GitHub - CSharpTeoMan911/ThetaFTP

About❓
ThetaDrive is a cross-platform open-source Google Drive alternative, that is an easily configurable full-stack FTP server application that works on both Windows and Linux. It comes ready to deploy with advanced features like two-step authentication via SMTP, SSL/TLS connection encryption, SSL certificate generation, and customizable security and database attributes. The website is hosted live at: https://theta-drive.org
📥Download & Setup
➡️ To download the application, go to the Release section and download the application binary executables. Alternatively, you can download the binaries and source code from SourceForge.
➡️ For instructions about how to use and configure the application, please visit the Wiki section of this repository.
📚 Tech stack
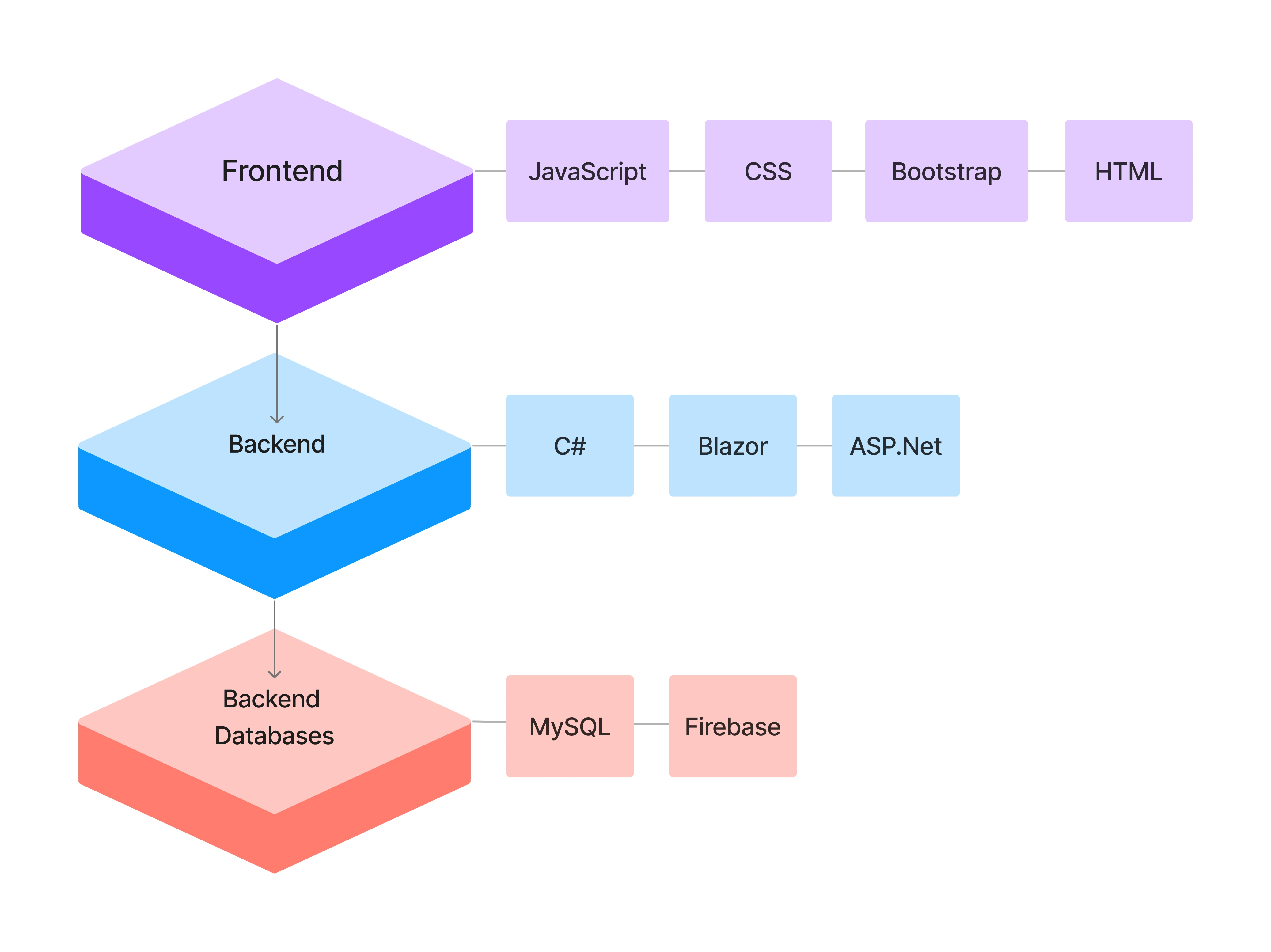
🗂️ Ftp features
🔼 Upload: Upload files securely.
🔽 Download: Download files from your server.
📦 Move: Move files within your directories.
✏️ Rename: Rename files or directories.
🗂️ Create: Create directories
🗑️ Delete: Delete files or directories securely.
🛡️ Security features
🔐 DDos protection
The application uses an IP based rate limiter to protect against DDos attacks, as well as ensuring a predictible CPU and RAM usage.
🔐 Connection encryption
The application uses SSL/TLS encryption to secure the client-server connection, preventing unauthorized access. You can configure it with either self-signed certificates or trusted publisher certificates.
🔐 Local storage encryption
The application will encrypt data to be stored within the local storage on the server side to prevent mallicious actors from gaining access to session tokens.
🔐 File encryption
The application uses state of the art AES 256 (Advanced Encryption Standard) encryption algorithm to encrypt files.
🔐 Path traversal attack prevention
Each user has a dedicated directory.
The server validates any file path to ensure it is within the user’s directory.
Invalid paths are rejected to prevent unauthorized file access.
🔐 SQL injection prevention
The application uses parameterized queries to prevent SQL injection attacks.
Special characters are escaped to ensure safe SQL command execution.
🧂➕#️⃣ Salting and hashing
All sensitive information stored in the database is hashed using the SHA-512 algorithm and salted, for added security. This ensures that even if the database is compromised, the data remains unreadable
🪪 Log in session validation
For every operation requested by the user, such as uploading or downloading a file, the server will request for the client its log in session key. If the log in session key is expired or the log in session key is invalid, the server will log out the user. If the log in session key is valid, the server will only process request and information for the account associated with the log in session key, thus preventing mallicious attacks.
🪪 Two-step registration
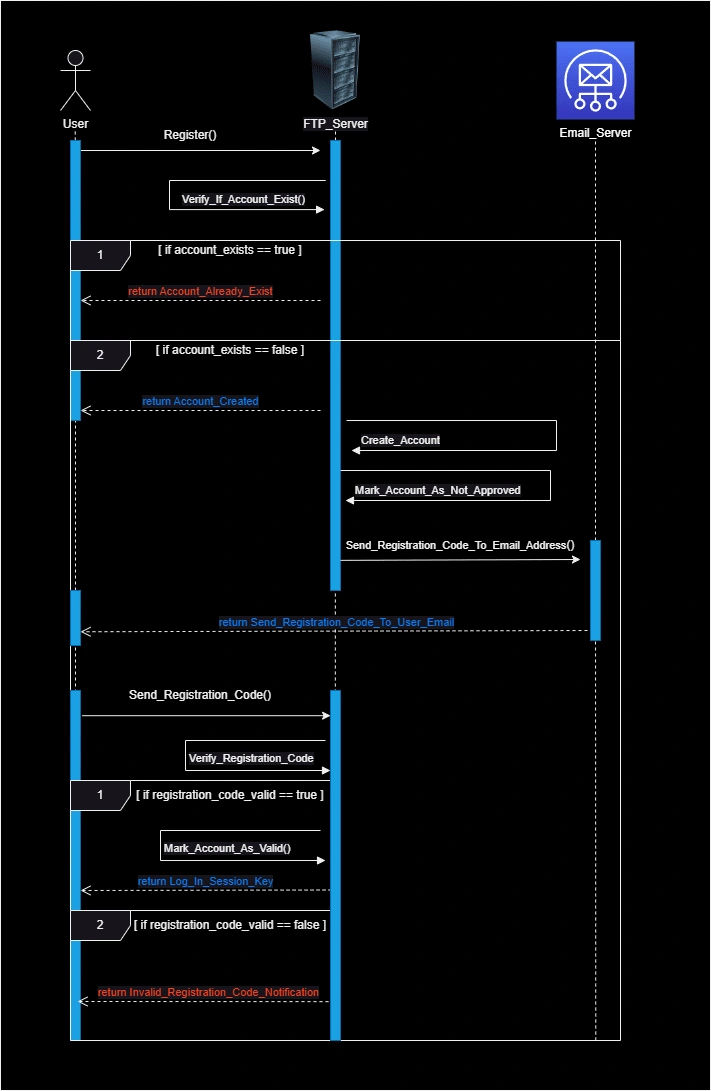
Account Creation:
When a user tries to create a new account, the server first checks if the account already exists in the system.
Registration Code Generation:
If the account doesn't exist, the server generates a registration code and stores it in the database.
The registration code is linked to the account, and until it is verified, the account remains invalid.
Email Notification:
The server sends the registration code to the user's email address and prompts them to enter the code on the registration page.
Code Validation:
The user enters the registration code, and the server verifies its validity.
If the code is valid, the server deletes the registration code from the database and proceeds to the next step.
Account Activation:
Once the registration code is validated, the account becomes valid, and the server sends a login session key to the user, effectively logging them into the system.
Expiration & Failure:
The registration code has a 1-hour expiration time.
If the user fails to enter the correct code within this period, both the account and registration code are deleted from the database.
🪪 Two-step authentication
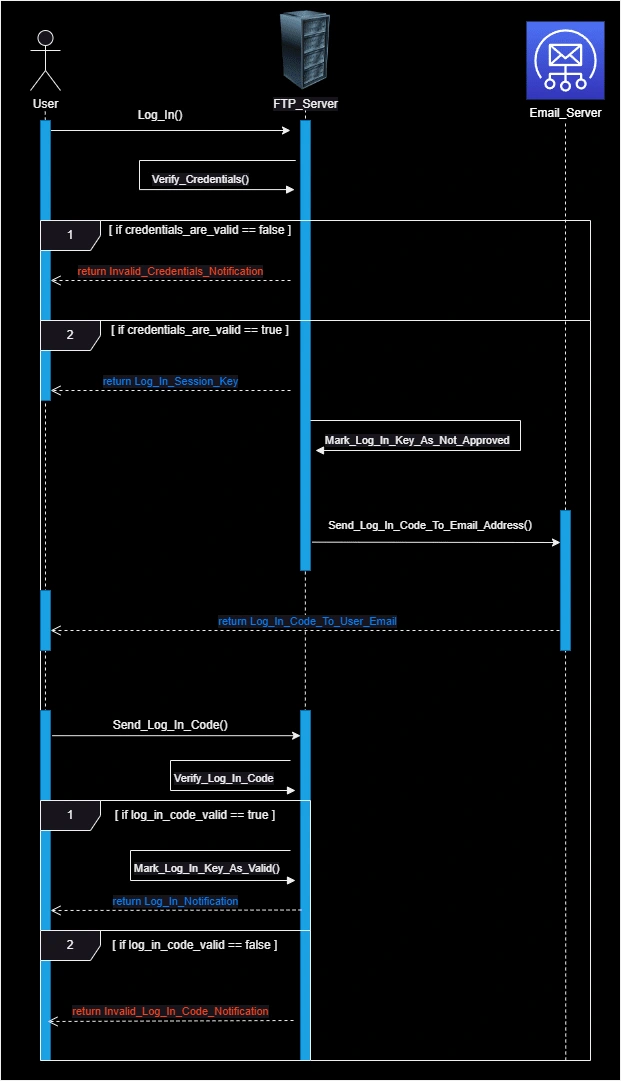
Login Attempt:
When the user attempts to log in, the server first verifies the user credentials (username and password).
Session Key & Login Code Generation:
If the credentials are valid, the server generates a login session key and a login code.
Both the session key and the login code are stored in the database.
Invalid Session Key (Until Verification):
The login code is tied to the session key. Until the login code is verified, the session key remains invalid.
Email Notification:
The server sends the login code to the user's email address and prompts the user to enter the code.
Code Validation:
If the user enters the correct login code, the server validates it and removes the code from the database.
Once the login code is validated, the session key becomes active, and the user is granted access.
Expiration & Failure:
The login code expires after 2 minutes.
If the user doesn't enter the correct code within this time frame, both the session key and login code are deleted from the database, and the user must start the login process again.
1️⃣0️⃣1️⃣1️⃣0️⃣ Binary manipulation mechanism
1️⃣0️⃣1️⃣ File upload binary manipulation mechanisms
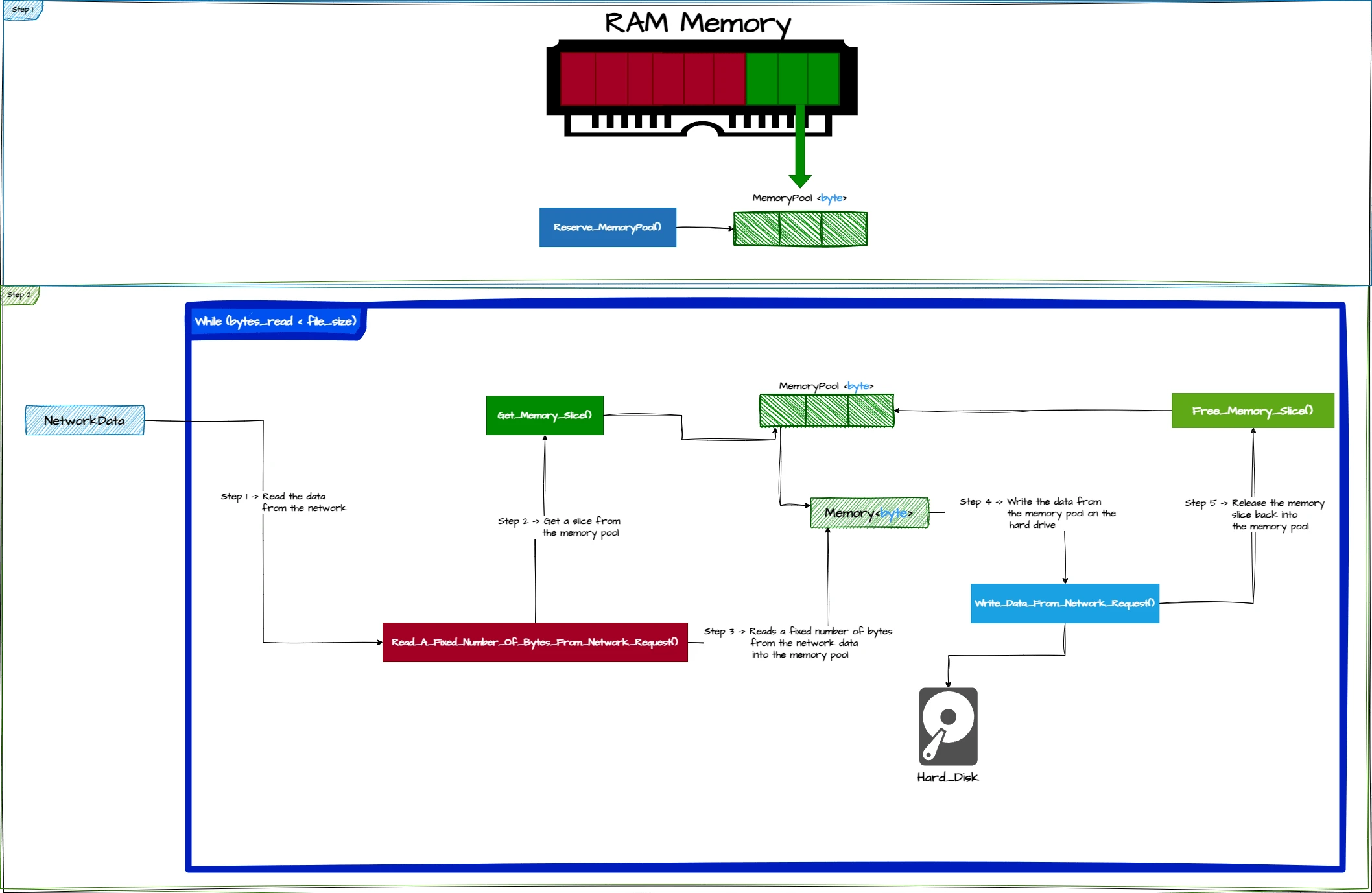
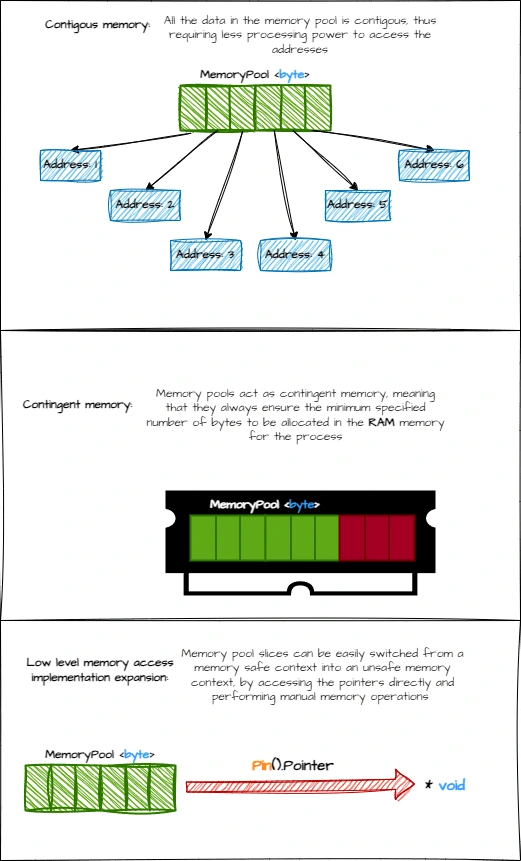
1️⃣0️⃣1️⃣ MemoryPool characteristics
Like this project
Posted Jan 18, 2025
ThetaDrive is a secure C#-based cloud storage system with 2FA, SHA-256 encryption, and FTP features like upload, download, rename, and directory management.
Likes
0
Views
4
Timeline
Jul 31, 2024 - Mar 31, 2025