Chimdiebube Egereonu
Web Security Analyst & OSINT Specialist
New to Contra
Chimdiebube is ready for their next project!
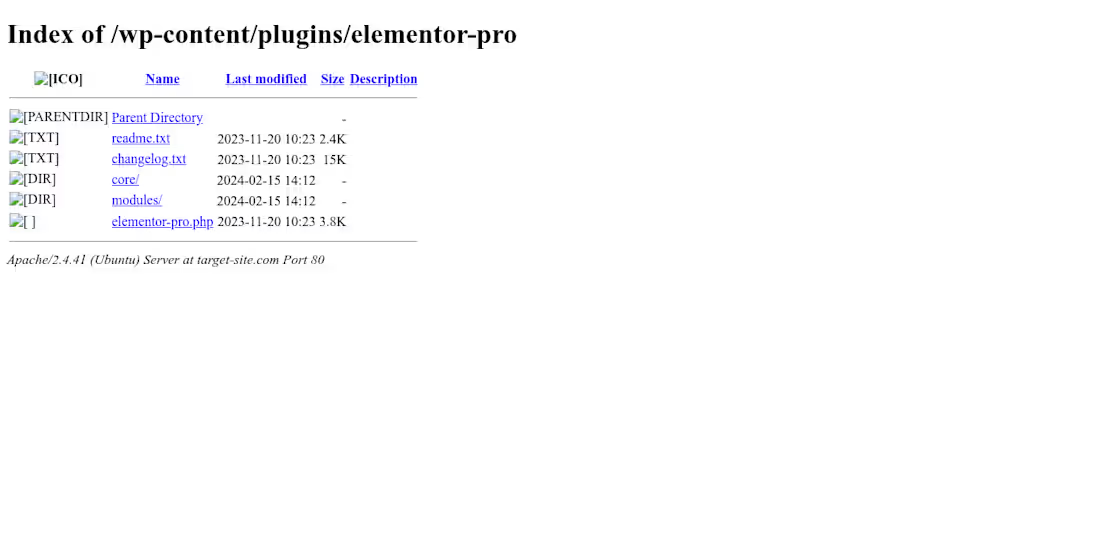
WordPress Security Hardening & Malware Prevention
Security audit for a business portfolio website running legacy infrastructure.
Findings:
Outdated Software: Identified CMS version 4 years out of date, exposing the site to known CVEs.
Plugin Vulnerabilities: Detected vulnerable versions of Elementor susceptible to Stored XSS.
Directory Traversal: Public access enabled on plugin directories.
Solution: Provided a roadmap for updating the core CMS, patching plugins, and implementing .htaccess rules to block directory browsing.
1
10
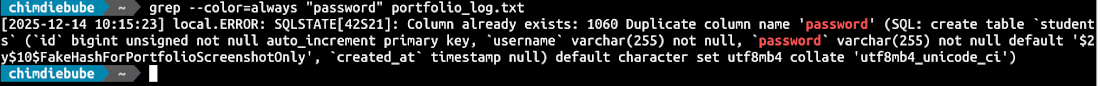
Critical Information Disclosure (Server Logs)
Identified a Critical (P1) data leak in an educational management portal.
The Finding: Exposed Laravel Debug Logs (laravel.log).
Technical Details: The server was misconfigured to allow public "Directory Listing" on the storage folder. This exposed a 5MB log file containing:
Full Database Schema.
Backend Stack Traces.
Hardcoded default user credentials.
Remediation: Advised the internal team to disable directory indexing and restrict access to the /storage/ directory immediately.
1
16
WAF Bypass & XSS Discovery for E-Commerce Platform
Conducted a black-box security assessment for a high-traffic e-commerce marketplace (10M+ users).
The Finding: Reflected Cross-Site Scripting (XSS) in the search functionality.
Technical Details: The application employed a Web Application Firewall (WAF) that stripped standard XSS vectors (parentheses). I successfully bypassed this filter using ES6 Template Literals (backticks) to execute JavaScript.
Impact: Reported a P2 Vulnerability that could allow account takeover via session cookie theft.
Status: Reported via Vulnerability Disclosure Program (VDP).
1
17
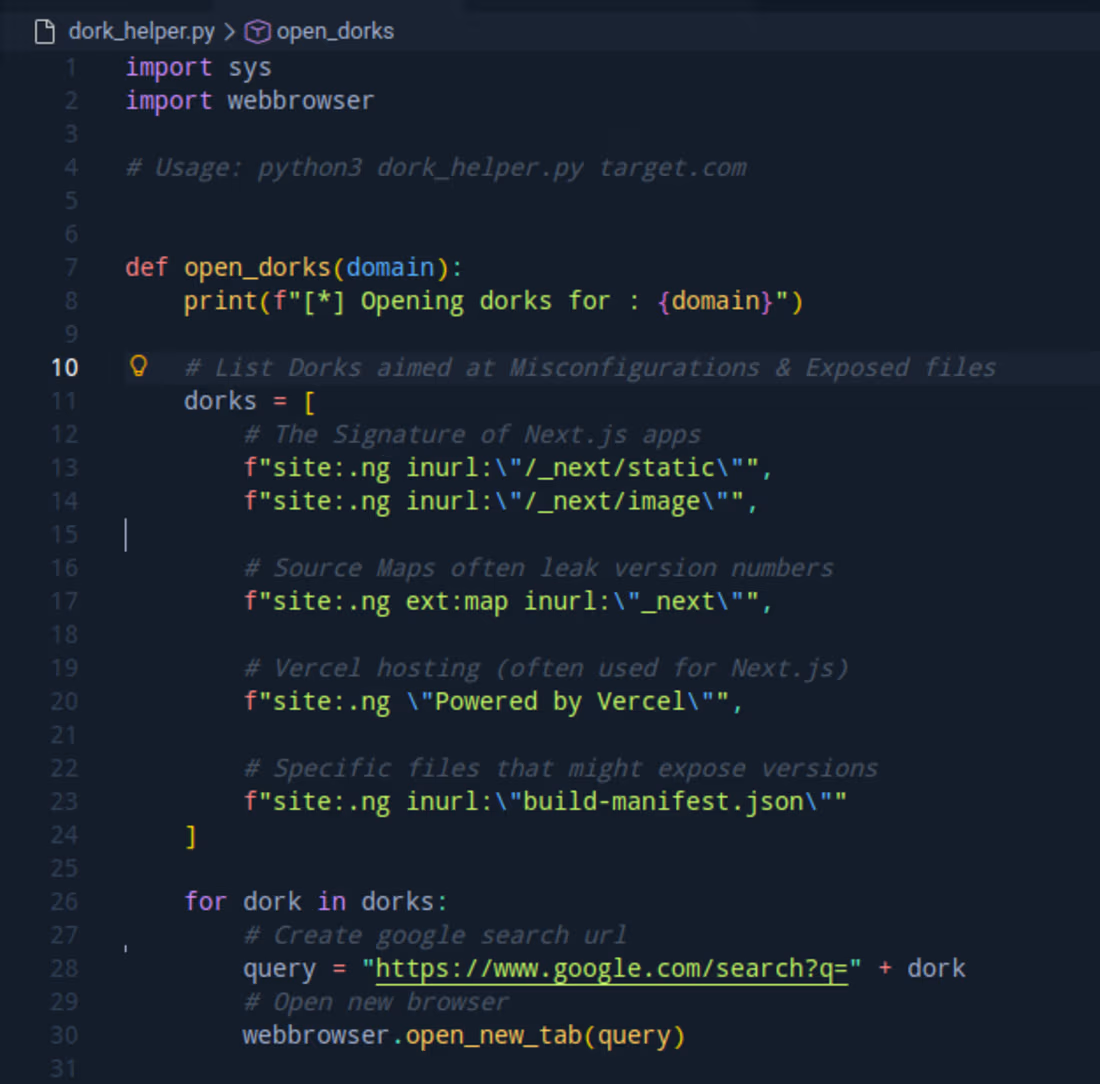
Custom OSINT Automation Tool (Python)
I developed a custom Python utility to automate the reconnaissance phase of security assessments.
Problem: Manual Google Dorking and server status checking consumes valuable time during an audit.
Solution: I wrote a Python script utilizing urllib and webbrowser modules to:
Automate complex Google Dork queries for finding exposed environment files and admin panels.
Batch-process server status checks (HTTP 200/403/404) to identify live targets instantly.
Outcome: Reduced reconnaissance time by 90% for large-scope targets.
2
13