Additional resources
What Cloud Security Engineers Do
Design Security Frameworks for Cloud Infrastructure
Implement Identity and Access Management
Monitor and Respond to Security Threats
Ensure Compliance with Industry Standards
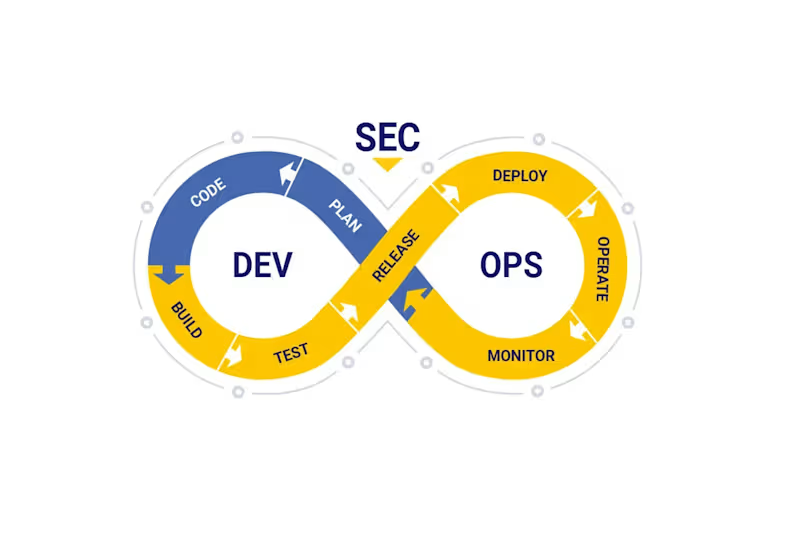
Integrate Security into DevOps Pipelines
Essential Cloud Security Engineer Skills
Platform-Specific Technical Expertise
Scripting and Automation Capabilities
Container and Serverless Security Knowledge
Communication and Stakeholder Management
Risk Assessment and Threat Modeling
Cloud Security Certifications That Matter
AWS Certified Security Specialty
Google Professional Cloud Security Engineer
Microsoft Azure Security Engineer Associate
Certified Cloud Security Professional (CCSP)
Cloud Security Engineer Salaries and Compensation
Entry-Level Salary Ranges
Senior Engineer Compensation
Regional Salary Variations
Benefits and Stock Options
Where to Find Cloud Security Engineers
Specialized Job Boards and Communities
University Partnerships and Bootcamps
Professional Networks and Conferences
Employee Referral Programs
How to Screen Cloud Security Engineer Candidates
Resume Red Flags and Green Flags
Portfolio and Project Evaluation
Certification Verification
Background Check Requirements
Technical Interview Strategies for Cloud Security Engineering Roles
Scenario-Based Security Challenges
Hands-On Cloud Configuration Tasks
Code Review Exercises
Incident Response Simulations
Onboarding New Cloud Security Engineers
90-Day Mentorship Programs
Platform-Specific Training Plans
Security Tool Familiarization
Team Integration Strategies
Retaining Cloud Security Engineering Talent
Continuous Learning Opportunities
Work-Life Balance Initiatives
Career Advancement Paths
Recognition and Reward Systems
Common Hiring Mistakes to Avoid
Overemphasizing Certifications
Ignoring Soft Skills
Unrealistic Experience Requirements
Slow Decision-Making Processes
Building a Strong Cloud Security Team
Defining Team Structure and Roles
Creating Collaborative Workflows
Establishing Security Champions
Measuring Team Performance
Future of Recruiting Cloud Security Engineers
AI-Powered Candidate Screening
Remote Work Considerations
Diversity and Inclusion Initiatives
Apprenticeship Programs