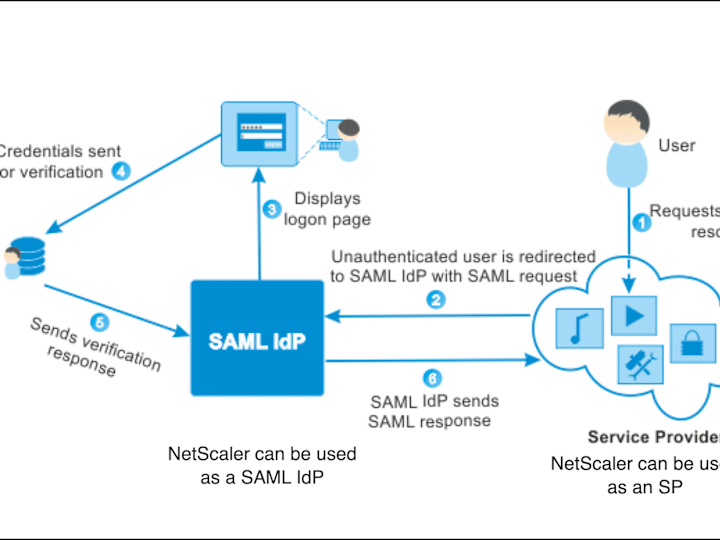
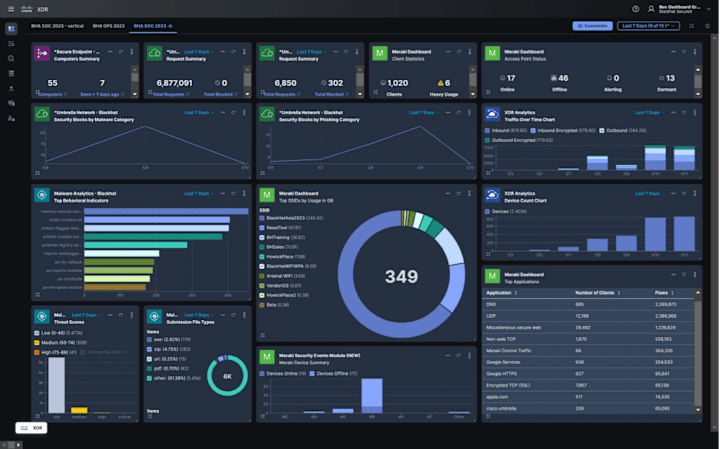
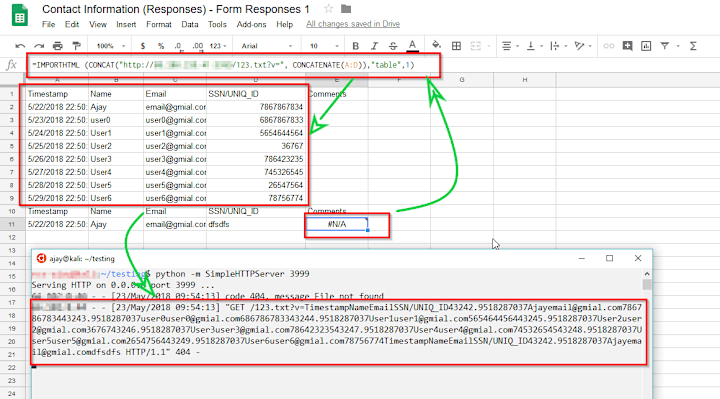
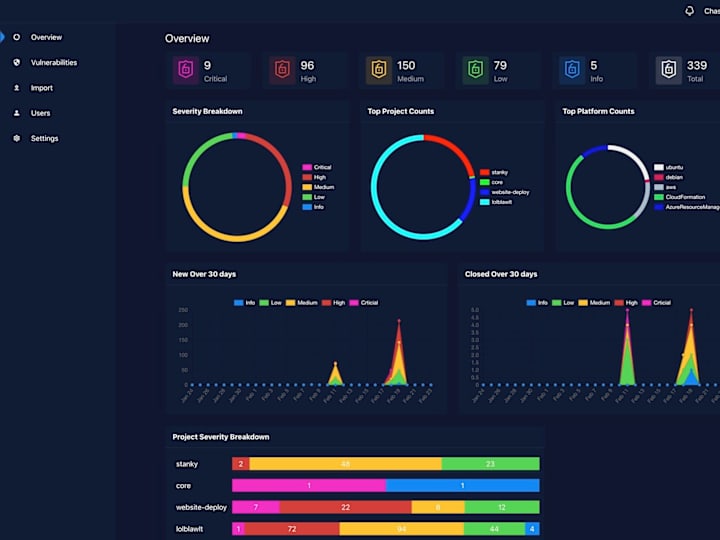
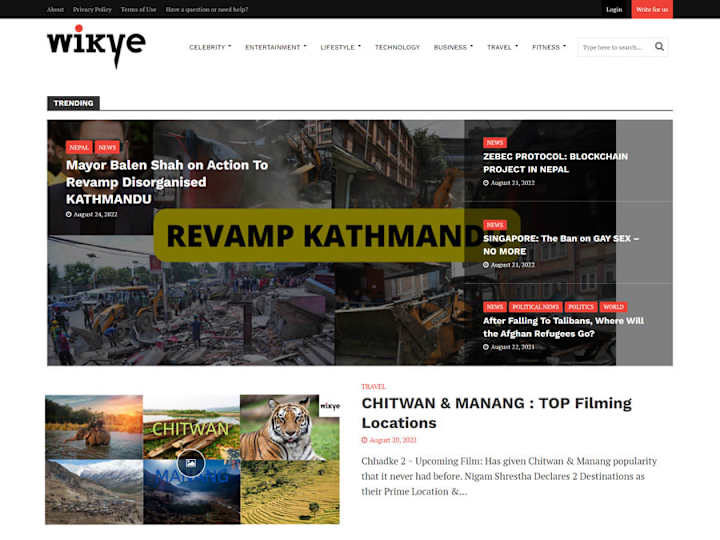
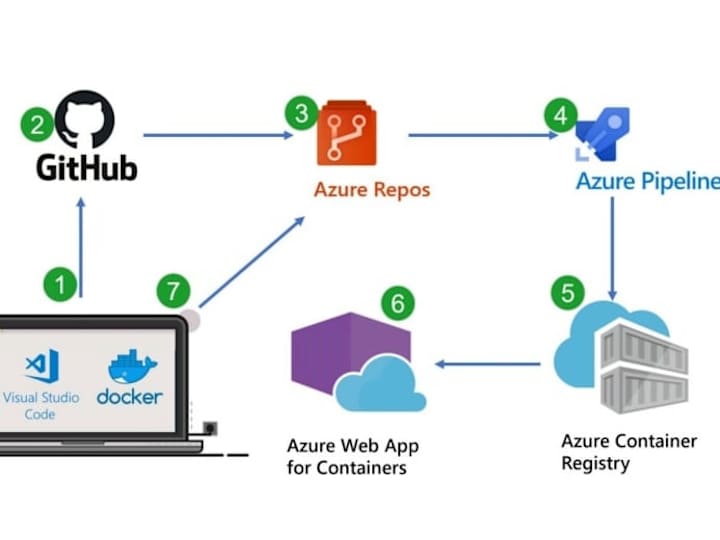
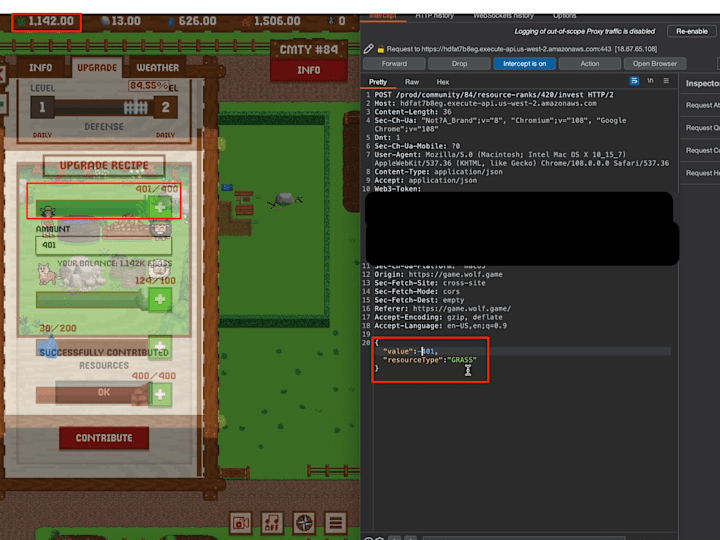
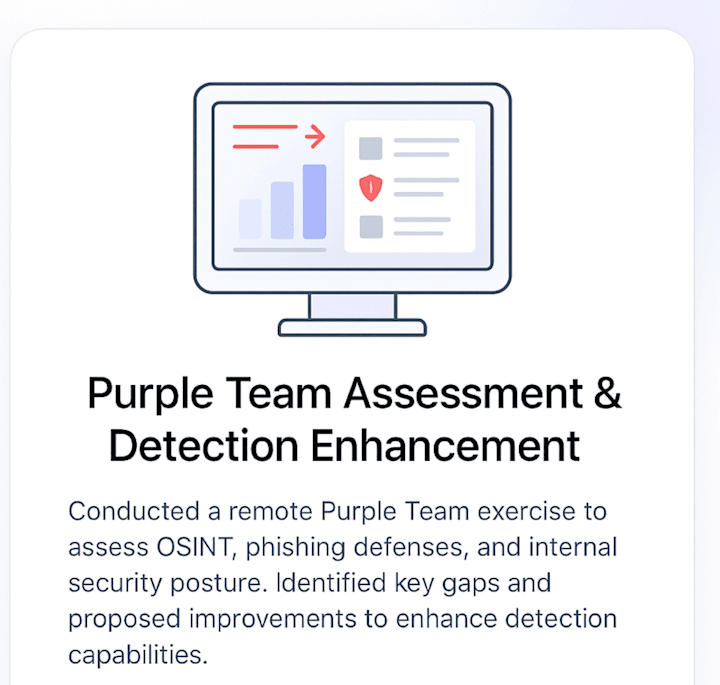
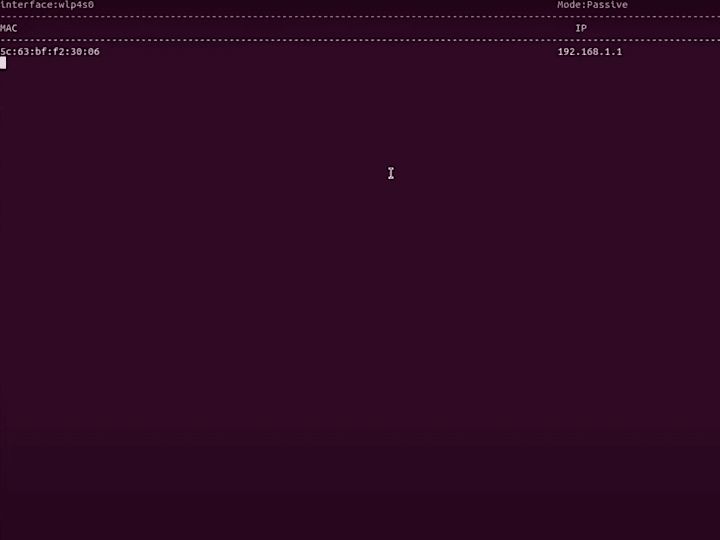
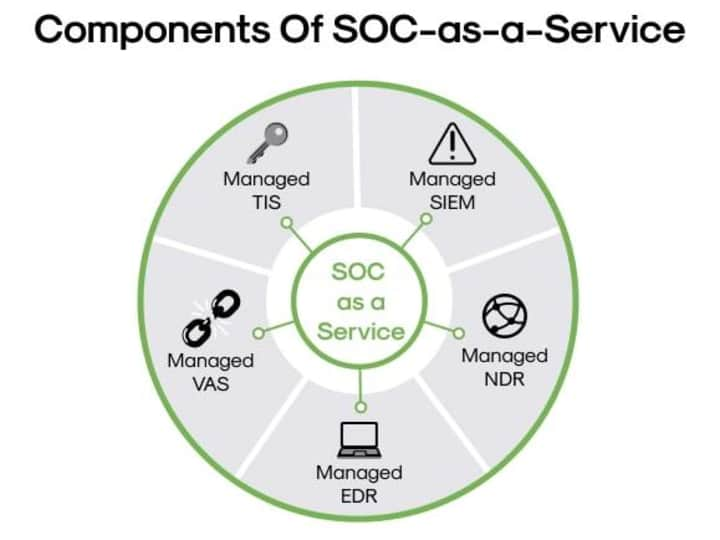
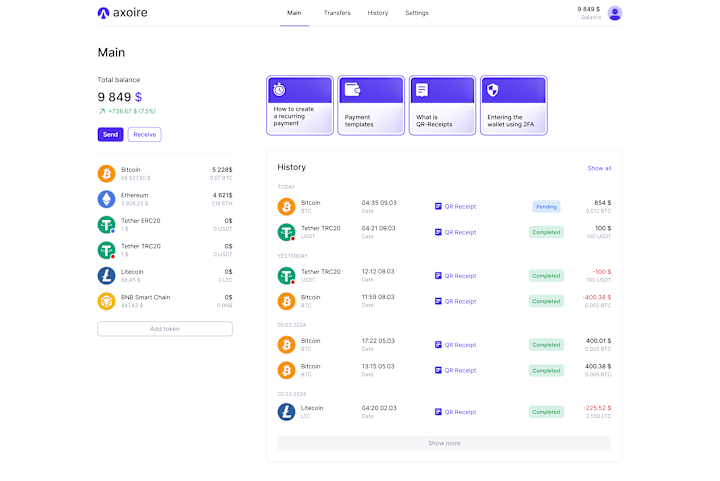
0
4
0
3
0
10
0
9
0
29
0
2
0
5
0
4
0
12
0
2
0
0
0
20
0
21
0
14
0
2
0
0
0
5
1
0
0
4
0
0
0
4
0
1
0
0
0
1
0
10
0
5
0
9
0
5
0
64
0
7
0
0
0
1
0
0
0
38
0
3
0
5
0
17
0
13
0
9
1
5
0
2
0
75
0
18
0
0
0
7
0
1
0
0
0
4
0
1
1
0
0
0
0
93
0
1
0
0
0
1
0
2
0
5
0
5
0
3
0
3
0
4
0
21
0
18
0
24
0
3
0
1
0
9
0
2
0
2
0
0
0
0
0
7
0
40
0
2
0
9
0
3
1
6
0
2
0
1
0
1
0
5
0
3
0
4
1
1
0
4
0
3
0
25
0
7
0
11
0
7
0
0
0
1
0
24
0
1
0
6
0
0
0
9
0
3
0
1
0
4