Identity Attack Path Risk AssessmentWatheq Zboun
This engagement provides a deep, evidence-based assessment of identity and privilege escalation risks across your Microsoft Active Directory and Entra ID environment.
Using industry-grade attack path analysis techniques, I identify how an attacker could realistically escalate privileges, move laterally, and gain administrative control and provide a clear, prioritized roadmap to fix the highest-risk issues first.
This is a time-boxed, one-time assessment, designed for organizations that want clarity, not ongoing support contracts.
This assessment focuses on:
Privileged access paths
Identity trust relationships
Conditional Access weaknesses
Role assignment risks
Hybrid AD ↔ Entra attack surfaces
Instead of generic checklists, you receive visual attack paths, concrete findings, and actionable remediation guidance mapped to real-world attacker behavior.
What's included
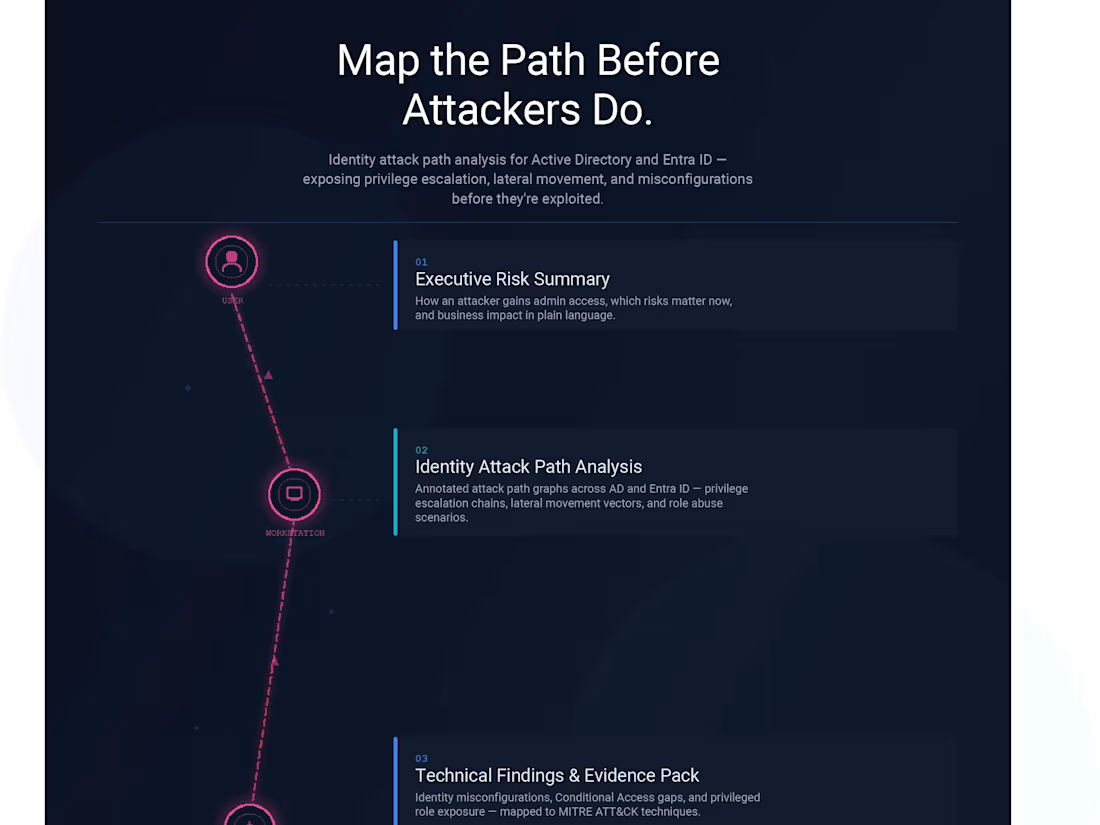
Executive Risk Summary (non-technical)
-How an attacker can realistically gain admin access
-Which risks matter most right now
-Business and operational impact explained in plain language
Identity Attack Path Analysis (Core Deliverable)
-Annotated attack path graphs (on-prem AD and/or Entra ID)
-Privilege escalation chains
-Lateral movement vectors
-Role and permission abuse scenarios
Technical Findings & Evidence Pack
Identity and access misconfigurations
Conditional Access gaps
-Privileged role exposure
--Findings mapped to MITRE ATT&CK techniques
Prioritized Remediation Roadmap
-Quick wins (30-day fixes)
-Medium-term structural improvements
-Long-term identity hardening recommendations
-Clear separation of “must fix” vs “nice to have"
Identity Attack Surface Baseline Snapshot
-A point-in-time baseline of your identity security posture
-Serves as a reference for future reassessments or audits
-Enables you to measure improvement after remediation
Final Report & Walkthrough Session
-Professional written report (PDF)
- findings walkthrough
- Q&A and prioritization discussion
FAQs
IAM is a framework of policies and technologies that ensures the right individuals have appropriate access to technology resources, enhancing security and operational efficiency.
IAM helps protect sensitive data, ensures compliance with regulatory requirements, and streamlines user access management, reducing the risk of unauthorized access.
I implement solutions such as Azure Active Directory (Azure AD), Multi-Factor Authentication (MFA), Single Sign-On (SSO), and role-based access control (RBAC).
The timeline varies based on the size and complexity of your organization, but typically ranges from a few weeks to a few months.
Yes, I design IAM solutions that integrate seamlessly with your existing IT infrastructure and applications.
I provide ongoing support, including troubleshooting, maintenance, and regular security reviews to ensure your IAM system remains effective and up-to-date.
I implement compliance controls and auditing mechanisms, and regularly review and update IAM policies to meet regulatory requirements.
Watheq's other services
Contact for pricing
Tags
AWS
Azure
Google Cloud Platform
Microsoft Office 365
Cloud Infrastructure Architect
Cloud Security Engineer
IT Specialist
Service provided by

Watheq Zboun
max
United States- $5k+
- Earned
- 1
- Paid projects
- 5.00
- Rating
- 8
- Followers

Identity Attack Path Risk AssessmentWatheq Zboun
Contact for pricing
Tags
AWS
Azure
Google Cloud Platform
Microsoft Office 365
Cloud Infrastructure Architect
Cloud Security Engineer
IT Specialist
This engagement provides a deep, evidence-based assessment of identity and privilege escalation risks across your Microsoft Active Directory and Entra ID environment.
Using industry-grade attack path analysis techniques, I identify how an attacker could realistically escalate privileges, move laterally, and gain administrative control and provide a clear, prioritized roadmap to fix the highest-risk issues first.
This is a time-boxed, one-time assessment, designed for organizations that want clarity, not ongoing support contracts.
This assessment focuses on:
Privileged access paths
Identity trust relationships
Conditional Access weaknesses
Role assignment risks
Hybrid AD ↔ Entra attack surfaces
Instead of generic checklists, you receive visual attack paths, concrete findings, and actionable remediation guidance mapped to real-world attacker behavior.
What's included
Executive Risk Summary (non-technical)
-How an attacker can realistically gain admin access
-Which risks matter most right now
-Business and operational impact explained in plain language
Identity Attack Path Analysis (Core Deliverable)
-Annotated attack path graphs (on-prem AD and/or Entra ID)
-Privilege escalation chains
-Lateral movement vectors
-Role and permission abuse scenarios
Technical Findings & Evidence Pack
Identity and access misconfigurations
Conditional Access gaps
-Privileged role exposure
--Findings mapped to MITRE ATT&CK techniques
Prioritized Remediation Roadmap
-Quick wins (30-day fixes)
-Medium-term structural improvements
-Long-term identity hardening recommendations
-Clear separation of “must fix” vs “nice to have"
Identity Attack Surface Baseline Snapshot
-A point-in-time baseline of your identity security posture
-Serves as a reference for future reassessments or audits
-Enables you to measure improvement after remediation
Final Report & Walkthrough Session
-Professional written report (PDF)
- findings walkthrough
- Q&A and prioritization discussion
FAQs
IAM is a framework of policies and technologies that ensures the right individuals have appropriate access to technology resources, enhancing security and operational efficiency.
IAM helps protect sensitive data, ensures compliance with regulatory requirements, and streamlines user access management, reducing the risk of unauthorized access.
I implement solutions such as Azure Active Directory (Azure AD), Multi-Factor Authentication (MFA), Single Sign-On (SSO), and role-based access control (RBAC).
The timeline varies based on the size and complexity of your organization, but typically ranges from a few weeks to a few months.
Yes, I design IAM solutions that integrate seamlessly with your existing IT infrastructure and applications.
I provide ongoing support, including troubleshooting, maintenance, and regular security reviews to ensure your IAM system remains effective and up-to-date.
I implement compliance controls and auditing mechanisms, and regularly review and update IAM policies to meet regulatory requirements.
Watheq's other services
Contact for pricing