Results that are similar to your search
Similar results
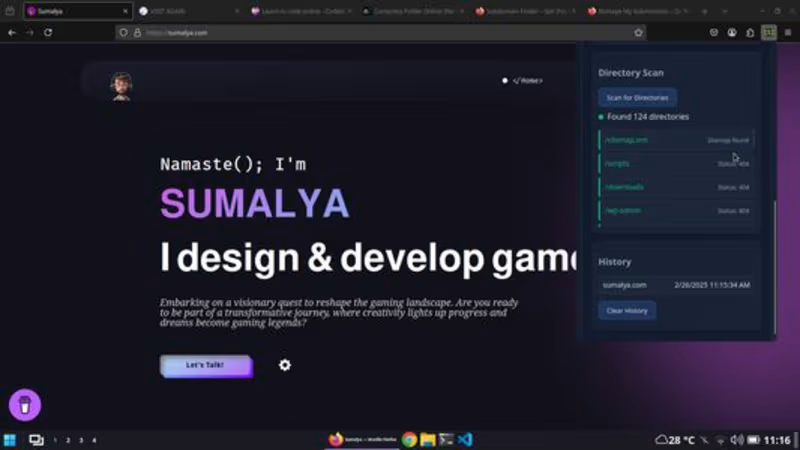
Cyber expert specialising in Azure Security Services.
- $5k+
- Earned
- 12x
- Hired
- 5.0
- Rating
- 13
- Followers
Cyber expert specialising in Azure Security Services.
B2B Websites for Complex Industrial & Defense Companies
Seasoned cybersecurity leader.
5 years of experience as a Software Engineer for startups.
New to Contra
5 years of experience as a Software Engineer for startups.
CyberSecurity expert
CyberSecurity expert
Cybersecurity| Robotics, Machine Learning & AI
Cybersecurity| Robotics, Machine Learning & AI
Expert Next.js Frontend Developer – Fast & Responsive
Web Security Analyst & OSINT Specialist