Intrusion detection System
System Design Document
1. Comprehensive Architectural Overview
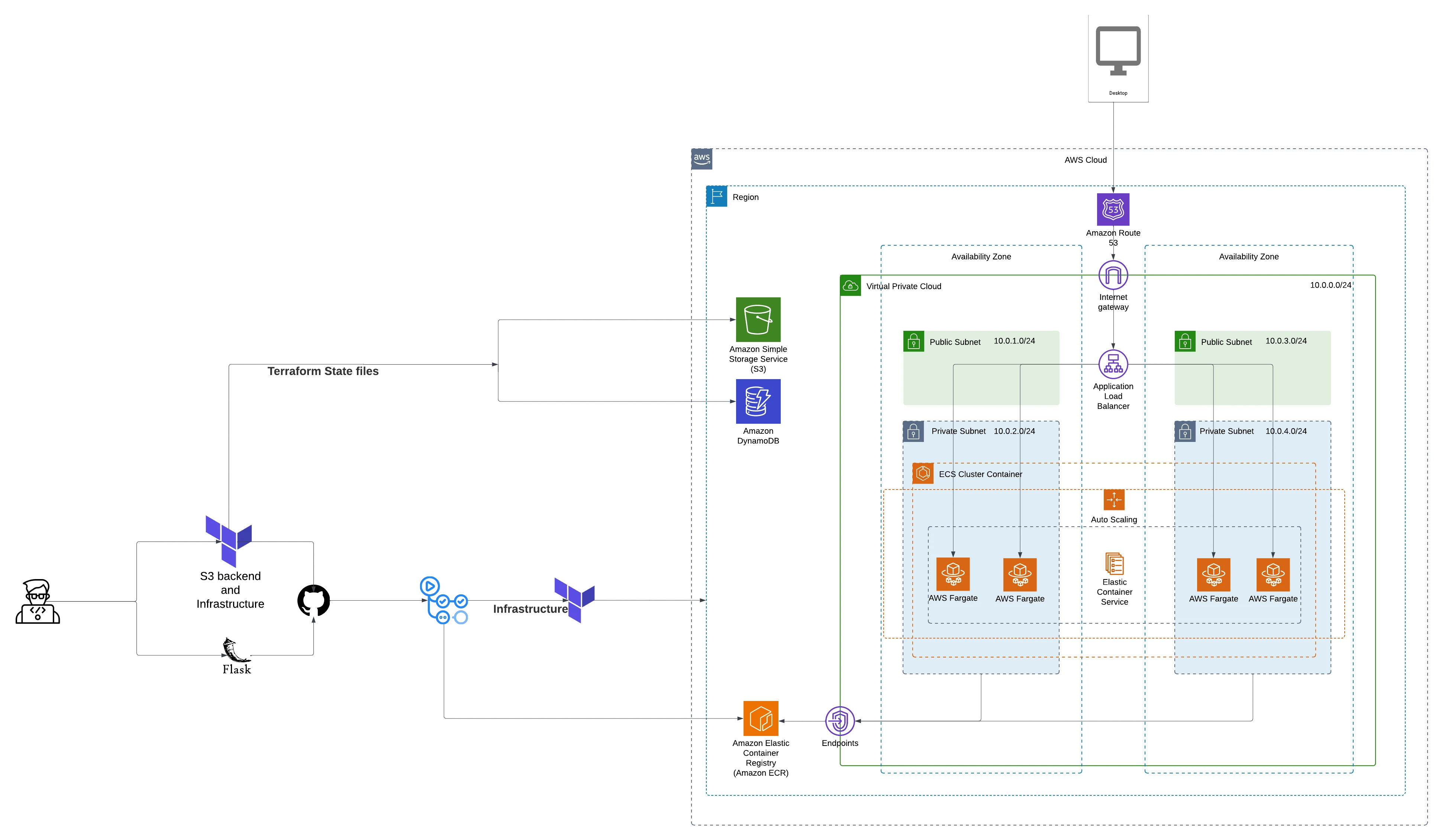
The system is designed using a Microservices Architecture to ensure scalability, maintainability, and better separation of concerns. The architecture separates the Frontend and Backend services, each deployed on AWS Fargate within an ECS Cluster, with appropriate load balancing and networking layers.
2. Detailed Component Interactions
Route 53 + ACM: Manages the custom domain name and SSL certificates.
Application Load Balancer (ALB): Public-facing ALB for the frontend service, and an internal ALB for the backend API service.
Frontend (Next.js): Deployed as an ECS Fargate Service behind the public ALB, responsible for serving the UI and interacting with users.
Backend (Flask API): Deployed as an ECS Fargate Service behind an internal ALB, responsible for handling API requests, ML inference, and file processing.
VPC: Spread across 2 Availability Zones (AZs) with public and private subnets.
S3: Stores uploaded files and processed results.
DynamoDB: Tracks job status and metadata.
Security Layers: AWS WAF, AWS Shield, IAM policies, and private networking.
3. Technology Stack Justification
Next.js + Flask: Clean separation of frontend and backend logic.
AWS Fargate + ECS: Serverless container orchestration without managing servers.
ALB: Provides load balancing, SSL termination, and routing.
S3 + DynamoDB: Durable, scalable storage and metadata tracking.
CloudWatch Logs: For monitoring and debugging.
4. Scalability & Performance Considerations
ECS Services can auto-scale based on CPU/Memory metrics.
Multi-AZ deployment ensures High Availability.
S3 and DynamoDB are highly scalable and managed.
Load Balancers distribute traffic efficiently across AZs.
5. Key Design Decisions & Rationales
Microservice Separation: To decouple frontend and backend, allowing independent scaling and deployment.
Internal ALB for Backend: Keeps the backend API private and secure.
Serverless Container Approach: Simplifies infrastructure management.
S3 + DynamoDB: Efficient and cost-effective storage and tracking mechanism.
Always-on Backend ECS Service: Avoids delays in processing requests compared to on-demand batch tasks.
6. Technical Constraints & Solutions
Security Requirements: Enforced using WAF, Shield, and private subnets.
Domain Management: Implemented with Route 53 and ACM for secure access.
Efficient Communication: Frontend interacts with backend through an internal ALB ensuring private and low-latency communication.
Job Tracking: Implemented using DynamoDB for real-time status updates.
Architecture Documents
High-Level Architecture Diagram
Route 53 (DNS + Domain) → Public ALB → ECS Fargate Frontend Service (Next.js) → Internal ALB → ECS Fargate Backend Service (Flask API) → S3 + DynamoDB
Network Topology Design
Public Subnets: Hosts ALB.
Private Subnets: Hosts ECS Fargate tasks for both Frontend and Backend.
NAT Gateway: Enables ECS services to access the internet securely.
VPC: Spread across two AZs for high availability.
Component Interaction Specification
User requests → Route 53 → Public ALB → Frontend (Next.js)
Frontend → Internal ALB → Backend (Flask API)
Backend API interacts with S3 (file storage) and DynamoDB (job status)
Data Flow Diagrams
File Upload Flow:
User uploads file → Frontend → Backend API → S3
Processing & Result Flow:
Backend processes file → Saves results to S3 & status to DynamoDB → Frontend polls API or uses WebSocket → Displays result
Like this project
Posted Mar 30, 2025
This project involved training a machine learning model and creating an application around it where users can scan their network data for malicious traffic.