Penetration TestingDimitris Pallis
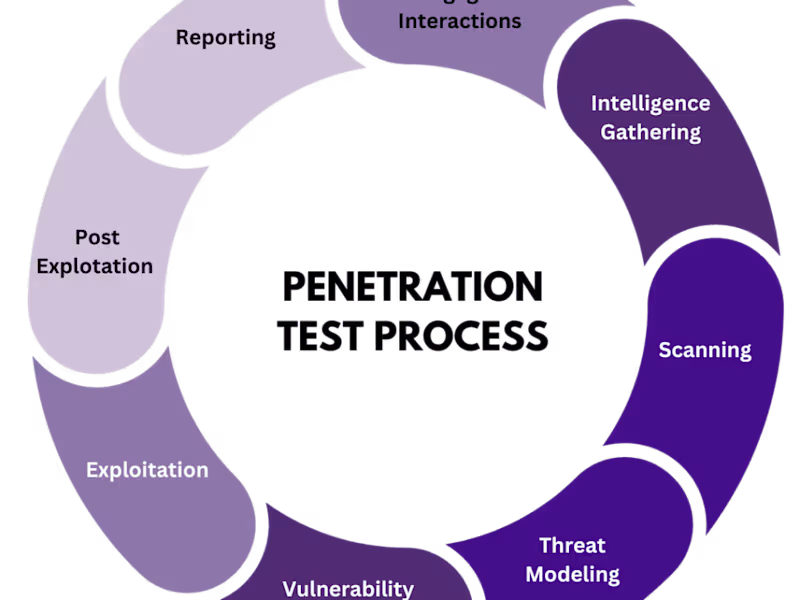
Penetration testing is a simulated cyber attack conducted by security professionals (like pentesters) to identify and exploit vulnerabilities in a system so that they can detect the security weaknesses before attackers do.
Dimitris's other services
Contact for pricing
Tags
Burp Suite
Docker
Kali Linux
Cloud Security Engineer
Security Engineer
Security Manager
Service provided by

Dimitris Pallis London, UK
- 5.00
- Rating

Penetration TestingDimitris Pallis
Contact for pricing
Tags
Burp Suite
Docker
Kali Linux
Cloud Security Engineer
Security Engineer
Security Manager
Penetration testing is a simulated cyber attack conducted by security professionals (like pentesters) to identify and exploit vulnerabilities in a system so that they can detect the security weaknesses before attackers do.
Dimitris's other services
Contact for pricing