WAF Bypass & XSS Discovery for E-Commerce Platform Conducted...
WAF Bypass & XSS Discovery for E-Commerce Platform
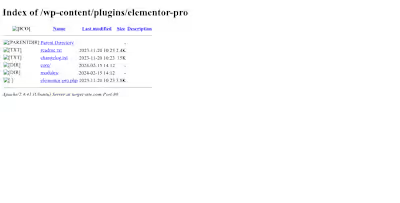
Conducted a black-box security assessment for a high-traffic e-commerce marketplace (10M+ users).
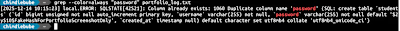
The Finding: Reflected Cross-Site Scripting (XSS) in the search functionality.
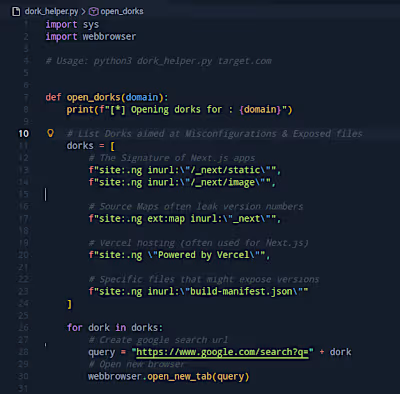
Technical Details: The application employed a Web Application Firewall (WAF) that stripped standard XSS vectors (parentheses). I successfully bypassed this filter using ES6 Template Literals (backticks) to execute JavaScript.
Impact: Reported a P2 Vulnerability that could allow account takeover via session cookie theft.
Status: Reported via Vulnerability Disclosure Program (VDP).
Like this project
Posted Dec 17, 2025
WAF Bypass & XSS Discovery for E-Commerce Platform Conducted a black-box security assessment for a high-traffic e-commerce marketplace (10M+ users). The Fin...
Likes
0
Views
0