Web Security Audit for E-commerce Website
External pen tests. They help you find security flaws that can be accessed from the public internet.
Internal pen tests. They help you understand weaknesses that employees or other insiders could exploit.
Blind pen tests. This kind of test can help you understand how easy it is for hackers to learn about your systems.
Double-blind pen tests. They can help you gauge your teams ability to handle a real hacking attempt.
Cybersecurity professional with a strong interest in Ethical Hacking, Web Application Penetration Testing, Vulnerability Analysis. Secure a responsible career opportunity to fully utilize my training and skills, while making a significant contribution to the success of the project
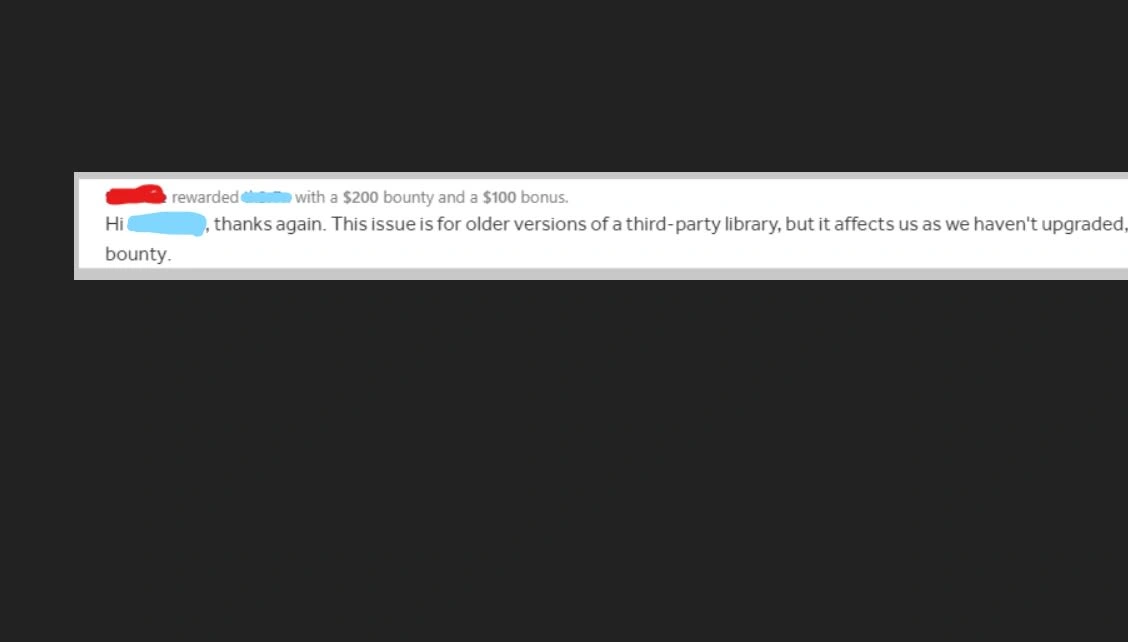
Rewarded $300 for identifying a vulnerability in OmniAuth Oauth library to a private organization in HackerOne which was assigned as CVE-2020-36599
Reported an Information Disclosure vulnerability to the same private organization on HackerOne
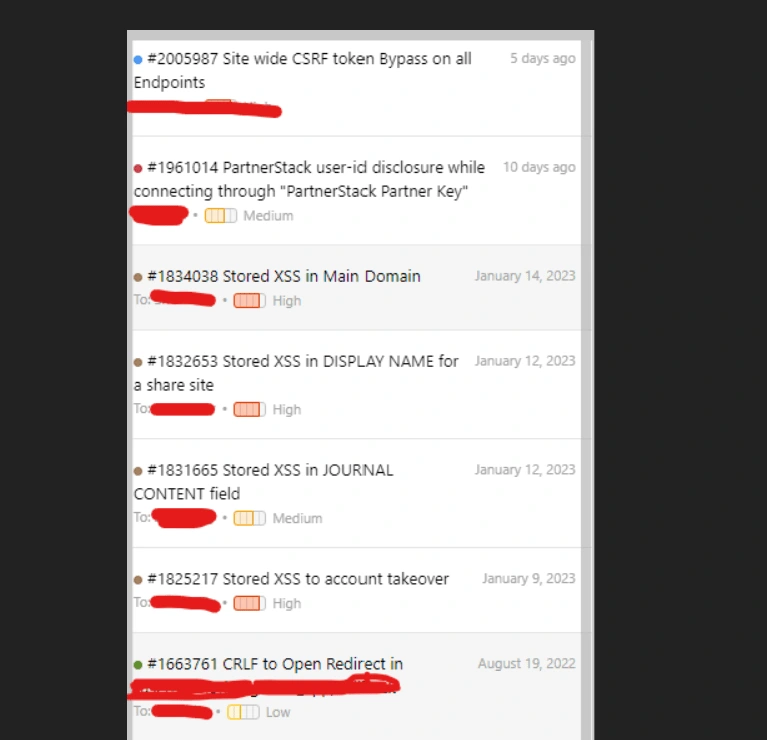
Researched multiple Stores XSS to a private program in HackerOne that impacted user accounts to get compromised
Participated in a Capture The Flag conducted by NAHAMSEC on 14.03.2021 and scored 1302 rank among 6491 players
Services:
Remarkable experience in manual penetration and Web application testing. Profound knowledge of network architectures, operating systems, application software and cyber security tools. Huge knowledge of managing information assurance evaluation tests. Solid understanding of information security and applied cryptographic protocols. Proficiency in scripting, Unix operating systems and windows. Ability to exploit recognized vulnerabilities.
Like this project
Posted Jun 7, 2023
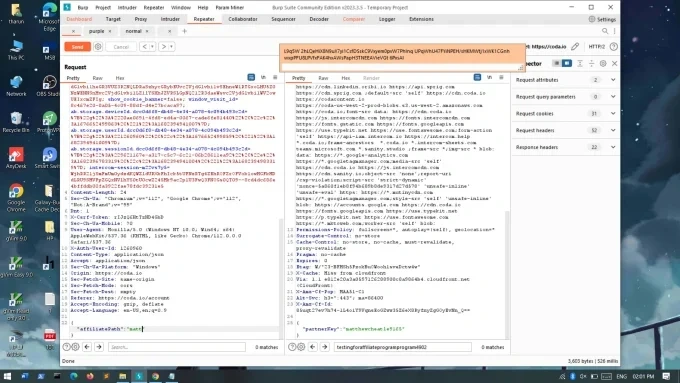
Performed a comprehensive security audit on an e-commerce website, identifying and reporting several critical vulnerabilities and providing recommendations for remediation.
Likes
0
Views
5


