DevSecOps Implementation Muhammed Ali
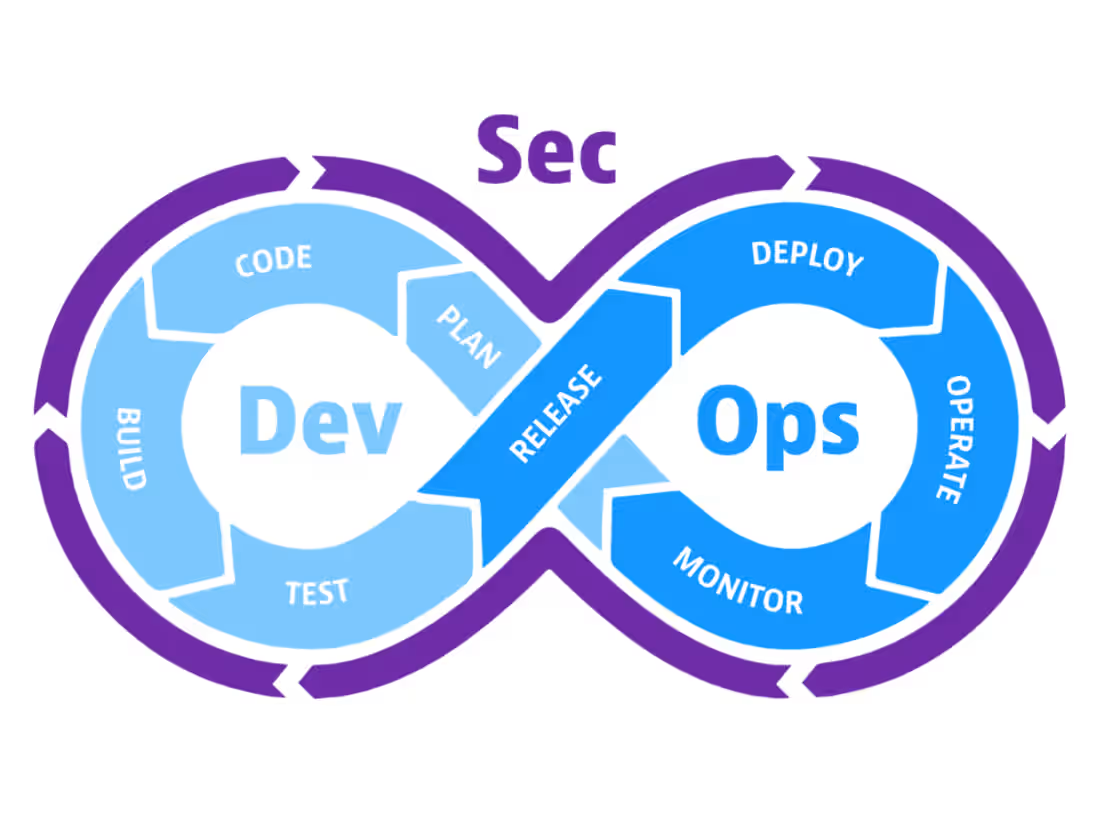
A DevSecOps implementation project integrates security practices into the software development lifecycle, ensuring that security is embedded at every stage of the CI/CD pipeline. The project involves automating security testing (SAST, DAST, SCA), managing secrets, and ensuring continuous compliance through automated tools. By shifting security left, vulnerabilities are detected and remediated earlier in the development process, enhancing both speed and security. The project also establishes continuous monitoring for real-time threat detection, ensuring that security risks are identified and addressed promptly.
Muhammed's other services
Starting at$40 /hr
Tags
AWS
Google Cloud Platform
Jenkins
Kubernetes
Terraform
Cloud Security Engineer
Cybersecurity Specialist
DevOps Engineer
Service provided by

Muhammed Ali Cairo, Egypt

DevSecOps Implementation Muhammed Ali
Starting at$40 /hr
Tags
AWS
Google Cloud Platform
Jenkins
Kubernetes
Terraform
Cloud Security Engineer
Cybersecurity Specialist
DevOps Engineer
A DevSecOps implementation project integrates security practices into the software development lifecycle, ensuring that security is embedded at every stage of the CI/CD pipeline. The project involves automating security testing (SAST, DAST, SCA), managing secrets, and ensuring continuous compliance through automated tools. By shifting security left, vulnerabilities are detected and remediated earlier in the development process, enhancing both speed and security. The project also establishes continuous monitoring for real-time threat detection, ensuring that security risks are identified and addressed promptly.
Muhammed's other services
$40 /hr