Securing Cloud Infrastructures Muhammed Ali
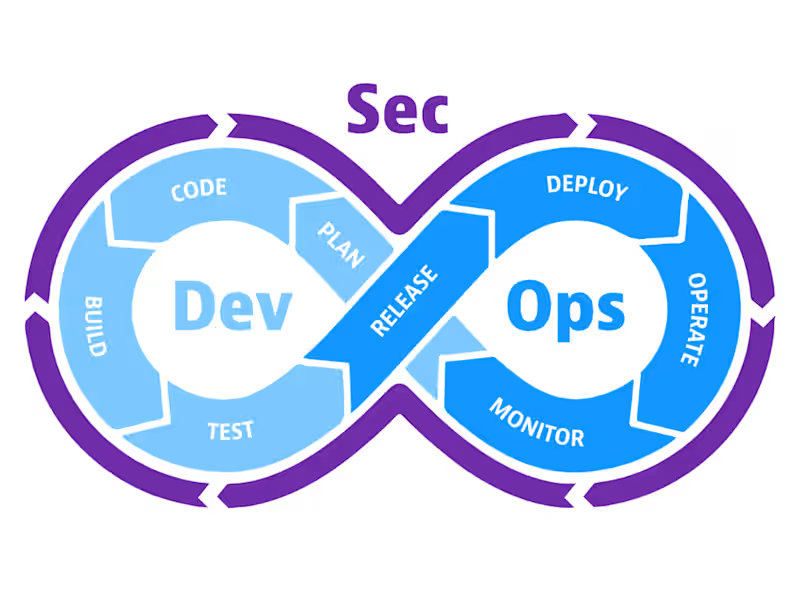
A cloud security project involves assessing and enhancing the security posture of cloud environments by implementing robust security policies, practices, and technologies. This includes securing CI/CD pipelines, managing Identity and Access Management (IAM), configuring encryption for data at rest and in transit, and deploying monitoring and alerting systems to detect and respond to threats. The project ensures compliance with industry standards and regulations such as GDPR, HIPAA, or PCI DSS through audits and control mappings. It leverages tools like Infrastructure-as-Code (IaC) for secure and automated deployments across public, private, and hybrid clouds, embedding security into the entire lifecycle. The goal is to create a resilient, compliant, and scalable cloud infrastructure while fostering a culture of continuous security improvement.
Muhammed's other services
Starting at$40 /hr
Tags
AWS
Google Cloud Platform
Jenkins
Kubernetes
Terraform
Cloud Infrastructure Architect
Cloud Security Engineer
Security Engineer
Service provided by

Muhammed Ali Cairo, Egypt

Securing Cloud Infrastructures Muhammed Ali
Starting at$40 /hr
Tags
AWS
Google Cloud Platform
Jenkins
Kubernetes
Terraform
Cloud Infrastructure Architect
Cloud Security Engineer
Security Engineer
A cloud security project involves assessing and enhancing the security posture of cloud environments by implementing robust security policies, practices, and technologies. This includes securing CI/CD pipelines, managing Identity and Access Management (IAM), configuring encryption for data at rest and in transit, and deploying monitoring and alerting systems to detect and respond to threats. The project ensures compliance with industry standards and regulations such as GDPR, HIPAA, or PCI DSS through audits and control mappings. It leverages tools like Infrastructure-as-Code (IaC) for secure and automated deployments across public, private, and hybrid clouds, embedding security into the entire lifecycle. The goal is to create a resilient, compliant, and scalable cloud infrastructure while fostering a culture of continuous security improvement.
Muhammed's other services
$40 /hr