Developing an Application Security Program From First Principles
I was tasked with developing an application security program on a green field in a short amount of time due to upcoming compliance requirements. This client had very unique challenges, in that their main product is written in C++, with the cloud offering built around it running in AWS and GCP built with Golang and Typescript.
The first task was software composition analysis(SCA). Since unmanaged C++ code limits your options, and the client wanted to operationalize as quickly as possible, we decided to deploy Snyk. For the Golang and Typescript code the standard GitHub integrations were set up. For the C++ code, it must be scanned with the Snyk CLI tool so I developed a module for the build pipeline in bash to find all the dependencies in the cmake file, download them, scan them with Snyk and send them to the dashboard.
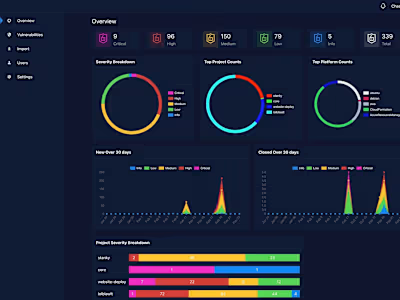
As this client deploys all of their infrastructure using Kubernetes, the next step was Docker container scanning. To save money, the client wished to develop an in-house solution and not pay the extra price for Snyk Container. I set up GitHub Actions across the organization to run the Trivy container scanning tool and send the results to S3. On write, a Lambda would send them to an instance of DefectDojo I set up so that individual contributors could view and manage the vulnerabilities.
Next I tackled the infrastructure as code(IaC) in a similar manner as the container scanning. Using KICS and tfsec, I set up additional GitHub actions across all relevant repositories. As before, the results were sent off to S3 where a Lambda I wrote would convert the issues to the format expected by DefectDojo and insert them into the dashboard.
The client's final requirement was Cloud Security Posture Management(CSPM). I chose to deploy ScoutSuite on a dedicated scanning box using EC2 which performed a full scan on a cadence defined by the client. It was configured to scan both AWS and GCP. Additionally I configured rules for cost-management by reporting certain types of untagged resources. These results were also sent to DefectDojo.
Like this project
Posted Mar 29, 2024
Design and deploy a greenfield application security program which included SCA, container scanning, IaC scanning and CSPM and operationalize it within the org.
Likes
0
Views
2
Clients

Redpanda Data