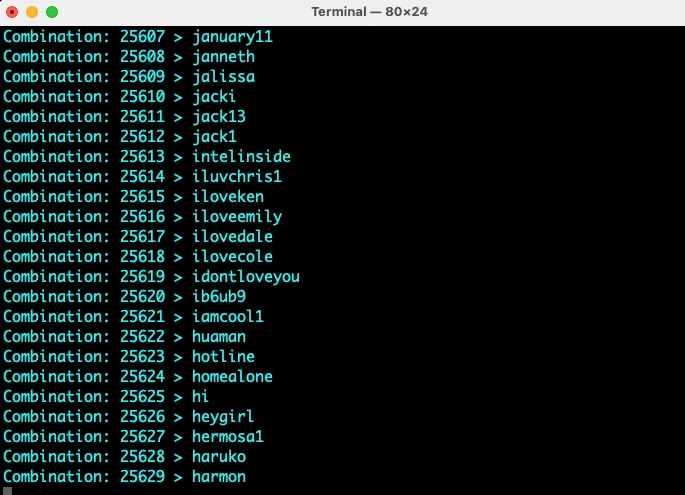
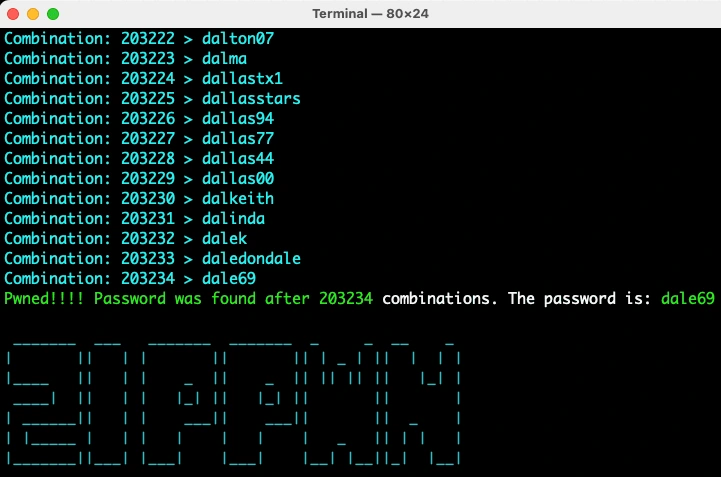
Yesssss!!!! After around 200,000+ combinations tried, the tool was able to find the password of the zip file. The password is dale69.
Let’s unzip the file now.
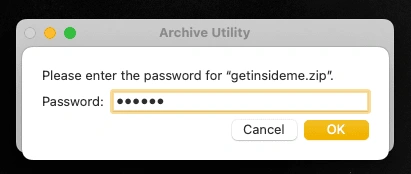
As soon after entering the password, flag.txt is extracted successfully.

Opened it,
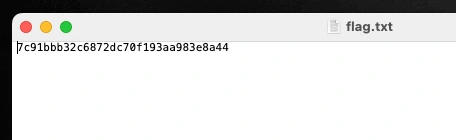
Solved!!!
The flag was: 7c91bbb32c6872dc70f193aa983e8a44
Like this project
Posted Mar 26, 2023
Information hiding in files is a technique used to conceal data within a file, such as an image, audio, or video file, without altering it. Here's the proof!
Likes
0
Views
85
Tags