Blockchain Attacks and Security

Blockchain Attacks and Security
Dec 15, 2023

One of the most widespread misconceptions about blockchain technology is that it is impervious to attacks. This notion is completely false as different kind of attacks can occur with Blockchain technology.
Suppose you are following the latest development in the realm of blockchain technology. In that case, you must have heard about the attack on the Ledger Connect Kit Library, which Ledger confirmed to be a phishing scam that resulted in the loss of nearly $484,000 in assets (according to blockchain analysis platform Lookonchain).
Another prominent example is the theft of $8 million worth of SOL by an attacker using an exploit on the widely used Solana mobile wallet Slope. Because this wallet was so popular, it was believed that the Solana blockchain was compromised.
In this article, I will be discussing blockchain attacks and blockchain security. It’s going to be interesting and impactful.
Understanding Blockchain Attacks
Blockchain attacks can be referred to as various Attempts to breach or alter a blockchain network. The technology known as the blockchain, which powers digital currencies such as Bitcoin and Ethereum, was built to be safe and impervious to any alteration. But there are still possible weak points and ways attacks can come in.
Every layer of blockchain technology is vulnerable to attack. Every layer possesses distinct technical constraints that can be leveraged to execute attacks that could result in system manipulation or harm.
Hackers have always targeted cryptocurrency exchanges, which are centralized marketplaces where consumers trade virtual assets. Among the most popular incidents is the 2014 Mt. Gox hack, in which about 850,000 bitcoins were stolen.
Type of Blockchain Attacks
51% attacks

The 51% attack is a blockchain attack in which an organized group of miners gains control over more than 50% of the network’s hashing power which is the processing power needed to solve the cryptographic puzzle.
The attackers would be able to stop payments between some or all users by stopping new transactions from receiving confirmations.
In addition, transactions that were executed while they were in charge could be cancelled. One of the problems that consensus systems like proof-of-work were built to prevent is the ability to double-spend coins through the reversal of transactions.
A 51% attack on a cryptocurrency with a high participation rate is an extremely tough and demanding task. Most of the time, the group of attackers would have to seize the required 51% of the blockchain and have developed a backup blockchain that they could introduce when needed. One of the most important things that prevent a 51% attack from happening is the cost of doing it.
34% Attack
This attack is comparable to 51% because it also aims to gain complete control over block mining by controlling 34% of the Blockchain’s mining power. The major difference between the 34% and 51% attacks is that the 34% attack only targets Blockchains that employ the Tangle consensus mechanism, such as the IOTA Blockchain.
Race Attack
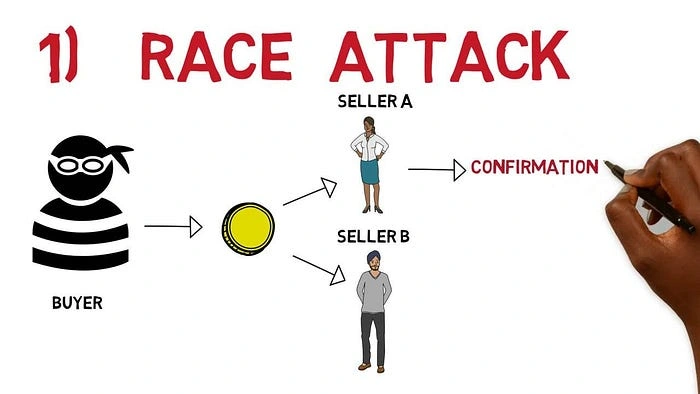
Race attacks do occur when there is an acceptance of an unconfirmed transaction. The attacker carries out two transactions simultaneously in this type of attack.
One transaction is to pay for a purchase from account A to a merchant, and another transaction at a higher cost is to move all the money from account A to account B ( another account under the attacker’s control).
Finney Attack

This type of attack was first explained by Mr Hal Finney who happened to be the first blockchain user to receive a bitcoin.
Finney attack takes place when a Blockchain user acknowledges a transaction that hasn’t been verified yet (added to a block). The concept here is that an attacker having two accounts A and B transfers all of the money from A to B. Then, instead of sending this transaction to the Blockchain network, he adds it to a valid block that he mines.
The attacker then uses account A to make a purchase from a Blockchain user, and before the transaction is added to the Blockchain, he receives his order. Afterwards, the attacker updates the network with the initial block that was mined.
Sybil Attack

Blockchain technologies were not yet in existence when the Sybil attack was created. The 1973 novel Sybil, which follows a lady with dissociative identity disorder, served as the inspiration for the attack’s nickname.
A Sybil attack happens when a malicious attacker aims to take control of numerous nodes by attacking the peer-to-peer layer of the network. A single unit can try to take control of a network by assuming several identities, posing a threat to any online system.
DDOS Attack

A DDOS (distributed denial of server) attack happens when the blockchain network is unable to add new transactions provided by its clients for a while into newly generated blocks.
When a fake transaction is fulfilled by the mempool, all subsequent transactions are dropped, which causes a DOS. If multiple exploits of a DOS vulnerability are carried out in the Blockchain client software, which nodes use to connect with users or each other, it may also result in a DOS attack.
Blockchain ecosystem vulnerabilities
An ecosystem attack can target a blockchain with fewer nodes than one with a larger, more evenly dispersed network. It is hard to carry out Sybil attacks or 51% attacks on blockchains such as Bitcoin or Ethereum because of the amount of computational power or assets needed.
However, it is important to be aware of the whole range of risks, particularly if your company is thinking of creating its blockchain or utilizing one of the smaller, emerging blockchains.
Routing Attack
The purpose of this attack is to attempt to divide the Blockchain network into two separate Blockchains by making use of network routing attacks. There will be two distinct chains with distinct transactions as a result of this attack. All of the transactions carried out in the smallest chain will be destroyed after the attack.
Thus, even if the transaction has already been verified and confirmed using six blocks, the transaction will still be denied. But as the network expands, it becomes harder to carry out this attack.
Smart contract vulnerability exploitation
The final layer of the blockchain is made up of smart contracts. These are perpetually running applications that carry out the business logic.
Consequently, those applications are typically deployed with serious vulnerabilities that can be exploited because their development technique is still in its infancy when compared to traditional application technologies.
As conventional apps, some vulnerabilities don’t do any harm. Others are crucial and can cause significant losses for the company. The ease of exploitation of this type of attack is what makes it much more dangerous.
Typically, attackers can take advantage of them without requiring a thorough understanding of smart contract drafting. With the correct parameters, a straightforward transaction might easily result in the vulnerability being successfully exploited.
Eclipse attack

An Eclipse attack is another network-based Blockchain attack which aims to prevent a node or group of nodes from interacting with one another to disrupt the peer-to-peer infrastructure. Only blockchains with bandwidth limitations that obstruct communication between all nodes are vulnerable to the Eclipse attack.
Once infiltrated, the hacker just needs to operate on a limited number of nodes that are connected to the compromised node. The malicious nodes will be able to alter the information that the targeted nodes receive from the network by carrying out this attack.
Blockchain Security

Blockchain security is the application of best practices, technologies, and cybersecurity principles to reduce risk and prevent unauthorized access and harmful attacks on blockchain networks.
Although distributed ledger technology (DLT) powers all blockchains, not all of them are equally safe or functionally sound. Due to the open and closed nature of their networks, public and private blockchains have fundamentally distinct security models, even though each has its benefits and limitations.
Public blockchain security
Public blockchains such as Ethereum and Bitcoin are open networks that anybody may join and take part in transaction validation. Public blockchains such as Ethereum and Bitcoin use an open-source code base.
This indicates that it is made available to the general public and is regularly checked for errors, vulnerabilities, and other problems by a community of developers.
Through the utilization of the combined knowledge of open-source communities, these blockchains’ security, functionality, and effectiveness are constantly assessed and enhanced. Malicious organizations and hackers are also constantly scanning the code for weaknesses they may attack.
Every user on the network has overall responsibility for maintaining the security of a public blockchain such as Ethereum. This comprises the thousands of developers who write the code as well as the validators and node operators who keep the network running.
A public blockchain is resistant to numerous kinds of attacks because it is a decentralized system, meaning that no single party can take full responsibility for its security.
Private blockchain security
Private blockchains are centralized networks that are exclusive and have restricted access. Their resilience to some external threats may be strengthened by this centralized control. The operational organization bears exclusive responsibility for safeguarding a private blockchain.
Because these blockchains are centralized, there is only one point of failure, so the organization must put robust security measures in place.
What security measures are in place for blockchain transactions?
Cryptocurrency transactions are push transactions that are initiated peer-to-peer and don’t require a third party. Blockchain network users manage their digital assets on the network by using private keys which are a cryptographically secure means of access and authentication.
Crypto demands thoughtfulness. When sending currency on-chain, personal accountability increases significantly because no third party is needed. Once a transaction is validated on the blockchain, it cannot be reversed. This makes getting lost or stolen money back extremely difficult.
Conclusion
Though the nature of decentralization has certain obstacles of its own, the rapid emergence of decentralized technologies has spurred innovative achievements. Every organization will soon need a blockchain security plan to protect its operations.
With blockchain, each user is responsible for preserving the system’s integrity. This technology, which powers well-known cryptocurrencies like ether and bitcoin, has tremendous prospects for the development of digital transactions in the future and beyond.
However, this attacks shouldn’t discourage potential users if they have the desire to incorporate cryptocurrencies into their daily lives. By putting security into practice, one can greatly increase their cryptocurrency safety and deter attackers from targeting more vulnerable individuals.
Like this project
Posted May 28, 2025
Article discussing blockchain attacks and security measures.
Likes
0
Views
3
Timeline
Dec 10, 2013 - Dec 15, 2023






