Creating a Highly Available, Two-tier Laravel Web Application U…
Creating a Highly Available, Two-tier Laravel Web Application Using Ansible
1. Setting Up Ansible Controller
An EC2 instance was used as the ansible controller for this task. An IAM role with the following policies was attached to the ansible controller EC2 instance:
AmazonVPCFullAccess
AmazonEC2FullAccess
AmazonRoute53FullAccess
AwsCertificateManagerFullAccess
These policies were attached to ensure that the ansible-controller EC2 instance had full access to the AWS services used in this task. Using an EC2 instance in the target account where the application was to be set up also ensured that the Secret Access Keys and Account Keys weren't specified in the task. The following packages were also installed on the Ansible controller:
Python3
Boto3 - necessary package that enables the ansible controller to interact with AWS
sudo pip install boto3
unzip to unzip the AWS CLI zip file during installation
sudo apt install unzip -y
2. Creating Inventory
A host_vars directory containing two subdirectories (remote-host and localhost) was created. Each subdirectory had a vars.yml file containing specified variables for the tasks ran on each node.
3. Creating Roles
Three roles were used for this task: VPC, EC2-Temp and Final. Each of these roles was created under the roles directory using the ansible-galaxy utility.
VPC Role
The VPC role had tasks that set up the following:
A VPC
Four subnets: two private and two public subnets each
An internet gateway to provide access to the internet for the public subnets
A NAT gateway to provide internet access for the private subnets
A route table each for the private and public subnets
A security group for the private instances which allowed HTTP and HTTPs access only from the load balancer
A security group for the application load balancer that allows HTTP and HTTPs access from the internet
Creation of a template instance that was to be used to create the target AMI for our autoscaling group
Import a private key generated on the ansible controller into AWS and attach it as the key for the template instance for SSH access
EC2-Temp Role
The EC2-Temp role was run using the newly created instance that was created with the VPC role as the target. To run the role, first, the database password for the MySQL database was encrypted using ansible vault.
The vault-encrypted string (db_pass) was inserted into the vars.yml file under the host_vars/remotehost/ path. The EC2-Temp role also did the following:
Clone the target Git repository with the Laravel Application
Install necessary dependencies for the Laravel Application
Set up MySQL user and database for the Laravel Application
Setup an Apache webserver configured with a customized configuration file and to serve the right application path
Final Role
The Final Role was run from the Ansible controller and had tasks that did the following:
Created a new AMI using the configured remote instance on which the Laravel Application was running
Set up autoscaling and target groups
Created an application load balancer and attached it to the target instances created by the autoscaling group
Setup SSL certificate with ACM manager using Ansible shell module
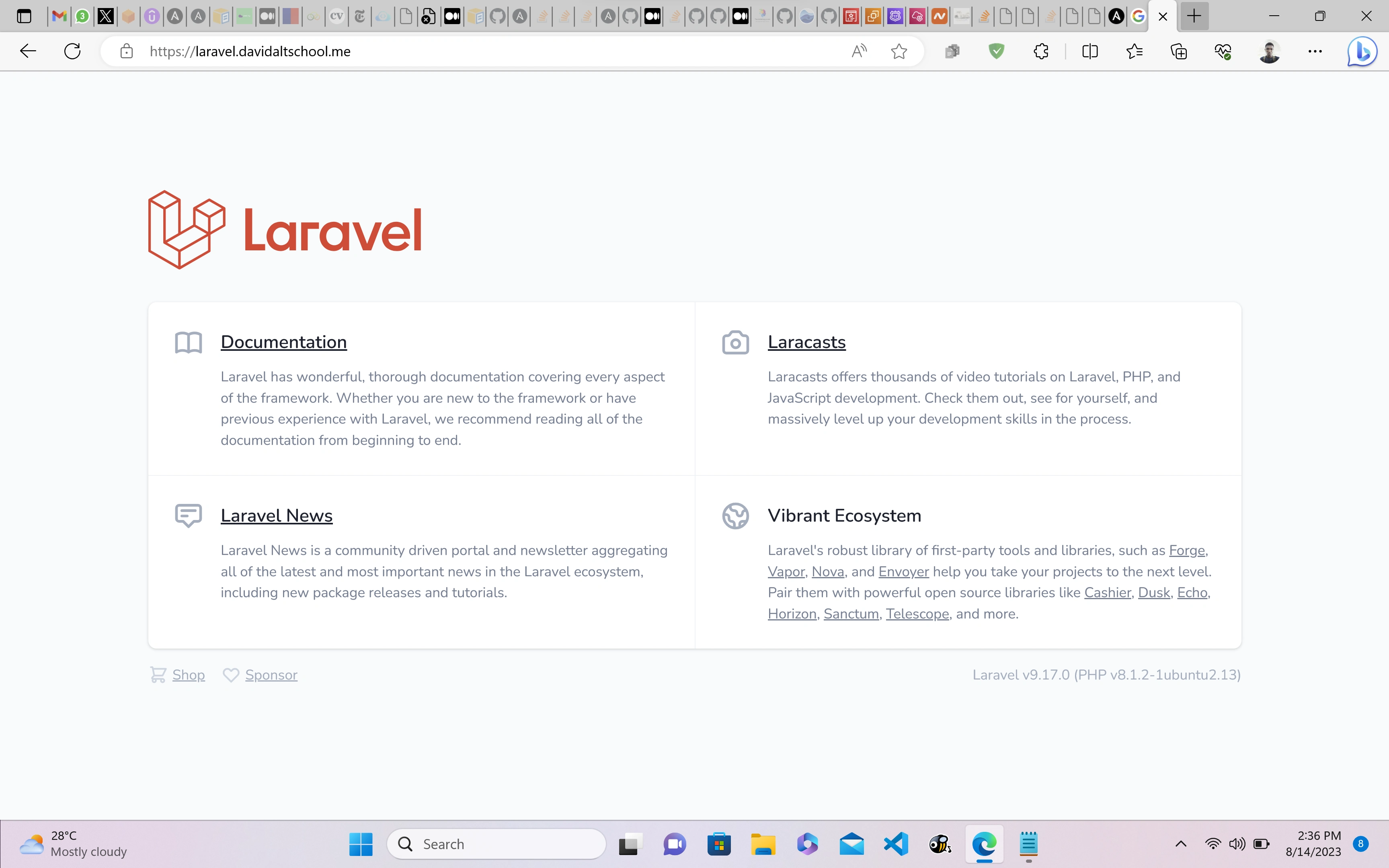
Setup a Route 53 Hosted Zone (davidaltschool.me) with an Alias record pointing the desired subdomain (laravel.davidaltschool.me) to the application loadbalancer.
The project was run using the ansible-playbook command.
The final Laravel Application ran on the desired number of instances (2) and was served by an application load balancer with an SSL certificate attached to redirect HTTP traffic to HTTPs.
Like this project
Posted Jan 10, 2024
Contribute to rigamortus/devops-projects development by creating an account on GitHub.
Likes
0
Views
21