Cybersecurity Blog post
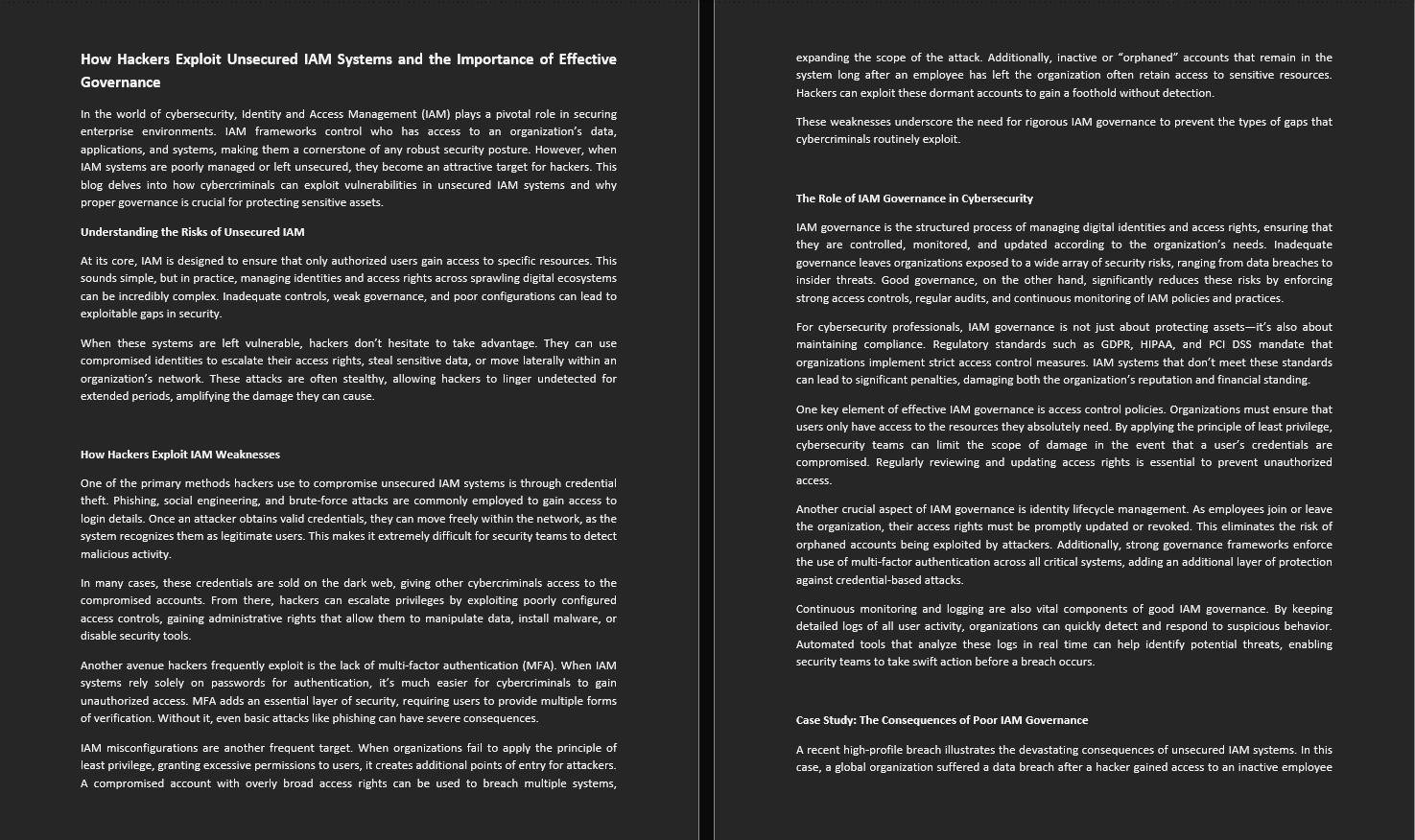
I was hired to ghostwrite a blogpost for a Cybersecurity company's blog on "How Hackers Exploit Unsecured IAM Systems and the Importance of Effective IAM Governance" and like always I came through again....
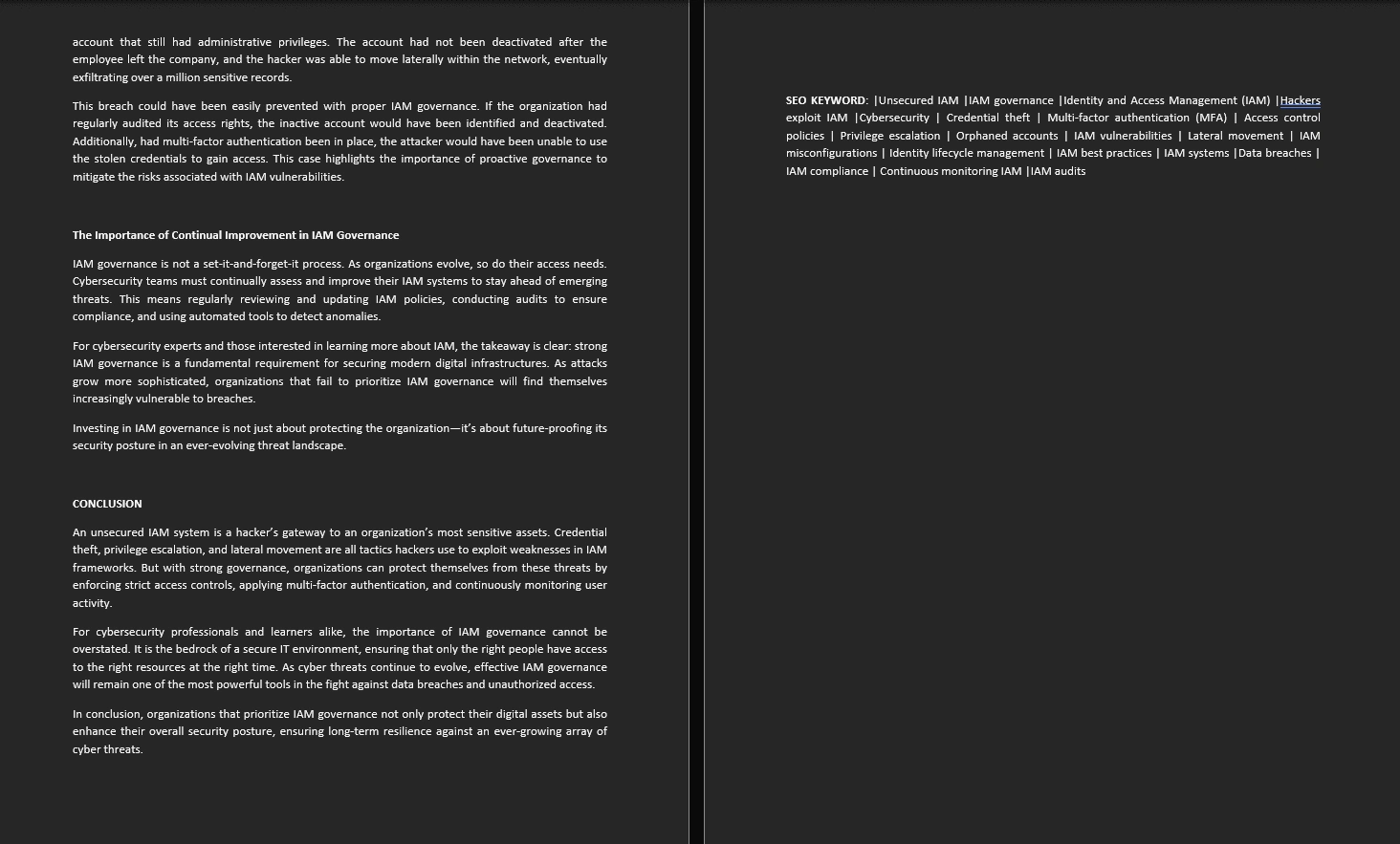
The Concluding Part of the Blogpost
Here is the Testimony of the Client....
Great working with him
Like this project
Posted Mar 27, 2025
This is a Cybersecurity Blog post on How Hackers Exploit Unsecured IAM Systems and the Importance of Effective IAM governance.
Likes
0
Views
2




