Managed Detection & Response with Compliance and SOC IntegrationMashooque Ali
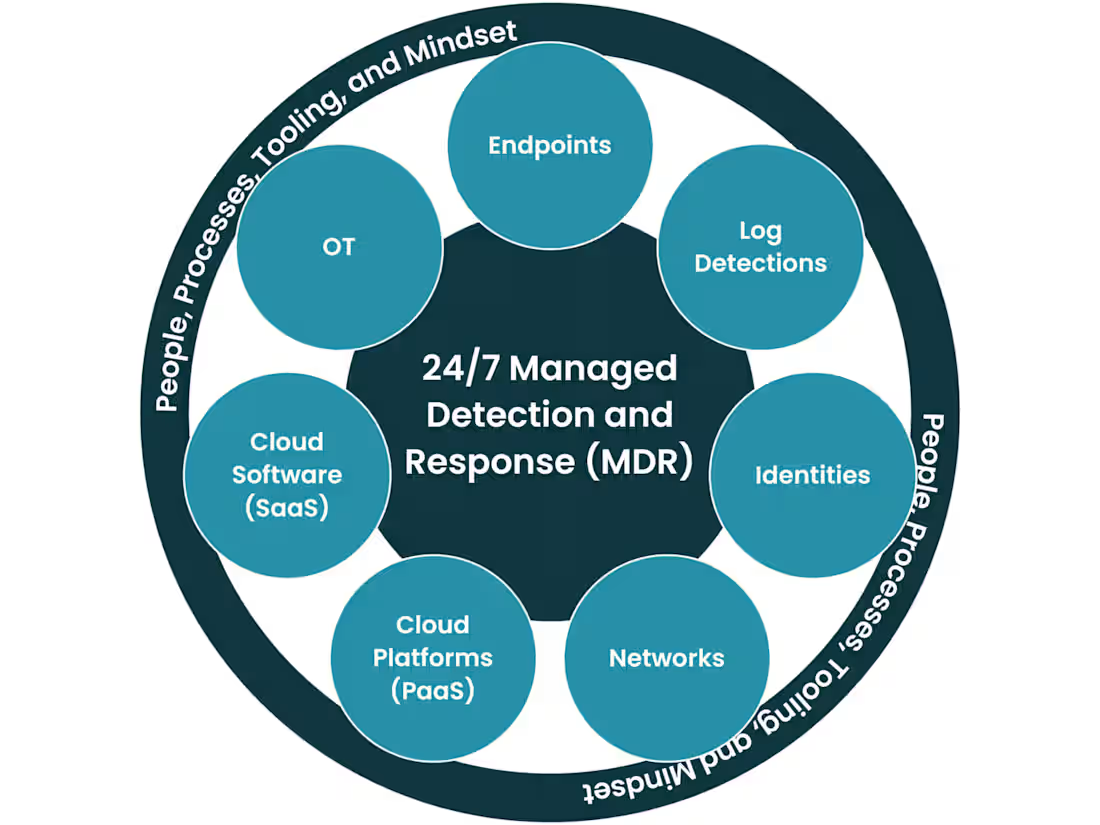
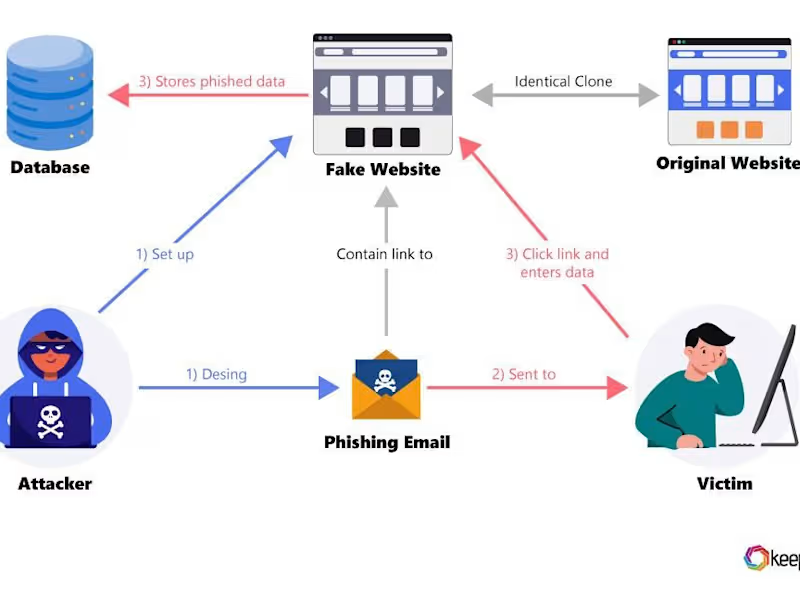
Deliver advanced threat detection, continuous monitoring, and rapid response to cyber incidents, while ensuring compliance with industry regulations and leveraging a 24/7 Security Operations Center (SOC). These enhanced services provide comprehensive security through SOC, threat intelligence, compliance auditing, and employee training, ensuring both security and regulatory compliance for the organization.
Mashooque's other services
Contact for pricing
Tags
AWS
Azure
Google Cloud Platform
Microsoft Intune
Cloud Security Engineer
Security Engineer
Security Manager
Service provided by

Mashooque Ali Sector X Lahore DHA, Pakistan

Managed Detection & Response with Compliance and SOC IntegrationMashooque Ali
Contact for pricing
Tags
AWS
Azure
Google Cloud Platform
Microsoft Intune
Cloud Security Engineer
Security Engineer
Security Manager
Deliver advanced threat detection, continuous monitoring, and rapid response to cyber incidents, while ensuring compliance with industry regulations and leveraging a 24/7 Security Operations Center (SOC). These enhanced services provide comprehensive security through SOC, threat intelligence, compliance auditing, and employee training, ensuring both security and regulatory compliance for the organization.
Mashooque's other services
Contact for pricing